News
Microsoft Releases Preview of Azure AD Application Proxy Service
Microsoft this week released a preview version of its Azure Active Directory (AD) Application Proxy service.
Azure AD Application Proxy extends Microsoft's cloud-based authentication service to an organization's internal Web apps and services. Apps within an organization that are accessible via the HTTP or HTTPS Web protocols can leverage the Azure AD Application Proxy service as a means to screen users located outside an organization's firewall, including users with non-domain-joined devices. The service is designed to act as a reverse proxy, with the aim of providing preauthentication services for users attempting to access an organization's Web apps or services.
The preview currently lacks a lot of functionality. For instance, the capability for the preauthentication of users and devices will be added in the next few months, according to Microsoft's announcement. In addition, Microsoft plans to add future support for "workplace join," which is an access method for non-domain-joined devices that depends on Windows Server 2012 R2 technology. Microsoft also plans to add support for "multifactor authentication," a security method that uses short message service or automated phone calls for secondary verification of devices and users. Another project in the works is the ability to "access your published applications in the Azure AD access panel at myapps.microsoft.com," according to Microsoft's announcement.
There are a few prerequisites for using the Azure AD Application Proxy preview. First, it requires the Microsoft Azure AD Premium service, which Microsoft launched as a commercial release back in April. The Microsoft Azure AD premium service includes security and reporting capabilities, along with multifactor authentication support and support for end user self-service capabilities. Second, the Azure AD Application Proxy technology is based on the Web Application Proxy capability in Windows Server 2012 R2, so organizations need to have Microsoft's most current flagship server software on premises. The service also taps Microsoft Azure AD Federation Services.
Azure AD Application Proxy works by installing a software agent, called a "connector," on an organization's "backend application tier." It doesn't require installing agents on devices.
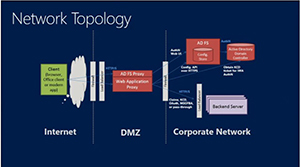
Microsoft claims that the architecture of this Azure AD Application Proxy service is such that users outside an organization's firewall never directly access the organization's network, unlike a virtual private network. The service uses Windows Server 2012 R2 technology to enable "conditional access" to Web apps and services, according to a TechEd presentation by Shai Kariv, a group program manager on the Microsoft AD engineering team. He presented the following slide illustrating the Web Application Proxy capability in Windows Server 2012 R2:
 [Click on image for larger view.]
Network topology of the Web Application Proxy in Windows Server 2012. Source: Microsoft TechEd presentation by Shai Kariv.
[Click on image for larger view.]
Network topology of the Web Application Proxy in Windows Server 2012. Source: Microsoft TechEd presentation by Shai Kariv.
While the Azure AD Application Proxy service uses Microsoft's cloud, it also taps Active Directory at the organization's backend. Microsoft claims that the service works across an organization's Demilitarized Zone (DMZ) without requiring additional hardware.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.