News
Microsoft Previews Azure Bastion Service for Private VM Access
Microsoft on Tuesday announced a preview of the Azure Bastion service, which lets a user connect to an Azure virtual machine (VM) using a private Internet connection.
This new managed service was created as an additional safeguard for organizations that don't want to connect to Azure VMs using public Internet connections, which could pose "security and connectivity issues," Microsoft explained in its announcement. As an alternative to Microsoft's service, organizations could instead set up their own "jump server" or "bastion host" to get these private connections. However, they'd have to do some setup and maintenance work to make that happen.
For instance, creating a jump server requires having a "Remote Desktop Services (RDS) gateway" in place. Organizations also would need to handle "the configuration and managing of authentication, security policies and access control lists (ACLs)." Moreover, they'd be tasked with "managing availability, redundancy, and [the] scalability of the solution," Microsoft suggested.
With the Azure Bastion service, organizations can start an RDS or Secure Shell (SSH) remote connection session from the Azure Portal using an HTML5-based Web browser. They connect via a Secure Sockets Layer (SSL) connection to the Azure Bastion service located in a subnet using Port 443. The Azure Bastion service then permits the user to access an Azure VM using a private Internet Protocol address (see diagram).
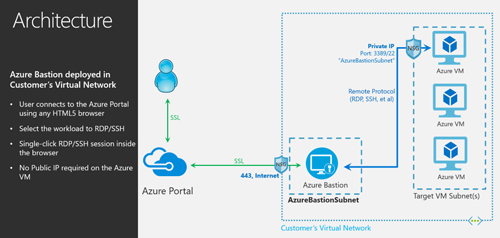 [Click on image for larger view.] The Azure Bastion managed service permits a user connect to an Azure virtual machine using a private Internet address. (Source: Microsoft Azure blog post)
[Click on image for larger view.] The Azure Bastion managed service permits a user connect to an Azure virtual machine using a private Internet address. (Source: Microsoft Azure blog post)
The Azure Bastion service is agentless, and Microsoft takes care of the patching and maintenance. The setup was described as being "simple," and Microsoft provides documentation at this page. When the service is set up, organizations will have protections against external port scanning of the Azure VMs they use, Microsoft promised.
In a future release, Microsoft plans to add Azure Active Directory integration with the Azure Bastion service. Plans include adding single sign-on access, as well as multifactor authentication (a secondary means of verifying identity besides passwords). Microsoft is also looking at expanding client and auditing support for the service.
"We are also looking to add support for native RDP/SSH clients so that you can use your favorite client applications to securely connect to your Azure Virtual Machines using Azure Bastion, while at the same time enhance the auditing experience for RDP sessions with full session video recording," the announcement explained.
The preview of the Azure Bastion service is currently limited to certain Azure regions, according to Microsoft's FAQ document, namely:
- West US
- East US
- West Europe
- South Central US
- Australia East
- Japan East
Also, the preview only works currently with the Azure Portal preview. There's no need to setup RDP or SSH beforehand as those connections are available within the Azure Portal. The preview is supported using the Microsoft Edge browser or Google Chrome on Windows. Those browsers also are supported on the macOS platform for the preview.
Microsoft charges for the use of the Azure Bastion service. It's charged by the hour and for the amount of outbound data transfers involved, as described at Microsoft's pricing page. Users will "only be billed partially during public preview," Microsoft indicated, although there's no service-level agreement during the preview phase.
For perspective on how the Azure Bastion Service could serve as a secure remote access solution for organizations, see this blog post by Aidan Finn, a Microsoft Most Valuable Professional. Right now, the Azure Bastion Service is a bit thin on having the needed capabilities, he suggested.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.