News
Microsoft Confirms System Slowdowns from Fixes to Meltdown and Spectre Attack Methods
Microsoft on Tuesday affirmed that Windows operating system updates released on Jan. 3 to address the Meltdown and Spectre CPU security issues will have noticeable system slowdown effects in some instances.
Performance slowdowns will be most apparent for older Windows client systems, such as Windows 7 and Windows 8, particularly when using Intel Haswell chips on "2015-era PCs," according to an announcement by Terry Myerson, executive vice president of the Windows and Devices Group. Microsoft expects "most users to notice a decrease in system performance" on these older Windows clients.
Myerson's most cautionary remarks, though, were reserved for the slowdown effects expected for Windows Server products. The slowdown will be apparent on those systems regardless of the processor used when Microsoft's Jan. 3 updates are applied:
Windows Server on any silicon, especially in any IO-intensive application, shows a more significant performance impact when you enable the mitigations to isolate untrusted code within a Windows Server instance. This is why you want to be careful to evaluate the risk of untrusted code for each Windows Server instance, and balance the security versus performance tradeoff for your environment.
The specific Windows Server performance degradation details weren't provided in the announcement. Myerson noted that Microsoft is currently performing its own benchmark studies and plans to publish the results when done.
The performance hits for Windows 10 systems using the Jan. 3 updates will depend on the age of the silicon chips. Newer Windows 10 systems, namely "2016-era PCs with Skylake, Kabylake or newer CPUs," will have slowdowns in the milliseconds that most users won't notice, according to Microsoft. However, users of older Windows 10 systems, namely "2015-era PCs with Haswell or older CPUs," will likely perceive a system slowdown.
Intel and other chip makers have generally indicated that both OS updates and silicon firmware updates are required to address the Meltdown and Spectre attack methods. However, Microsoft's announcement added an important clarification. In a table, Microsoft showed that a firmware update is only required to address the Spectre variant 2 attack approach.
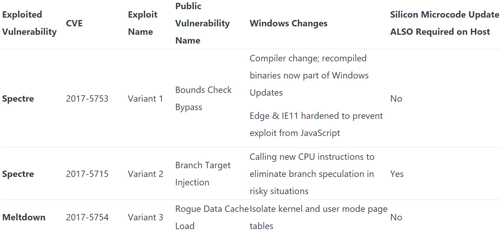 [Click on image for larger view.] Windows mitigations for Meltdown and Spectre attack methods. Source: Microsoft announcement.
[Click on image for larger view.] Windows mitigations for Meltdown and Spectre attack methods. Source: Microsoft announcement.
Alas, it's the variant 2 fix that entails the greatest performance hit on systems.
"In general, our experience is that Variant 1 and Variant 3 mitigations have minimal performance impact, while Variant 2 remediation, including OS and microcode, has a performance impact," Myerson stated.
Another important clarification by Microsoft is that the firmware update ("silicon microcode") distributions are decided by the PC or server original equipment manufacturers (OEMs). The OEMs' firmware updates could arrive via Windows Update or another mechanism:
Silicon microcode is distributed by the silicon vendor to the system OEM, which then decides to release it to customers. Some system OEMs use Windows Update to distribute such microcode, others use their own update systems. We are maintaining a table of system microcode update information here. Surface will be updated through Windows Update starting today.
Microsoft, for its part, has released 41 of 45 OS updates through its Windows Update service to address the Meltdown and Spectre threats. The remaining updates will be coming "soon."
Intel CEO Brian Krzanich had indicated earlier this week that Intel plans to issue microcode updates for chips up to 5 years old by the end of this month. Possibly, updates for older Intel chips will be coming, too, as suggested in an Intel statement issued Tuesday:
In early December we began distributing Intel firmware updates to our OEM partners. For Intel CPUs introduced in the past five years, we expect to issue updates for more than 90 percent of them within a week, and the remainder by the end of January. We will continue to issue updates for other products thereafter. We are pleased with this progress, but recognize there is much more work to do to support our customers.
Intel continued to downplay the performance hits of these OS and firmware updates, stating that "based on our tests on SYSmark 2014 SE, a leading benchmark of PC performance, 8th Generation Core platforms with solid state storage will see a performance impact of 6 percent or less."
The Meltdown attack method is thought by researchers at the Graz University of Technology to mostly affect Intel-based CPUs, while Spectre is thought to affect chips from Intel, AMD and ARM Holdings. Both attack methods leverage a normal processor method, called "speculative execution," to pull privileged information (such as passwords) from the operating system's kernel. Unfortunately, researchers found ways to surface that information.
The attack methods depend on malware being on a system. So far, active attacks haven't been detected, but the problem has been present in chips for decades.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.