Posey's Tips & Tricks
How To Grade Your Organization's Office 365 Security Level
Cyber threats are a major problem in today's world and Office 365 has become a big target for hackers. Because Office 365 presumably contains some of your organization's most sensitive data, it is really important to keep it secure.
The good news is that Microsoft handles many of the security tasks for you. You will never have to apply a patch to Office 365 or create a firewall rule on the Office 365 servers, for example.
At the same time, though, Microsoft does give subscribers a fair amount of control over their Office 365 applications. Some of the decisions that you make as an administrator can either strengthen or weaken your security.
As a way of making it easier to keep Office 365 secure, Microsoft generates a security score that is based around your configuration. Think of it as a security report card (yes, I used to hate report card day, too).
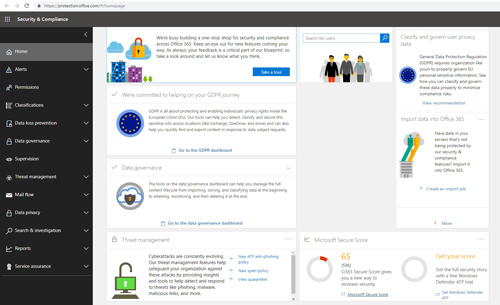
You can see your security and compliance score by going into the Security and Compliance Center, and then scrolling down toward the bottom of the screen. You can see what the security score looks like in Figure 1.
 [Click on image for larger view.] Figure 1: This is how Microsoft presents security scores.
[Click on image for larger view.] Figure 1: This is how Microsoft presents security scores.
In some cases, you may end up seeing a message saying that Office could not display the security score (I can't remember the exact wording of this message). If that happens, don't worry about it too much. It can take awhile for Office 365 to accumulate enough data to be able to generate a security score. Just check back in a week or two, and the score should be there.
As you look at the figure above, you can see that my security configuration has earned 65 out of 596 points. If this really was a report card, it would be a failing score. This Office 365 instance only received about 11 percent of the points! The reason for my terrible security score is that the screen capture was taken from a developer account (not my primary Office 365 account) and the configuration is pretty much wide-open.
So where does the security score come from? If you click on the Microsoft Security Score link shown at the bottom of the previous figure, you are taken into the Secure Score portal. This portal is made up of two separate tabs. The Dashboard tab is shown by default. The upper portion of this tab rehashes your score. Things become more interesting when you scroll down a bit.
As you can see in Figure 2, the dashboard contains a slide bar that you can use to set your target score. Beneath that is a list of action items that you can perform in order to achieve the target score. In my case, for instance, Microsoft recommends that I do things such as requiring multifactor authentication and turning on auditing data.
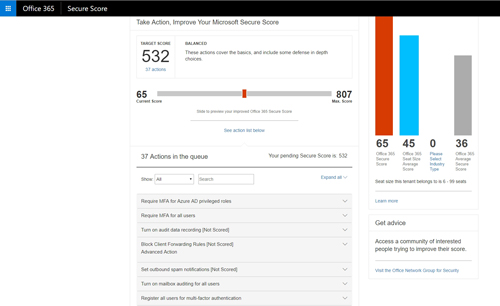 [Click on image for larger view.] Figure 2: Microsoft tells you how to achieve your target security score.
[Click on image for larger view.] Figure 2: Microsoft tells you how to achieve your target security score.
As you look at the figure above, you will notice that there is a down arrow icon displayed next to each of the action items. Clicking on this arrow reveals information about why Microsoft recommends that particular action. There are also buttons that you can click to learn more, ignore the recommendation or to indicate that the action is being performed with third-party tools. You can see what this looks like in Figure 3.
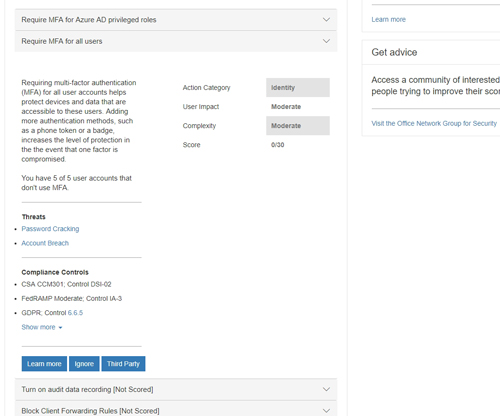 [Click on image for larger view.] Figure 3: Microsoft provides information about each recommendation.
[Click on image for larger view.] Figure 3: Microsoft provides information about each recommendation.
The Score Analyzer tab provides a nice graphic showing you how your security score has changed over time. This can help you track your progress and spot any administrative actions that might have weakened your security. You can see what this chart looks like in Figure 4. As you can see in the figure, you have the option of adjusting the reporting period, comparing scores or even exporting the data.
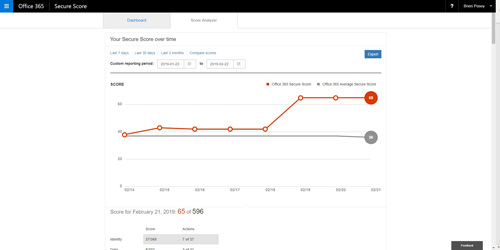 [Click on image for larger view.] Figure 4: This is what the Score Analyzer tab looks like.
[Click on image for larger view.] Figure 4: This is what the Score Analyzer tab looks like.
Finally, if you scroll down a little bit more, you will find a list of your completed security actions and those actions that still need to be performed. There is even a search interface that you can use to find a specific security action.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.