Posey's Tips & Tricks
How To (Safely) Run Untrusted Applications in Windows 10
The new Sandbox feature in Windows 10 lets organizations run potentially risky executables in isolation, without having to set up a virtual machine.
Roughly nine months ago, I wrote a column in which I speculated on whether Hyper-V was about to be removed from Windows 10 and replaced by something else. The speculation stemmed from some leaked screen captures of a yet-to-be-released Windows 10 build, in which the Hyper-V option had been replaced by a more generically named option called "Virtual Machines."
At the time, I dismissed the Virtual Machines option within the leaked screen capture as simply being a placeholder for Hyper-V. I argued that it would not make sense for Microsoft to cripple Windows 10 by removing Hyper-V.
Microsoft has since released version 1903 of Windows 10, and I am happy to say that Hyper-V is alive and well in the new version. But what about that Virtual Machines option?
Although it's hard to say for sure why this option existed in the early build, I think that it most likely corresponded to a brand-new Windows 10 feature called Windows Sandbox. The Windows Sandbox feature lets you run potentially risky executables in a sandboxed environment without having to go through the trouble of setting up a virtual machine (VM). Here is how you can use this feature.
In Windows 10 version 1903, right-click on the Start button and choose the Run option from the shortcut menu. When the Run prompt appears, enter the word "Control" to launch the Windows Control Panel. Now, click on Programs, followed by the option to Turn Windows Features on or off. As you can see in Figure 1, the resulting Windows features list contains an option called Windows Sandbox.
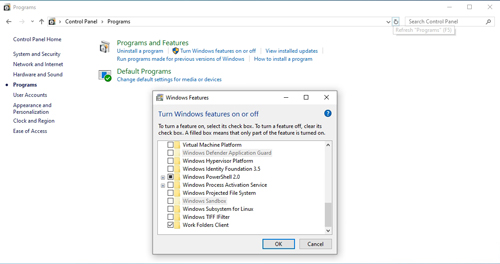 [Click on image for larger view.] Figure 1: Windows Sandbox is listed among the Windows features that you can turn on or off.
[Click on image for larger view.] Figure 1: Windows Sandbox is listed among the Windows features that you can turn on or off.
In case you are wondering, the reason why Windows Sandbox is grayed-out in the screen capture is because I am running Windows inside of a Hyper-V VM. It would probably be possible to experiment with Windows Sandbox inside of a VM by enabling VM nesting. However, the nested VMs feature for Hyper-V requires an Intel processor and my lab servers are all running AMD processors, so I can't enable nesting to find out if it works for sandboxed VMs.
Even though I was unable to enable the new Windows Sandbox feature on my VM, I went ahead and enabled it on a physical desktop so that I could show you what the feature looks like. As you can see in Figure 2, Windows Sandbox looks a lot like a VM. It is essentially just a Windows 10 instance running inside of Windows 10. In case you are wondering, you can access Windows Sandbox from the Windows 10 Start menu.
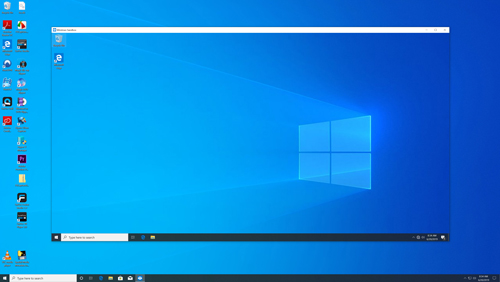 [Click on image for larger view.] Figure 2: This is what Windows Sandbox looks like.
[Click on image for larger view.] Figure 2: This is what Windows Sandbox looks like.
Before I wrap up this column, there is one important thing that I need to talk about. Windows Sandbox is being widely described as an isolated environment that can be used to safely run code that may or may not be safe. However, the idea that you can run potentially malicious code in Windows Sandbox without putting your system at risk is only partially true.
When you run an application in Windows Sandbox, that application is isolated from your primary Windows operating system, and therefore cannot damage it. When you close Windows Sandbox, it is reverted back to a pristine state, which means you don't have to worry about damaging the sandbox environment or your primary Windows operating system.
Even so, the fact that Windows Sandbox can access the Internet means that the sandbox has network connectivity. Thankfully, Microsoft does not make it easy to map a network drive or attach to a file share from within Windows Sandbox.
However, if someone were to attach Windows Sandbox to a network share, iSCSI storage or something like that, then there is a good chance that malware could attack resources outside of the sandbox. As such, I recommend that you avoid establishing any sort of external connectivity beyond whatever Windows Sandbox provides by default.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.