Posey's Tips & Tricks
How To Replace an Aging Domain Controller
If the hardware behind your domain controllers has become outdated, here's a step-by-step guide to performing a hardware refresh.
Although most of the resources on my network are virtual, I have a couple of physical domain controllers that are used to control access to a resource domain. This domain is used primarily for the management of Microsoft Hyper-V servers.
Unfortunately, the hardware on which the domain controllers are running has become outdated, and it is time for a hardware refresh. I thought that I would show you the process that I am using to replace the domain controllers.
Right now, both of my domain controllers are running Windows Server 2012 R2. My goal is to replace them with new hardware running Windows Server 2016. I also want to keep the same IP addresses and server names that I was using before. This means that the domain controllers must be replaced one at a time.
The first step in the process is to demote a domain controller. Once upon a time, this meant running the DCPromo utility, but that isn't really an option any more. The way to do it is to open Server Manager, then use the Remove Roles and Features Wizard to try to remove the Active Directory Domain Services role. You won't actually be able to remove the role (at least not yet), but the error message that you receive when you try will give you the option to demote the domain controller, as shown in Figure 1.
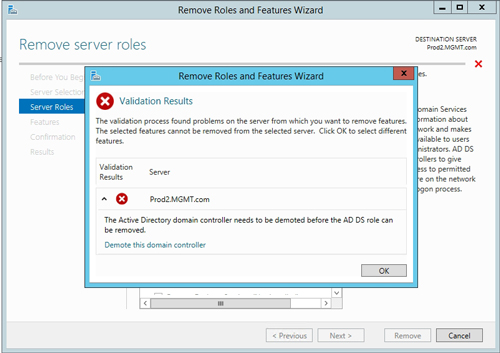 [Click on image for larger view.] Figure 1: You are given the option to demote the domain controller.
[Click on image for larger view.] Figure 1: You are given the option to demote the domain controller.
The demotion process is really straightforward. It essentially involves verifying that you really do intend to demote the server and that you are aware of the Active Directory-related roles that the server is performing. Demoting the domain controller also requires you to provide a machine-level password. It is worth noting that the downgrade process requires the server to reboot.
Demoting the domain controller is only the first step in replacing the domain controller. Although the domain controller has been demoted, the server still exists as a domain member (a member server). Therefore, the next step in the process is to remove the server from the domain.
To remove the server from the domain, right-click on the Start button and then select the System command from the shortcut menu. When the System dialog box opens, click on the Change Settings link. This causes Windows to open the System Properties dialog box, which you can see in Figure 2.
 [Click on image for larger view.] Figure 2: You will need to remove the old domain controller from your domain.
[Click on image for larger view.] Figure 2: You will need to remove the old domain controller from your domain.
Click the Change button shown in the figure above. Windows will now open the Computer Name/Domain Changes dialog box. Select the Workgroup option, shown in Figure 3, and then enter a workgroup name (WORKGROUP is the default workgroup name used by Windows).
 Figure 3: Choose the Workgroup option, then provide a workgroup name.
Figure 3: Choose the Workgroup option, then provide a workgroup name.
At this point, you will see a message telling you that after you leave the domain, you will need to know the password of the local administrator account to log on to the computer. Assuming that you know the password, click OK. When you do, Windows should complete the domain removal, and you will eventually see a message welcoming you to the workgroup. You can see an example of such a message in Figure 4.
 Figure 4: You should see a message welcoming you to the workgroup.
Figure 4: You should see a message welcoming you to the workgroup.
Click OK a few times, and then click on the option to reboot the server. At this point, the domain removal should be complete. However, it is a good idea to open the Active Directory Users and Computers console to make sure that the recently removed domain controller is no longer listed in the Domain Controllers container.
Now the replacement domain controller can be brought online. Because the old domain controller has been removed from the domain (and shut down), the new domain controller can be assigned the same name and IP address that had been used by the old domain controller. At that point all you have to do is to join the server to the domain, install the Active Directory Domain Services, then promote the machine to domain controller status.
Once the new domain controller is up and running, be sure to allow plenty of time for the Active Directory database to fully replicate before attempting to replace another domain controller. Once all of the domain controllers
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.