News
Office Macro Blocking by Default Coming This Year for Some Windows Users
Microsoft announced on Monday that it will be bringing a new default for Windows Office users that is said to "block Internet macros by default."
Microsoft's new Internet macro blocking scheme will be taking effect sometime in "early April" for Windows Office users, starting with the release of "Version 2203" for "current channel preview" users. The macro blocking scheme will arrive for other update channels mostly throughout this year, according to the following table from this document on Internet macro blocking, which is key reading:
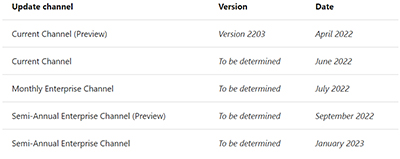 [Click on image for larger view.] Figure 1. Microsoft's plan to enable new "macro blocking" scheme for Windows Office applications (Access, Excel, PowerPoint, Visio and Word) (source: Microsoft document, "Macros from the Internet Will Be Blocked by Default in Office").
[Click on image for larger view.] Figure 1. Microsoft's plan to enable new "macro blocking" scheme for Windows Office applications (Access, Excel, PowerPoint, Visio and Word) (source: Microsoft document, "Macros from the Internet Will Be Blocked by Default in Office").
The changes are only coming to Windows systems, and were described as affecting just five Office applications, namely Access, Excel, PowerPoint, Visio and Word.
Microsoft plans to add the macro blocking default to "Office LTSC, Office 2021, Office 2019, Office 2016, and Office 2013" at some point.
The macro blocking change won't affect "Office on a Mac, Office on Android or iOS devices, or Office on the web," Microsoft indicated.
Security Risk Banner
Essentially, the current situation is that external attackers use e-mail attachments with embedded macros to execute scripts and gain a network foothold. Microsoft has typically trusted end users to make the decision on whether or not to click on such attachments, offering a fairly a mild warning that it could contain malicious "active content."
With the new default behavior that's coming to Office subscribers, macros with the "mark of the Web" or "MOTW" (indicating external arrival through the Internet) won't execute when clicked and end users will get a more robust warning, plus a link to this explanatory support article.
Here's the new warning (called a "security risk banner") that end users will see:
 [Click on image for larger view.] Figure 2. New Office warning about macros in e-mail attachments (source: Nov. 7 Microsoft announcement).
[Click on image for larger view.] Figure 2. New Office warning about macros in e-mail attachments (source: Nov. 7 Microsoft announcement).
Ultimately, these macros aren't completely blocked because end users can still save the document to a trusted location and then enable them. When they save these files, the so-called "mark of the Web" (MOTW), indicating that the source originated in the external Internet, goes away, so there's no warning.
Here's how Microsoft expressed that notion in its document on Internet macro blocking:
Saving files from the internet to a Trusted Location ignores the check for the Mark of the Web (MOTW) attribute and opens with VBA macros enabled.
Moreover, Microsoft's new macro-blocking policy won't apply if a user had previously opened a file and enabled the macros from the Trust Bar prior to Microsoft's new policy being in effect. It won't show Microsoft's new security risk banner "because the file is considered trusted," the Internet macro blocking document explained.
New Behavior
The only major change Microsoft is making with its coming new policy happens in Step 7, when end users get the new security risk banner messaging and document link, as shown in the following illustration.
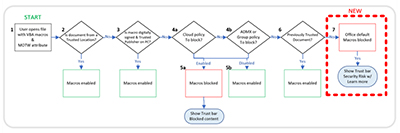 [Click on image for larger view.] Figure 3. Microsoft diagram showing how Visual Basic for Applications (VBA) macros get checked, plus the new security risk banner pop-up in Step 7 (source: Nov. 7 Microsoft announcement).
[Click on image for larger view.] Figure 3. Microsoft diagram showing how Visual Basic for Applications (VBA) macros get checked, plus the new security risk banner pop-up in Step 7 (source: Nov. 7 Microsoft announcement).
Microsoft also explained that the MOTW protection scheme only happens with NTFS-based file systems. Here's that explanation, per the Internet macro blocking document:
The Mark of the Web (MOTW) attribute is added by Windows to files from an untrusted location, such as the internet or Restricted Zone. The attribute only applies to files saved on an NTFS file system, not files saved to FAT32 formatted devices.
Policy Setting Just for Microsoft 365 Apps for Enterprise
Microsoft is recommending that organizations running Office on Windows use the new policies to block macros in Access, Excel, PowerPoint, Visio and Word, which is part of its security baseline approach. If it can't be used, Microsoft advises implementing its "VBA Macro Notification Settings policy."
Oddly, Microsoft's macro blocking document indicated that it's only possible to use policies if organizations are Microsoft 365 Apps for Enterprise subscribers:
You can only use policies if you're using Microsoft 365 Apps for enterprise. Policies aren't available for Microsoft 365 Apps for business.
Microsoft 365 Apps for Enterprise used to be called "Office 365 ProPlus," while Microsoft 365 Apps for Business once was known as "Office 365 Business." Microsoft changed these product names a couple of years ago.
Microsoft had explained back in December that it was bringing the ability for IT pros to set policies on active content in Office documents, which would block potentially abused technologies such as ActiveX content, Office add-ins and macros. Back then, Microsoft had indicated that these policy controls would be arriving to Office 365 and Microsoft 365 "current channel" subscribers in "early February 2022."
This ability to block active content by policy wasn't going to be backported to older Office apps, Microsoft had indicated at the time.
Back during the December announcement, Microsoft had not indicated that the ability to set such policies was just for Microsoft 365 Apps for Enterprise users.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.