News
Azure Key Vault Service Now Commercially Available
Microsoft turned on its Azure Key Vault service this week for commercial use.
Azure Key Vault is a means of managing the cryptographic keys and passwords (called "secrets" by Microsoft) that are associated with applications. It works by tapping hardware security module (HSM) appliances housed in Microsoft Azure datacenters where the keys are stored. The service is currently available in all regions except Australia, but the Australian service will be "coming soon," according to Microsoft's announcement. It was last released as a preview back in January.
Azure Key Vault centralizes access to HSMs for developers building security into their apps, but it's also for IT pros that manage custom business applications. For instance, the service can be used to assure that compliance standards are met when using software-as-a-service (SaaS) applications. Organizations may need to assure that the application security of SaaS apps is tied to HSMs that meet the Federal Information Process Standard (FIPS) 140-2 Level 2 approach or Common Criteria EAL4+ certification. Organizations also may need to have lifecycle control over the encryption keys associated with these SaaS apps.
This scheme was explained by Sumedh Barde, a program manager with the Azure security team, in a Microsoft-produced video. He illustrated the concept with this slide:
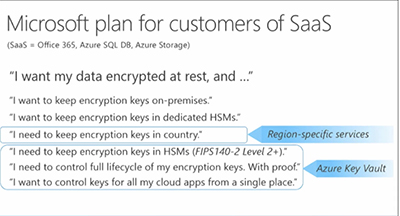 [Click on image for larger view.]
Azure Key Vault security assurance for SaaS apps. Source: a Microsoft video.
[Click on image for larger view.]
Azure Key Vault security assurance for SaaS apps. Source: a Microsoft video.
Barde explained that applications can use the cryptographic keys of Azure Key Vault but the apps can't "see" the keys. The keys can be HSM-protected keys or software-protected keys. Certain specialized apps tend to use the cryptographic keys plus HSM approach. Azure Key Vault itself is "just a container for related keys and secrets," Barde added, and it addresses an issue for developers on where to store passwords and keys. Azure Key Vault leverages the Azure Active Directory identity and access management service to access the keys.
Some software developers are using Azure Key Vault within their applications. The master keys can be centrally managed using CloudLink Secure VM for virtual machine encryption. Brocade's SteelApp traffic manager for TLS also can be used. Microsoft is planning an Azure Disk Encryption feature that will be able to use Azure Key Vault. It also will be possible to use Azure Key Vault for SQL Server encryption, although Microsoft didn't specify a timeline.
The interface with Azure Key Vault is set up using NuGet packages for .NET, which is currently available. There's also a software development kit for Node.js, which at the "preview" stage. Microsoft also has new REST APIs for Azure Key Vault. The new REST APIs replace the previous APIs that were at the preview level.
Azure Key Vault currently supports Azure Virtual Machine certificates. Support for Azure Storage encryption is at the preview stage. Azure Disk Encryption for Windows and Linux virtual machines isn't available yet.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.