Product Reviews
Review: PowerBroker Desktops DLP
The BeyondTrust application is great for putting files on lockdown and preventing data leakage.
One of the big problems plaguing organizations is that of data leakage. Employees with legitimate access to sensitive data may either accidentally or intentionally expose data to the outside world. BeyontTrust offers a product called PowerBroker Desktops DLP that's designed as a solution to the data leakage problem.
Getting Started
PowerBroker DLP makes use of a reporting server and a desktop component. BeyondTrust provides the reporting server as a pre-configured VMware virtual machine (VM). However, for evaluation purposes, BeyondTrust will allow you to use a reporting server that's hosted on its servers.
In addition to the reporting server, there's also a client component that must be deployed on each desktop. In order to deploy the desktop client, there are two files you must run. The first file is the actual client and is named PBDLPCL64_3.2. For the purposes of this review, I ran the 64-bit version of this file, but there's also a 32-bit version available.
Installing the PBDLPCL64_3.2 file proved to be idiot-proof. The installer uses a typical installation wizard that requires little more than accepting a license agreement.
The second file that had to be installed was the snap-in, which was named PBDLPSNAP32_3.2. As was the case with the first file, this file used a really simple installer that merely required me to accept the license agreement. At first, I wondered why BeyondTrust didn't just combine the two components into a single file, but this was presumably done so that administrators can avoid having to install the snap-in onto users' desktops.
Intuitive Installation
Whenever I write a software review, I like to start out by trying to get the product up and running without using the documentation. In the case of Power¬Broker, I completed the installation with no problems.
After downloading the documentation, I discovered that PowerBroker works by extending the machine's local security policy. As such, the next step in the process was to reboot the Windows 7 machine on which I had installed the software and then open the Group Policy Editor by running the GPEdit.msc command.
I discovered that the software only modifies the Group Policy Editor in the 32-bit version of Windows 7. I was using the 64-bit edition, but was able to access the modifications by going to C:\Windows\SysWOW64\ and double-clicking on the GPEDIT.MSC file. Upon doing so, the BeyondTrust related policy settings were displayed, as shown in Figure 1.
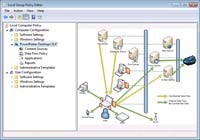
[Click on image for larger view.] |
| Figure 1. BeyondTrust PowerBroker Desktops DLP modifies the local security policy. |
The software's configured through a series of Group Policy settings. These Group Policy settings were all rather intuitive, so I set out to try to test the software. The documentation indicated that you must import a license file before the software can be used. I sent a message to BeyondTrust and had a key within five minutes. I imported the license key and the software began to work.
When I started to use the software, I was impressed. The software proved to be very easy to use and completely intuitive and -- most important -- it worked as advertised.
Ease of Use
There are four nodes in the PowerBroker Desktops DLP container. The Content Sources node allows you to define various types of content. For example, you can define what constitutes a confidential document as opposed to what constitutes a document that doesn't need to be protected.
The Data Flow Policy node lets you create rules defining what should happen when protected content is accessed. For instance, you can deny access to the content; you can also prevent protected content from being e-mailed, copied or modified (among other things).
The Applications node allows you to specify the applications that you trust, and you can even exclude applications (such as your antivirus software) from the data flow policies that you create.
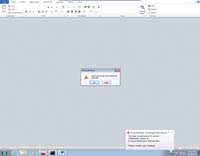
[Click on image for larger view.] |
| Figure 2. BeyondTrust PowerBroker Desktops DLP tells the user when he's attempted a prohibited operation. |
Finally, the Reports node provides instructions for generating audit reports.
The software works by allowing you to define your data at the Group Policy level and then set data flow policies that regulate what can be done with that data. To show you how this works, I defined all Microsoft Office documents as confidential and then created a data flow policy that denies read access to documents. When I attempted to open a Microsoft Word document, I was presented with this message: "Word cannot open the existing file (Normal)."
The Bottom Line
Ultimately, my opinion of PowerBroker Desktops DLP is that it's extremely effective. The software goes far beyond just preventing certain types of files from being copied. It actually analyzes the files' contents and prevents protected data from being extracted in a roundabout way. When the BeyondTrust folks demonstrated the software for me, they copied some data from a word document into another document and showed me that the software recognized the data and prevented it from being e-mailed.
Assuming that the software had merely captured the Windows clipboard, I tried to fool the software by copying the data into Notepad, saving the Notepad document, closing Notepad, copying some non- protected data to the clipboard (in an effort to flush the buffer), opening my Notepad document and pasting its contents into an e-mail message. Even after all of that, the software still recognized the data as being protected and would not allow me to send it.
| REDMOND
RATING |
Installation:
25% |
10.0 |
Features:
25% |
10.0 |
Ease of Use:
25% |
10.0 |
Administration:
25% |
10.0 |
Documentation:
0% |
7.0 |
Overall
Rating: |
9.4 |
Key: 1: Virtually inoperable or nonexistent 5: Average, performs adequately 10: Exceptional
|
|
|
My only real complaint about the software is that it can actually be too effective. Out of curiosity, I decided to find out what would happen if I told it to deny access to all content. In doing so, I locked myself out of Windows. I couldn't access the Control Panel, the Group Policy Editor -- nothing. The only way that I managed to regain control of the OS was to boot Windows into System Repair mode and recover a system restore point that was created before my reckless policy change.
If you're looking to protect your company from data leakage, BeyondTrust PowerBroker Desktops DLP is definitely the way to go.
PowerBroker Desktops DLP
$64.00 per user for 500-999 users; call for pricing for volume purchases
BeyondTrust | 800-234-9072 |
beyondtrust.com
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.