News
Microsoft Graph 'Activity Logs' Feature Goes Live
Microsoft on Friday announced the general availability of the "activity logs" capability in Microsoft Graph, giving administrators more options to track user activity and, in theory, identify patterns of potential misuse ahead of a security attack.
"Microsoft Graph activity logs give you visibility into HTTP requests made to the Microsoft Graph service in your tenant," Microsoft explained in this Entra Blog post.
Microsoft touts this capability as an added handhold against potential bad actors, saying, "[T]his log data source allows you to perform security analysis, threat hunting, and monitor application activity in your tenant."
Microsoft Graph captures organizational and user data from multiple Microsoft services, including Microsoft 365, Enterprise Mobility + Security, and Windows. Previously, administrators could use Graph to access data about sign-ins and audit logs. The newly live activity logs feature expands their visibility to include things like "token request in sign-in logs, to API request activity (reads, writes, and deletes) in Microsoft Graph activity logs, to ultimate resource changes in audit logs."
Organizations need to have the following elements to take advantage of the new activity logs feature, per this Microsoft document:
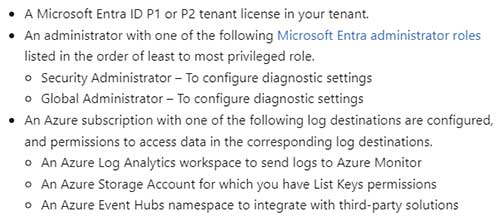 Figure 1. Prerequisites for using Microsoft Graph activity logs. (Source: Microsoft)
Figure 1. Prerequisites for using Microsoft Graph activity logs. (Source: Microsoft)
Users can analyze their logs in Azure Log Analytics Workspace, or archive them in Azure Storage Accounts. The logs can also be used with third-party tools via Azure Event Hubs.
For those using Azure Log Analytics to ingest their data, Microsoft suggests they use criteria filters to omit everything but the data they're specifically interested in, thus lowering usage costs.