News
Microsoft Offers More 'Solorigate' Advice Using Microsoft 365 Defender Tools
Microsoft issued yet another article with advice on how to use its Microsoft 365 Defender suite of tools to protect against "Solorigate" advanced persistent threat types of attacks in a Thursday announcement.
Many such articles have been generated. Microsoft's go-to landing point for organizations trying to follow the Solorigate debacle is this Microsoft Security Response Center article, which gets updated from time to time. Microsoft's Thursday article offered broad advice, but it did include specific details for users of Active Directory Federation Services, a Windows Server role used to connect with Microsoft's cloud services. Active Directory Federation Services seems to be emerging as one of the targets leveraged in the Solorigate attacks.
Microsoft's Thursday article included a diagram showing that the aim of the Solorigate attackers was to get access to cloud services, such as e-mail. Access to cloud services was gained by creating Security Assertion Markup Language (SAML) tokens in a compromised local environment.
Here's Microsoft's diagram illustrating the Solorigate attack plan:
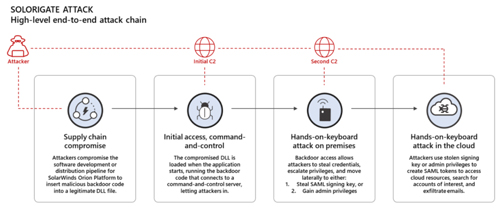 [Click on image for larger view.] Solorigate attack approach to gain e-mail access. (Source: Jan. 14 Microsoft security blog)
[Click on image for larger view.] Solorigate attack approach to gain e-mail access. (Source: Jan. 14 Microsoft security blog)
Solorigate (also called "Sunburst" by security researchers) was the initial piece of software used for the purpose. It's thought to have been injected into SolarWind's Orion management software during the build process. It later triggered the installation of malware, dubbed "Supernova," that was used in a sophisticated espionage scheme.
Active Directory Federation Services Targeted
The Cybersecurity and Infrastructure Security Agency (CISA), part of the U.S. Department of Homeland Security, recently suggested that other methods besides the Solorigate software compromise were used in these attacks. CISA also specifically pointed to Active Directory Federation Services, used in organizations' computing environments, as being leveraged by the attackers to gain access to Microsoft 365 and Azure cloud-based services.
Microsoft's Thursday announcement didn't put the blame on users of Active Directory Federation Services. It did, though, include a section called "Protect your Active Directory and AD FS infrastructure," which included some advice.
According to that advice, organizations using Active Directory Federation Services should use Microsoft Defender for Identity (a Microsoft 365 Defender tool) to turn on sensors for "all your Domain Controllers and Active Directory Federation Services (AD FS) servers," Microsoft advised. Microsoft also advised "using the 'Unmonitored domain controllers' security assessment, which lists any detected domain controllers in your environment that are unmonitored."
Details for implementing those protections weren't further described in the announcement. However, Microsoft recently opened up its FastTrack support program, offering best practices guidance to organizations with 150 subscriptions or more, to its Microsoft 365 Defender customers.
Microsoft had also advised in an earlier article on protecting Microsoft 365 by Alex Weinert, director of identity security at Microsoft, that "we recommend you disable federation trust relationships for authentication to Microsoft 365 when possible," which seems to be the most explicit downplaying of Active Directory Federation Services use by Microsoft. Weinert further advised that organizations should "use Azure AD cloud authentication to eliminate dependencies on your on-premises credentials."
Code for Sale?
Microsoft itself was a Solorigate victim. The company disclosed that its source code was viewed by the attackers. However, that exposure wasn't deemed to be a broad security compromise because of its assumed-breach software practices, Microsoft had indicated.
Possibly, though, code is being offered for sale by unknown parties. They are claiming to have the code of Microsoft, Cisco and SolarWinds, according to BleepingComputer reports. Likely, though, it's just fraud. The tawdry details can be found in this Born's Tech and Windows World article.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.