Posey's Tips & Tricks
Beware These New Microsoft Office 365 Phishing Attacks
Admins, take note: Hackers are increasingly targeting Office 365 with new and more sophisticated phishing schemes. Here's a snapshot of the most common methods.
Phishing attacks are obviously nothing new, but lately I have been noticing an increase in phishing attacks that specifically target Office 365.
A lot of these phishing messages are intended to make recipients think that they have received a voice message. You can see a somewhat primitive example of this in Figure 1.
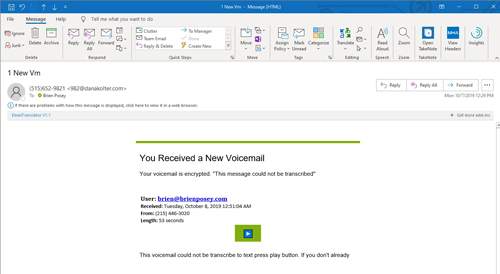 [Click on image for larger view.] Figure 1: Phishing scams are increasingly trying to trick users into thinking that they have received a voice message.
[Click on image for larger view.] Figure 1: Phishing scams are increasingly trying to trick users into thinking that they have received a voice message.
As you can see in the figure, the message provides a bogus phone number, a message length and a message stating that the call could not be transcribed. The message then prompts the recipient to click on a presumably malicious link to access the message.
Although I have recently received plenty of messages like the one shown above (along with several variants), some messages actually look like they came from Microsoft. Unfortunately, I couldn't find an example that I could include in a screen capture, but I will tell you what these messages look like.
The messages are somewhat similar to the one shown in Figure 1 above, except that they contain a Microsoft logo. I have also heard stories of some of these messages using an Office 365 logo or a Microsoft Teams logo instead. The messages include an HTML attachment that redirects the victim to a phishing site that is designed to look like the Microsoft Office 365 portal. At that point, the victim is prompted to enter their Office 365 credentials, and those credentials are promptly stolen.
This isn't the only type of Office 365-specific phishing attack that has been on the increase. There is another attack that has been targeting Office 365 admins.
We have probably all seen phishing attacks in which an e-mail message is meant to appear to have come from Microsoft, and prompts Office 365 administrators to take some sort of action, such as updating billing details. These attacks have been around for years.
Recently, attackers have introduced a new spin on these types of attacks. Instead of trying to spoof Microsoft in message's Sender field, the attacker will send the message from another domain that has been compromised. The idea is that because the message comes from a legitimate domain (albeit one that has been compromised), filters will be less likely to block the message. Of course, an administrator who is paying attention can easily verify that the message did not come from Microsoft.
While I am at it, there is one more phishing attack that I want to tell you about. This one wasn't Office 365-specific, but it was so audacious that I just couldn't write an article on phishing and not mention this attack.
Microsoft has several fictitious companies (with corresponding domain names) that it routinely uses during product demos. These include "companies" like Contoso, Northwind Traders, Tailspin Toys and a few others. Similarly, I also own several domain names that I use solely for demonstration purposes. Recently, one of these domains was coming due for renewal. I had configured the domain to automatically renew, and when the time came, GoDaddy sent me confirmation of the renewal by e-mail. You can see the legitimate renewal e-mail in Figure 2.
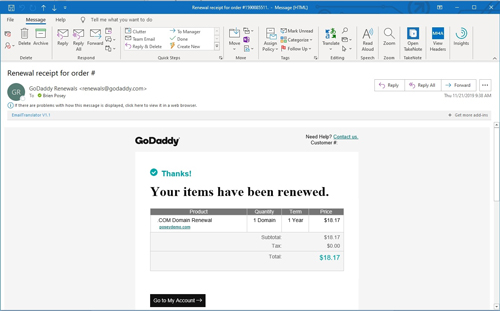 [Click on image for larger view.] Figure 2: This is a legitimate renewal e-mail.
[Click on image for larger view.] Figure 2: This is a legitimate renewal e-mail.
So now that I have shown you what the legitimate renewal notice looks like, take a look at the e-mail message shown in Figure 3 below. Even though this message bears the GoDaddy logo, the From address points to PayPal. This part of the message is legitimate; the message really did come from PayPal. Someone used the domain registry to figure out that one of my domains needed to be renewed and sent me an invoice through PayPal.
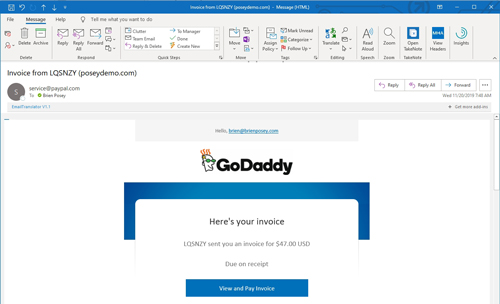 [Click on image for larger view.] Figure 3: This message is a scam.
[Click on image for larger view.] Figure 3: This message is a scam.
Obviously, GoDaddy doesn't use PayPal for its billing, but there are a few other red flags in this e-mail message that give it away as a scam. For starters, the invoice is from LQSNZT, not GoDaddy. The other giveaway is the message that was included with the invoice, which is chock-full of grammatical errors. You can see the message in Figure 4.
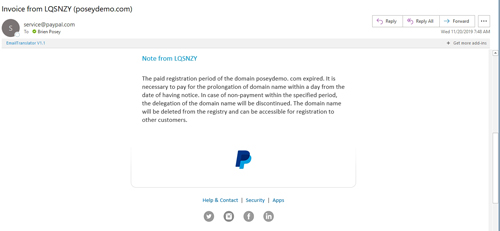 [Click on image for larger view.] Figure 4: The message included with the invoice was full of grammatical errors.
[Click on image for larger view.] Figure 4: The message included with the invoice was full of grammatical errors.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.