Posey's Tips & Tricks
How To Prevent the Use of USB Media in Windows 10
Introducing an unknown USB device into a network can cause a host of security headaches. Take away the threat in Windows 10 in just a few short steps.
Let's face it, there are a lot of things that a user could do to potentially undermine an organization's IT security. One of the most serious is using an unauthorized USB storage device. The use of such a device could lead to data leakage, or the user might use a USB storage device to install an unauthorized application. Unauthorized storage devices can even enable the spread of malware. The question is, what can you do about it?
Thankfully, Microsoft makes it relatively easy to block unauthorized USB storage devices. Let me show you how it's done.
If you look at Figure 1, you can see a Windows File explorer, and you can also see the contents of a particular USB flash drive. This one is harmless enough. It contains the slide deck for a presentation that I am giving at a Microsoft MVP event in Orlando next week. Even so, I will use this flash drive to demonstrate the ability to lock out USB media.
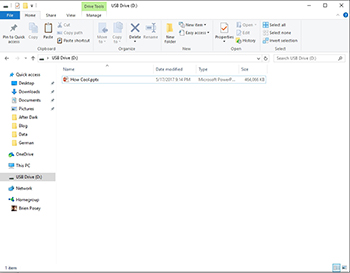 [Click on image for larger view.] Figure 1. Right now my PC can access USB media with no problem.
[Click on image for larger view.] Figure 1. Right now my PC can access USB media with no problem.
USB storage devices can be disabled either at the group policy level, or through the registry, but the group policy approach tends to be the safer option. So with that said, open the Group Policy Editor, and navigate through the console tree to Computer Configuration | Administrative Templates | System | Removable Storage Access.
As you can see in Figure 2, there are actually quite a few policy settings available for controlling access to removable storage. However, not all of these settings are related to USB devices. For example, there are several settings related to DVD and CD drives. There are even some legacy settings related to floppy drive use.
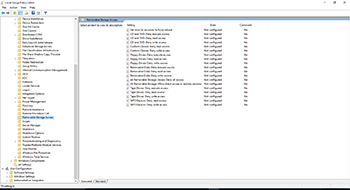 [Click on image for larger view.] Figure 2.There are numerous settings related to removable media use.
[Click on image for larger view.] Figure 2.There are numerous settings related to removable media use.
Because the group policy settings are based on media type, you can take a granular approach to storage configuration by disabling the use of USB storage, while leaving access to other types of removable media enabled. If you prefer to block removable media access regardless of type, however, then the best setting to enable is the All Removable Storage Classes Deny All Access setting. You can see what this setting looks like in Figure 3.
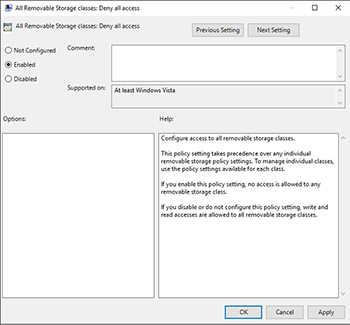 [Click on image for larger view.] Figure 3. The All Removable Storage Classes Deny All Access setting blocks all access to removable media.
[Click on image for larger view.] Figure 3. The All Removable Storage Classes Deny All Access setting blocks all access to removable media.
If you would like to try out this policy setting, you can enable it and then either reboot your computer or force a policy update. To force a policy update, open an administrative Command Prompt window, and enter the following command:
GPUpdate /Force
Now, if you plug in a USB storage device, you will see a message like the one that is shown in Figure 4.
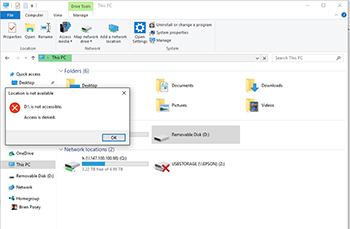 [Click on image for larger view.] Figure 4. The computer is now preventing the use of USB storage devices.
[Click on image for larger view.] Figure 4. The computer is now preventing the use of USB storage devices.
As I mentioned earlier, it is possible to disable USB storage device access at the registry level. There are several different methods for accomplishing this, but I will show you the easiest. Before I do, I want to point out that you should back up your system before continuing. Remember that editing the registry is dangerous, because doing so bypasses all of the usual OS-level safeguards. Making a mistake while editing the registry can destroy Windows and/or your applications.
So with that said, the registry key that controls USB media access is named Start and is located at HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\USBStor. Microsoft recommends setting the value of the Start key to 4. You can see what this registry key looks like in Figure 5.
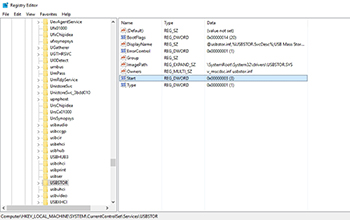 [Click on image for larger view.] Figure 5. Change the value of Start to 4.
[Click on image for larger view.] Figure 5. Change the value of Start to 4.
As you can see, it is possible to prevent access to USB storage devices, either at the group policy level, or through the Windows registry. As a best practice however, you should always use the group policy option, unless you have a compelling reason to delve into the registry.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.