Posey's Tips & Tricks
Using Ethical Scareware as an End User Security Training Tool
The Attack Simulation Tool can help you and your organization better prepare and spot phishing attempts.
In this age of ever present malware threats, it is more important than ever to educate your users about the dangers of phishing messages. In my experience however, there will always be some users who pay no attention to the warnings. Such users may feel that phishing messages and ransomware are IT's problem, not theirs. I have also encountered users who feel as though such threats are greatly exaggerated and that ransomware poses little to no actual threat for the organization.
Unfortunately, conventional security training is ineffective when it comes to these types of users. However, you may be able to scare these users into adopting better security practices by subjecting them to a harmless, yet authentic looking ransomware infection.
Before I show you how to create such an attack, I need to point out that it is important to have a frank and open discussion with your organization's HR and legal departments before moving ahead with a fake ransomware attack. Depending on where you work, there may be legal issues or company policies that would cause you to be subjected to disciplinary action for creating a fake ransomware attack, even if conducting this type of security training is in your company's best interest.
So now that I have gotten the warning out of the way, let's talk about how you can create a fake ransomware attack. As is the case with a real ransomware attack, you will need two things: a delivery mechanism and a payload.
For the purposes of this article, we will use email as the delivery mechanism. You could create an email account and use it to manually send harmless phishing messages to your users. As an alternative, I recommend using Microsoft's Attack Simulation Tool.
If you aren't familiar with the Attack Simulation Tool, it is included with Microsoft 365 E5 subscriptions (you can also get it as a security add-on for other subscriptions). The Attack Simulation Tool includes a huge collection of realistic, but harmless, phishing messages that you can send to your users in an effort to help them to recognize phishing attacks.
Normally, when a user clicks on a link within one of these fake phishing messages, Microsoft 365 displays a landing page telling the user that they have clicked on a link within a phishing message. You can see an example of one of these landing pages in Figure 1.
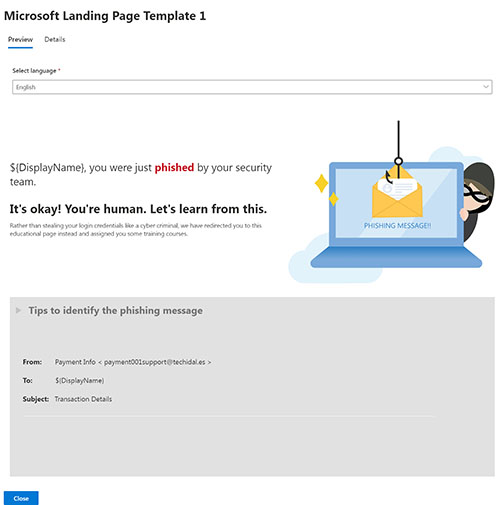 [Click on image for larger view.] Figure 1. This is one of the landing page templates provided by Microsoft.
[Click on image for larger view.] Figure 1. This is one of the landing page templates provided by Microsoft.
Interestingly, you don't have to use the stock landing page templates. You can create a custom landing page, although there is one important caveat that I will mention in a moment. This ability to create a custom landing page can be exploited for the purposes of creating a fake ransomware attack. Let me show you how it works.
To get started, open the Microsoft Defender console (formerly known as the Security Admin Center) and select the Attack Simulation Training tab. Next, click on the Launch a simulation button and then follow the prompts to create a phishing attack simulation. The process is really straightforward, so I am not going to do a full step-by-step walkthrough, but there are a couple of things that I do want to point out about the process.
The first screen that you will encounter, which you can see in Figure 2, asks you what technique you want to use. Since the goal is to create a fake ransomware attack, the Malware Attachment or Link to Malware options probably seem like the most logical choices. As you will recall, I mentioned earlier that there was a caveat that you needed to know about. That caveat is the fact that Microsoft has incorporated a safety mechanism into their Attack Simulation Training tools that prevent you from using malware-related techniques to launch a fake ransomware attack. My experience is that the Drive-By URL option works best.
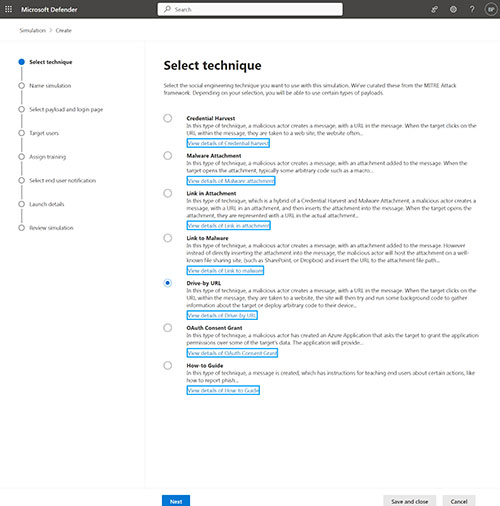 [Click on image for larger view.] Figure 2. Choose the Drive-By URL option.
[Click on image for larger view.] Figure 2. Choose the Drive-By URL option.
Once you have chosen the Drive-By URL technique, continue through the various screens until you arrive at the Select Phish Landing Page screen, shown in Figure 3. As you can see in the figure, this screen gives you the option of using a custom URL, although the custom URL option does not exist if you selected a malware related attack technique.
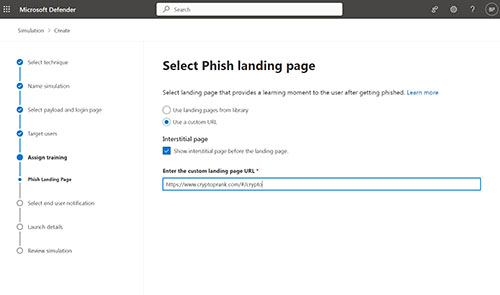 [Click on image for larger view.] Figure 3. You can use the Select Phish Landing Page option to direct users toward a fake ransomware attack
[Click on image for larger view.] Figure 3. You can use the Select Phish Landing Page option to direct users toward a fake ransomware attack
Earlier I mentioned that a phishing attack required a delivery method and a payload. The payload is fake ransomware, and this is where you call if from. All you need is URL for a Web page that displays a fake ransomware attack. You can create such a page yourself, or there are some fake ransomware pages that already exist online (just make sure to verify that they are safe by testing them in a sandbox before using them). For the purposes of this article, I am using the CryptoPrank site (https://www.cryptoprank.com/#/). This site, which you can see in Figure 4, offers two different fake ransomware attacks.
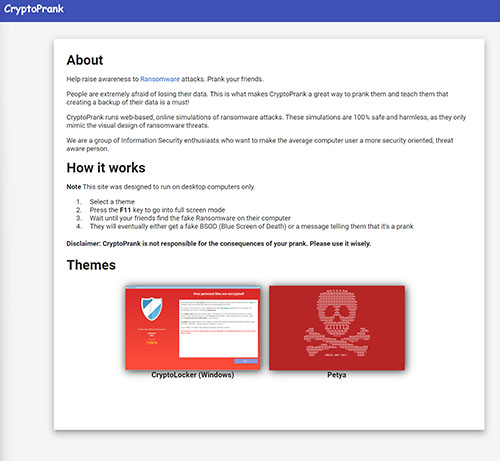 [Click on image for larger view.] Figure 4. CryptoPrank offers two fake ransomware options.
[Click on image for larger view.] Figure 4. CryptoPrank offers two fake ransomware options.
When you finish setting up the simulation, you will reach a screen similar to the one shown in Figure 5. This screen gives you the chance to send a test message to your own mailbox so that you can see what the simulated phishing email will look like. It is worth noting however, that if you click on the link within this email you will be take to a page that displays the words Ping Successful, as shown in Figure 6. The landing page that you have specified will not be displayed until you actually launch the simulation.
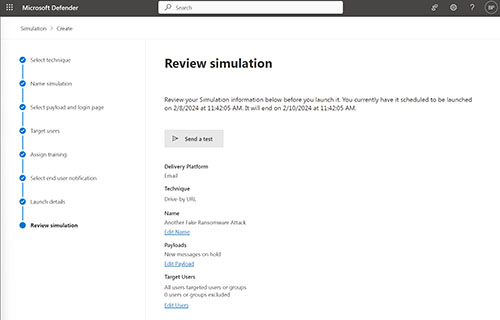 [Click on image for larger view.] Figure 5.You can send a test message to yourself.
[Click on image for larger view.] Figure 5.You can send a test message to yourself.
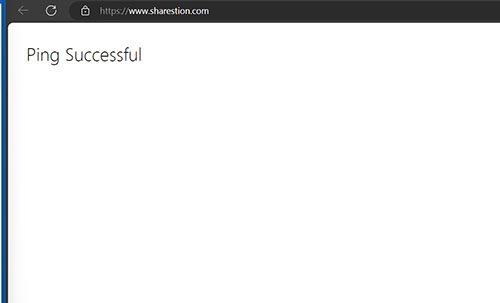 [Click on image for larger view.] Figure 6. This is the page that is displayed when you click on the link in the test email.
[Click on image for larger view.] Figure 6. This is the page that is displayed when you click on the link in the test email.
Upon running the simulation, your users will receive the message that you have set up in the phishing simulation. You can see an example of such a message in Figure 7. When the user clicks on a link in the message, they will be taken to the fake ransomware attack, as shown in Figure 8.
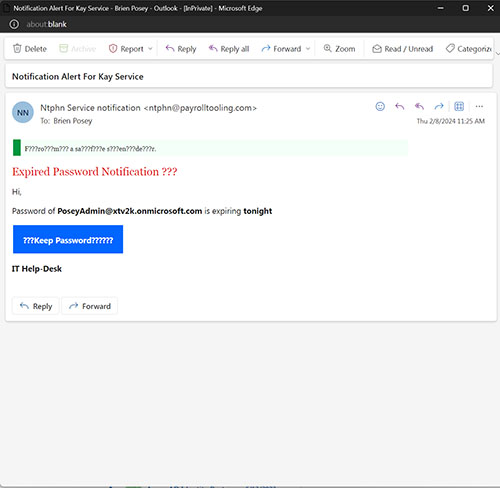 [Click on image for larger view.] Figure 7. This is an example of a message generated by the Attack Simulation Tool.
[Click on image for larger view.] Figure 7. This is an example of a message generated by the Attack Simulation Tool.
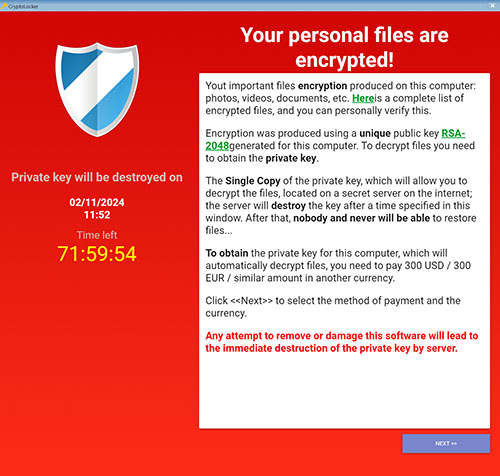 [Click on image for larger view.] Figure 8. This is the fake ransomware attack that was displayed when I clicked on the link within the email.
[Click on image for larger view.] Figure 8. This is the fake ransomware attack that was displayed when I clicked on the link within the email.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.