Posey's Tips & Tricks
How To Review Your User Access Control Settings -- And Why
Once universally loathed, UAC is now a very useful tool for blocking Windows security threats. Here's how to make sure you're using it appropriately.
Quickly, without stopping to think about it, name the one Windows 10 feature that annoys you more than any other. My answer would have to be Windows Update. My desktop just has a bad habit of installing updates and rebooting at the worst possible times. (Yes, I know there are ways to fix that problem.)
I have no way to know what your own answer is, but some of the more common "annoying features" might be the monetization of the Start menu, the nagging to create a Microsoft account or the seemingly never-ending parade of notifications.
Regardless of what you deem to be the most annoying Windows 10 feature, I'm guessing you didn't pick User Access Control (UAC) -- unless you just happened to take a cue from this column's title.
When it first debuted, UAC was universally loathed. It seemed that no matter what you were trying to do, UAC would get in your way. In fact, UAC was so intrusive and annoying that most people simply disabled it altogether. Thankfully, Microsoft realized that Windows users were dissatisfied (to put it mildly) with UAC and took steps to dial it back so it wasn't so obnoxious. UAC is no longer the overzealous electronic babysitter it once was.
That being the case, it might be time to take a fresh look at UAC to make sure you are using the configuration that is most appropriate for your organization's unique needs. After all, UAC can be a very effective tool for blocking certain security threats so long as it is used appropriately.
To configure the UAC settings on an individual Windows 10 machine, log into the computer as an administrator and open the Control Panel. You can get to the Control Panel by entering the word "Control" at the Windows Run prompt. Once in the Control Panel, click on System and Security, followed by Security and Maintenance, and Change User Account Control Settings. This will bring you to the screen shown in Figure 1.
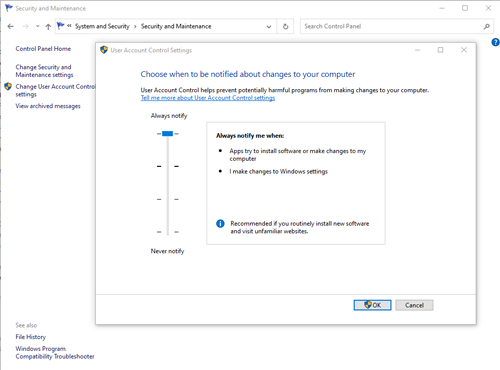 [Click on image for larger view.] Figure 1: This is what the UAC screen looks like.
[Click on image for larger view.] Figure 1: This is what the UAC screen looks like.
UAC's job is to intercept and notify you of impending configuration changes. That way, you can intervene if you suspect a malicious or otherwise undesirable change is about to be made. It is worth noting that UAC distinguishes between changes you make to your own system and configuration changes that are being made by an application. For obvious reasons, most people opt not to be notified of configuration changes they make themselves.
If you look back at Figure 1, you can see that UAC notifications are controlled by a slidebar. There are four different settings available, ranging from Never Notify to Always Notify. The Never Notify setting does exactly what it sounds like: It completely disables UAC. UAC won't notify you when you make a configuration change, nor will it tell you when an application is trying to make a change. Not surprisingly, Microsoft does not recommend using this setting.
The second option is to have Windows notify you when an application attempts to make a change to your computer, but to avoid dimming the desktop. This setting doesn't notify you about any configuration changes you initiate yourself.
Microsoft doesn't recommend using this particular setting because it does not dim the desktop. If you aren't familiar with the desktop dimming option, it's a mechanism by which UAC darkens everything on your screen except for the notification that a change is being made. This behavior makes it more difficult for a malware author to trick their victims into clicking on a fake UAC notification.
At the same time, though, using UAC without the desktop dimming option does have its place. For instance, admins who manage bandwidth-constrained virtual desktop environments sometimes use this setting to conserve a bit of bandwidth.
The third UAC option is almost identical to the one I just described, except this option does dim the desktop whenever UAC generates a notification. This is the default UAC setting.
The final option is the Always Notify option. When this option is used, Windows will notify you of all configuration changes regardless of whether they are being made by an application or by you. This option is really only appropriate for those who are in the habit of engaging in risky behavior online.
Incidentally, in a corporate environment, it is usually preferable to configure UAC via group policy rather than manually configuring Windows desktops. You can find the UAC-related group policy settings at Computer Configuration \ Windows Settings \ Security Settings \ Local Policies \ Security Options. You can see the available settings in Figure 2.
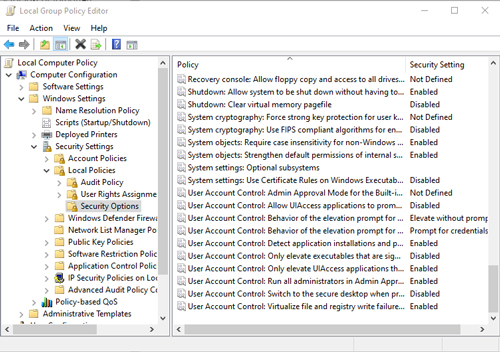 [Click on image for larger view.] Figure 2: UAC can be configured through the Group Policy Editor.
[Click on image for larger view.] Figure 2: UAC can be configured through the Group Policy Editor.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.