News
Microsoft and US-CERT Issue Office Malware Advice
Microsoft today warned of a somewhat new tactic being used to spread malware via Office files.
This tactic uses the Object Linking and Embedding (OLE) capability of Microsoft Office documents to perpetuate an attack. This method isn't prevalent so far. There has been "a steady decline" in such attacks since its discovery in late May, Microsoft indicated, in its announcement.
OLE Attacks
Under this OLE attack scenario, users get a Word document with instructions to follow. Typically, the instructions try to get the user to activate an object embedded in the document by clicking on it, which typically activates a malicious JavaScript or a Visual Basic script. The user might be told to double click on the object in order to unlock the document's content, for instance.
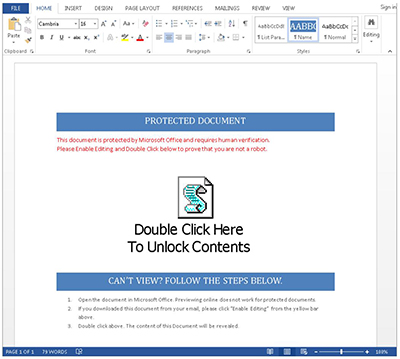 [Click on image for larger view.]
Figure 1. Example of OLE malware in Office document. Source: Microsoft blog post.
[Click on image for larger view.]
Figure 1. Example of OLE malware in Office document. Source: Microsoft blog post.
The scripts, when executed, typically drop malware, such as "TrojanDownloader:VBS," Microsoft noted.
IT pros can modify the Windows registry to block OLE package activation. They can opt to disable objects from activating, which will block script execution by end users. Microsoft lists the steps to carry that out in this support article, although it references Office 2007.
Microsoft attributed the appearance of these OLE attacks to better Office security precautions against the similar use of macros to conduct such attacks. However, that view isn't the way the United States Computer Emergency Readiness Team (US-CERT) sees it. For US-CERT, there's been a recent "resurgence" of Office macro attacks. It issued a warning to that effect this month.
Macro Attacks
This resurgence of Office macro attacks is all Microsoft's fault, according to US-CERT. Microsoft has made its Office macro warnings more confusing for end users ever since the release of Office 2010. The user interface changes in the software are to blame, according to analysis by the CERT/CC blog. Attackers are now using social engineering techniques to try to get users to enable macros by clicking on the "Enable Content" button, which is less descriptive than past warnings Microsoft has produced. Enable Content actually turns on macros in Office documents.
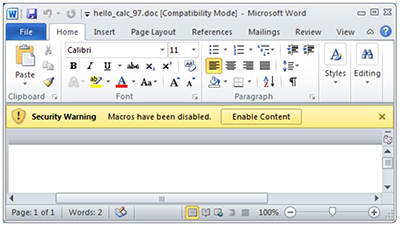 [Click on image for larger view.]
Figure 2. Office 2010's macro warning. Source: CERT/CC blog post.
[Click on image for larger view.]
Figure 2. Office 2010's macro warning. Source: CERT/CC blog post.
"The default behavior of Microsoft Office has usually allowed for inadvertent execution of malicious macros, but recent versions of Microsoft Office make it much easier for the user to make the wrong decision," the CERT/CC blog stated.
US-CERT recommends restricting access to macros in Office, which can be done by making Registry changes. Office 2016 and Office 365 have a simpler option by opting to block macros in "documents that originate from the Internet," as described here. US-CERT recommends blocking macros "without notification" to the end user for the older Office editions.
Microsoft Office for Mac 2016 apparently doesn't have an option for disabling macros, the CERT/CC blog noted.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.