News
Microsoft Permits 3-Month Reprieve Before Ending Basic Authentication for Exchange Online Users
By Kurt Mackie
Microsoft still intends to turn off Basic Authentication for Exchange Online users on Oct. 1, but it is offering a possible grace period of about three months before ending it altogether.
The new milestones for Exchange Online users were outlined in this Thursday Microsoft Tech Community post by the Exchange Team. Organizations will need to run a so-called "self-service diagnostic" this month if they want to defer Microsoft from turning off Basic Authentication on Oct. 1. However, even with such deferrals specified using the self-service diagnostic tool, Microsoft is still planning to "permanently" end Basic Authentication, starting on January 1, 2023.
Some organizations may have already used the self-service diagnostic tool to block disablement of Basic Authentication, but the Exchange Team post indicated that these organizations will have to do it again this month if they really need an extension.
Here's the Exchange Teams' expression toward that end:
Today, we have archived all prior re-enable and opt-out requests. If you have previously opted out or re-enabled basic for some protocol, you'll need to follow the steps below during the month of September to indicate you want us to leave something enabled for basic auth after Oct 1.
Even still, organizations going through the trouble to keep using Basic Authentication will face a hard stop in January.
"Please understand we will be disabling basic auth for all tenants permanently in January 2023, regardless of their opt-out status," the Exchange Team clarified.
Slow Progress
Microsoft has been using its Message Center seen by IT pros to communicate its plans to end Basic Authentication support in Exchange Online. Even though IT pros have gotten such messages every month since October 2021, it's been tough to get full compliance, the Exchange Team admitted.
Some organizations may be clueless about Basic Authentication use in their environments. However, on the client side, organizations can easily tell that they are using Basic Authentication if the log-in dialog box looks like the following image:
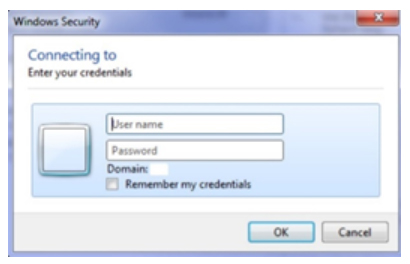 Figure 1. The Basic Authentication screen seen in client applications (Source: "Deprecation of Basic Authentication in Exchange Online" Microsoft document, dated Sept. 1, 2022).
Figure 1. The Basic Authentication screen seen in client applications (Source: "Deprecation of Basic Authentication in Exchange Online" Microsoft document, dated Sept. 1, 2022).
Security Issue
Microsoft's intent in eliminating Basic Authentication for Exchange Online is to improve security. The Basic Authentication approach just entails a user name and password, which is subject to so-called "password spray" attacks (trying easily guessed passwords across an organization to gain a foothold).
It's true that Microsoft has repeatedly moved the goal posts on its plans to block Basic Authentication in past communications. Its plans for an October end to Basic Authentication was last reiterated back in May. It's a big deal because some organizations still using it will have their e-mail blocked when Basic Authentication is ended.
Likely, though, Microsoft means it, this time around, about killing off Basic Authentication permanently in January. Skeptical IT pros can read a declaration of such intent in this Thursday post by Seth Patton, general manager of Microsoft 365.
Patton urged IT pros to check Microsoft 365 Message Center posts about the issue. He also clarified why Microsoft plans to permanently block Basic Authentication in January, citing Microsoft's security research:
Our own research found that more than 99 percent of password spray attacks leverage the presence of Basic Authentication. The same study found that over 97 percent of credential stuffing attacks also use legacy authentication. Customers that have disabled Basic Authentication have experienced 67 percent fewer compromises than those who still use it.
Most newer apps will use so-called "Modern Authentication," based on OAuth 2.0, which is deemed to be more secure, Patton explained. Updating client apps may be a simple way for organizations to get rid of Basic Authentication use.
Blocking Preview for Microsoft 365 Apps
The Exchange Team briefly noted that Microsoft has released a preview for Microsoft 365 users that "changes the default behavior of Office applications to block sign-in prompts using basic authentication." In such cases, users will see a message explaining that "the file has been blocked because it uses a sign-in method that may be insecure."
This Basic Authentication blocking preview was rolled out in August for Microsoft 365 version 2208 users, according to this Microsoft document. It'll be available at some point as well in "retail versions of Office 2021, Office 2019 and Office 2016," the document indicated.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.