
The new flagship Microsoft hardware comes with a mixed bag of improvements and downgrades.

While the feature takes a big step forward with the new OS, there's still some ground to make up, compared to other third-party options.

No longer is the Microsoft feature gated behind hardware.

Microsoft Support and Recovery Assistant can help identify and address basic fixes in just a few easy steps.

Progress isn't a straight line. In fact, when it comes to Microsoft operating systems, it's more up-and-down.

Now that you've accessed the Microsoft Office Setup files, here's how to use them to perform a custom deployment.

If you'd rather automate and customize the Microsoft 365 deployment process instead of doing it from the management console, here's how.

Microsoft developed Windows 10 S Mode with good intentions, but not with IT pros in mind. Here's how to turn it off -- but beware. Once you disable S mode in Windows 10, there's no going back.

It's hard for Brien to get excited about Microsoft's new operating system when it still misses the mark in these three important areas.

The next phase of Microsoft's Teams push is tight integration between the collaboration platform and Windows 11 -- whether users want it or not.

Microsoft's Windows 11 unveiling was packed with information but, in some key ways, it left Brien with more questions than answers.
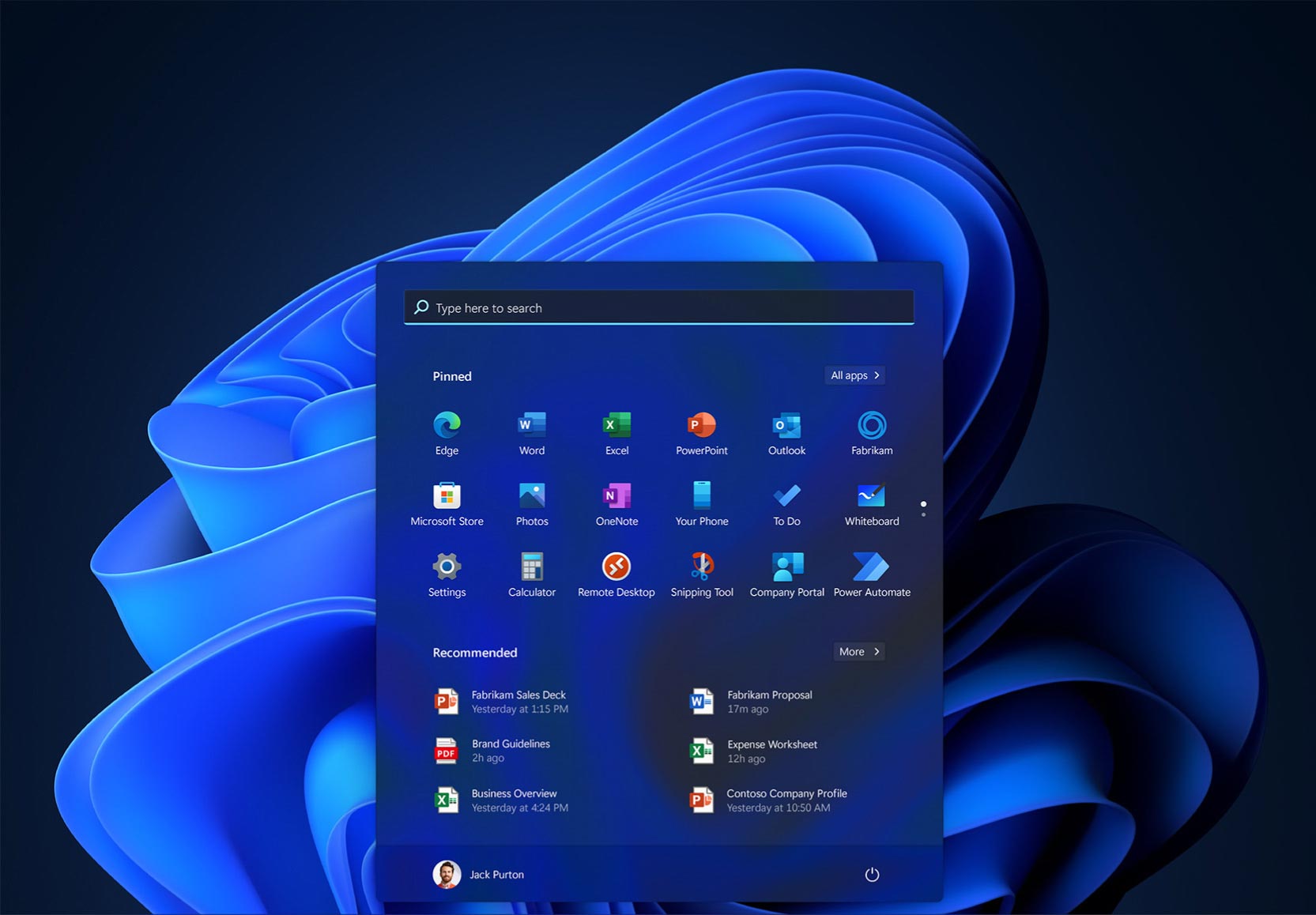
Microsoft hasn't said so, but Windows 11 might be shaping up to become the great unifying OS that Windows 10 should have been.

Brien's solution to cooling down his overheating PC works well, but probably won't scale to datacenter hardware. Enter Microsoft's inventive new datacenter cooling project.

In Part 1, Windows Reliability Monitor detected a hardware issue on Brien's Surface Book 2. Here's how he fixed the problem.

There are three initial paths you can take to diagnose a BSOD problem.