News
Microsoft Releasing My Sign-Ins and App Lock Azure Active Directory Protections
Microsoft announced a couple of Azure Active Directory-based security enhancements this week, which are now available for end users.
Office 365 users are getting access to a new My Sign-Ins portal, showing sign-in activity (including the activity of attackers). In addition, Microsoft is rolling out App Lock protections by default for Microsoft Authenticator App mobile device users.
My Sign-Ins General Availability
The My Sign-Ins feature for Office 365 users, which lets them check account sign-in attempts, has reached "general availability," or commercial-release status, Microsoft announced on Monday.
My Sign-Ins is an enterprise feature for Office 365 users that can be accessed directly through this URL or it's available through a user's My Profile "Overview blade." My Sign-Ins users will see the following information, per the announcement:
- If anyone is trying to guess their password.
- If an attacker successfully signed in to their account from a strange location.
- What apps the attacker accessed.
The feature was at preview back in October. Since then, Microsoft has added some more features. For instance, it's now more mobile-device friendly, and it now includes two new buttons that let end users categorize the account activity that gets shown -- namely, the "This Wasn't Me" and "This Was Me" buttons.
Clicking the "This Wasn't Me" button starts a workflow for end users to change their passwords. Users would click "This Wasn't Me" for things like successful sign-ins from unfamiliar locations. The My Sign-Ins app will show users the approximate location associated with the attempt, although it may not correspond with an attacker's exact location.
Unsuccessful sign-in attempts get shown. They could be due to mistyped passwords by the end user or an attacker was attempting to guess the password. In cases where an attacker is active, but failing to guess the password, Microsoft advises enabling multifactor authentication (adding a secondary identity verification method beyond a password). The password doesn't have to be changed in such cases, though.
Here's Microsoft advice on what to do on discovering unsuccessful sign-in attempts:
If it's because an attacker was trying to guess the password (but was unsuccessful), then there's no need for the user to change their password. However, this is a great reason for the user to register for Azure Multi-Factor Authentication (MFA), so even if the hacker eventually guesses the password, it won't be enough to access the account.
In my case, when I tried using the My Sign-Ins feature, I discovered that someone (or some bot) in Hebei, China has been trying to access my Office 365 Exchange account every minute of the day, and that's just for today. The attacker's IP address is shown:
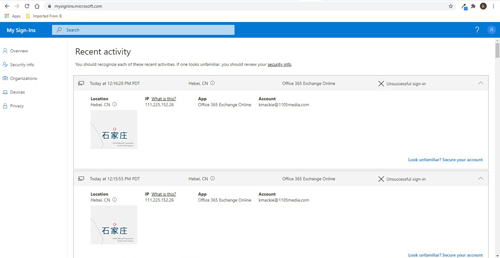 [Click on image for larger view.] My Sign-Ins screenshot showing attacker activity.
[Click on image for larger view.] My Sign-Ins screenshot showing attacker activity.
An unsuccessful sign-in screen will include a link reading, "Look unfamiliar? Secure your account." When that link gets clicked, it'll report the sign-in attempt as "unsafe" and will direct end users to another page to add multifactor authentication protection, such as adding a phone number or specifying the use of the Microsoft Authenticator App for account verification on top of a password.
Microsoft states that "based on our studies, accounts protected by MFA are 99.9 percent less likely to be compromised."
During the preview of My Sign-Ins, Robyn Hicock, a senior program manager on the Microsoft Identity Security and Protection team, responded to a question about adding alerts for administrators. At the time, she suggested it was part of Microsoft's plans.
"Yep our long term plan is to give admins the option to set up alerts," she wrote back in October regarding My Sign-Ins. Microsoft also aims to send alerts to end users, too, at some point, she had indicated.
App Lock in Microsoft Authenticator
In other Azure AD-related news this week, Microsoft on Monday announced that it is turning on the App Lock feature by default for iOS mobile device Microsoft Authenticator users. App Lock will get turned on for Android device Microsoft Authenticator users sometime "next month."
App Lock gets turned on by default "if you've set up a PIN or biometric on your device," Microsoft explained. "When App Lock is enabled, you'll be asked to authenticate using your device PIN or biometric every time you open Authenticator," Microsoft explained in an FAQ document.
App Lock ensures that an application "was secured by a PIN or biometric" after receiving a Microsoft Authenticator notification. Apparently, the idea is that App Lock will protect users should they walk away from their mobile devices.
Here's how Microsoft described it:
Currently, when the notification arrives on the phone, you can click approve/deny from the lock screen. However, when app lock is enabled, you will have to launch the app (on iOS) or launch a dialog (on Android) before you can click approve/deny, and you'll also need to provide an additional PIN/bio gesture to successfully authenticate. Thus, even if you leave your phone unlocked on your desk and walk away, a passerby cannot approve the notification for you.
For organizations using multifactor authentication, the PIN that gets used in this process is "your MFA pin (not your device pin)," Microsoft explained.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.