News
New Microsoft Autopatch Service Aims To Patch PCs Automatically
Microsoft on Tuesday unveiled Windows Autopatch, which lets Microsoft take over quality and security patching operations in organizations, including Windows operating system feature updates, plus driver updates.
Windows Autopatch is expected to reach the "general availability" commercial-release stage in July. It'll be free for organizations meeting certain Windows Enterprise E3-type licensing requirements and prerequisites, allowing them to automatically patch and update Windows 10 and Windows 11 client devices.
The scheme will work with premises domain-joined devices if an organization uses "Hybrid Azure AD mode with Microsoft Intune," Microsoft explained in an accompanying FAQ, which means tying local Active Directory to the Azure Active Directory service.
Windows Autopatch also supports patching operations for Windows 365 for Enterprise users. However, Windows 365 for Business users aren't supported.
While Microsoft essentially takes over the patching for organizations with Windows Autopatch, the service has rollback capabilities in cases where there are problems. The rollbacks are automated, too.
The scope of Windows Autopatch includes some, but not all, "third-party" (non-Microsoft) drivers that would typically get automatically applied. If the driver is optional (that is, it gets published as "Manual"), then it doesn't get automatically supported by Windows Autopatch. IT pros would have to apply those drivers manually, if wanted.
Windows Autopatch is just for client devices, as Microsoft has no plans to bring it to Windows Server, according to the FAQ. For Windows Server 2022 Datacenter Azure Edition product users, though, Microsoft does have a Hotpatch capability, which is part of its Azure Automanage service.
The setup of Windows Autopatch is said to be as simple as just consenting for Microsoft to handle the software patching, as described in this video. Organizations also have to provide administrator contact information to Microsoft in case there are incidents or notifications.
Deployment Rings Model
Windows Autopatch is the software realization of Microsoft's "deployment rings" patching model that it has been encouraging organizations to use over the last few years. IT pros following this model have had to set up these user testing groups manually, but Microsoft aims to do that work automatically with Windows Autopatch.
Under the deployment rings model, organizations are supposed to set up a group of users who get early software releases for testing. If things go well with that group, the software update get released more broadly to other and larger test groups. This process repeats until a full rollout happens.
Microsoft illustrated how the deployment rings model would work with Windows Autopatch in the following graphic, which shows the percentage of users in four groups getting software updates:
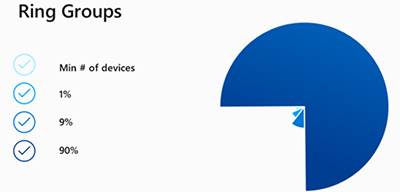 [Click on image for larger view.] Figure 1. Microsoft's ring groups concept for Windows Autopatch, where software updates get tested early by small groups of users and then passed to progressively larger groups before a full organizational rollout.
[Click on image for larger view.] Figure 1. Microsoft's ring groups concept for Windows Autopatch, where software updates get tested early by small groups of users and then passed to progressively larger groups before a full organizational rollout.
With Windows Autopatch, the ring groups get "managed automatically." IT pros can move specific devices between the groups, though.
The service puts a priority on rolling out monthly "quality updates," especially with regard to security and firmware updates. It takes a slower rollout approach with "feature updates," where essentially the whole operating system is replaced by a new one. Users get a 30-day period to report problems with feature updates.
Windows Autopatch also has a "Halt" feature, which is instigated by Microsoft or by its customers when there are patch problems. A "Rollback" feature also is available for software update failures, which can happen automatically. It's also possible to permit some updates to go through and hold back others with a "Selectivity" feature.
IT pros will be able to view Windows Autopatch nuances via a message center. Microsoft delivers update compliance reports, too, with the Windows Autopatch service. These details possibly surface in Microsoft Intune or Configuration Manager (Microsoft didn't really describe this aspect).
Windows Autopatch Requirements
Windows Autopatch has licensing requirements, as well as prerequisites that vary depending on whether Microsoft Intune is used or Configuration Manager (with the Comanagement capability). "Comanagement" means using Microsoft Intune within the Configuration Manager console.
Here are the licensing requirements for Windows Autopatch:
- Windows 10/11 Enterprise E3 and up
- Azure AD Premium (for co-management)
- Microsoft Intune (includes Configuration Manager, version 2010 or greater via co-management)
If organizations are using Microsoft Intune only for management, then they'll need to also use Azure Active Directory.
If organizations are using Configuration Manager with the Comanagement capability, then they have a longer list of prerequisites to follow, namely:
- Hybrid Azure AD-Joined or Azure AD-joined only
- Microsoft Intune
- Configuration Manager, version 2010 or later
- Switch workloads for device configuration, Windows Update and Microsoft 365 Apps from Configuration Manager to Intune (min Pilot Intune)
- Co-management workloads
There are no hardware requirements for using Windows Autopatch, although devices must still be in good standing with "hardware OEM" support. That stipulation typically means that the processors in the machines must still be supported by Intel or AMD.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.