In-Depth
Protecting Office 365 from Attack
As the rate and sophistication of ransomware and phishing campaigns accelerate, Office 365 has become a primary target, making a defense-in-breadth strategy critical.
- By Jasson Walker
- 05/30/2017
While hackers have targeted Microsoft products and services for decades, the growth in ransomware and phishing attacks has made Office 365 a primary target. Now that Office 365 has become the company's fastest-growing offering and the breaches coming from e-mail and misused identities continue to accelerate, it's essential that Office 365 administrators take proactive steps to "hack-proof" their environments.
A recent report released by the U.S. Department of Justice revealed that ransomware -- the fastest growing malware -- quadruped last year from 1,000 attacks per day observed in 2015 to more than 4,000 daily incidents with the amounts paid in ransom expected to reach $1 billion. The average ransom paid is $500. The risk of malware from e-mail doubled last year, based on findings from the 2017 Symantec Corp. "Internet Security Threat Report," which showed the probability of an attack via e-mail rose to one in 131 last year from one in 224 in 2015. The 2017 Verizon "Data Breach Investigations Report" found that 43 percent of hackers used e-mail-based phishing as their method of attacks, which were associated with espionage and financial theft.
Last year Microsoft saw malware attempts targeted at Office 365 increase 600 percent, said Jason Rogers, Microsoft's lead program manager for antimalware and advanced threat detection for Office 365, speaking during a session at last fall's Microsoft Ignite conference in Atlanta.
Unfortunately, like other software, it's virtually impossible to "hack-proof" Office 365. Nevertheless, you can significantly mitigate the probability of a successful attack by understanding common Office 365 attack vectors and implementing a comprehensive strategy that defends your environment against the growing number of threats. A defense strategy must incorporate multiple Office 365 defense-in-breadth (not depth) security services, user awareness training and by utilizing the continuous monitoring services offered with Office 365.
Among the most pervasive attacks against Office 365 users is ransomware, and given last year's sharp rise, it's a significant problem. One example of a high-profile Office 365 attack vector was last year's Locky attack. Let's examine the attack and some best practices to defend your environment against it.
Anatomy of an Osiris/Locky Ransomware Attack
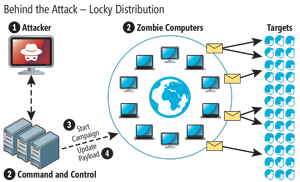
In addition to Locky, a more recent iteration of it has emerged, which is called Osiris. Once an attacker reaches a user endpoint, the malware encrypts the hard drive and demands .5 to 2 Bitcoin to decrypt your data. At last the Atlanta Ignite conference, Microsoft gave a detailed description of how the attack is executed (see Figure 1 and Figure 2).
 [Click on image for larger view.]
Figure 1. The path of the Locky/Osiris attack.
[Click on image for larger view.]
Figure 1. The path of the Locky/Osiris attack.
 [Click on image for larger view.]
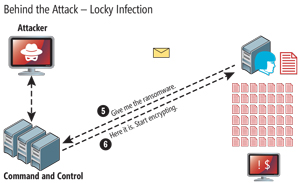
Figure 2. The flow of a ransomware attack following a successful phishing attempt.
[Click on image for larger view.]
Figure 2. The flow of a ransomware attack following a successful phishing attempt.
1. The Attacker: Many attackers are now well-funded, professional hackers with advanced resources at their disposal. These aren't some high schools kid in their parents' basement. Today's attacker usually spends 200+ hours curating all the resources and workflow of an attack. How many hours have you spent to secure your environment?
2. Locky Attack Infrastructure: A typical Locky attack includes a command-and-control apparatus and a network of zombie computers (aka botnet). The command-and-control apparatus executes the workflow of the attack, while the botnets are a set of servers that have been compromised (unbeknownst to their owners) to send out millions of e-mails to the individuals who are targeted in the attack.
3. Start Campaign: Attacks are organized into campaigns, and the command-and-control apparatus launches a campaign by directing the botnets to start sending out infected e-mails to targets.
4. Update Payload: The Attacker knows the target e-mail servers will eventually block infected e-mails. Therefore, the attacker configures the command-and-control apparatus to morph the attack signature (aka update the attack payload) of the infected e-mails as the botnets continue to send them out. The attack signatures can morph as quickly as every five minutes, making it very difficult for target e-mail servers to identify any single attack signature and prevent the delivery of infected e-mail messages.
5. Distribution of the Ransomware: When an infected e-mail is successfully delivered to a targeted individual, and the target subsequently opens the attachment and enables macros, malicious code is executed, which saves a downloader application to the machine and communicates back to the command-and-control apparatus to download the encryption code.
6. Activating the Ransomware: Once the code starts encrypting, the command-and-control apparatus delivers the encryption code to the target's machine and encryption commences. At this point, the target computer is now owned and the user is completely locked out.
The Evolution from Locky to Osiris
Locky is an extremely sophisticated piece of ransomware that keeps evolving. As of April 2017, the latest iteration is known as Osiris (named for the Egyptian god). There are at least seven known iterations of the ransomware since it was discovered in February 2016. Each iteration is noted by the file extension used on encrypted files:
- .locky -- February 2016
- .zepto -- June 2016
- .odin -- September 2016
- .shit, .thor -- October 2016
- .aesir -- November 2016
- .zzzzz, .osiris -- December 2016
Each iteration of the ransomware is more efficient, adding new features such as: dynamic command-and-control IP addresses, stronger encryption, and new infected message formats that get delivered and clicked through by targeted individuals.
Strategy to Protect Office 365
Now that you understand how this ransomware works, what can you do to protect your Office 365 environment and your users? It requires a comprehensive strategy to mitigate as many vulnerabilities as possible and to quickly detect and respond to a successful attack. Defense in breadth mitigates the vulnerabilities in your defense products and services, user training mitigates human vulnerabilities, and continuous monitoring allows you to detect and respond to successful attacks. Let's look at each of these components closer.
Defense in Breadth
Defense in breadth is accomplished by implementing multiple defense systems simultaneously. Theoretically, the use of multiple defense systems will make it more difficult for a ransomware attack to succeed. Because the Osiris/Locky attack is perpetrated through spam/phishing message delivery, you need a defense-in-breadth strategy that mitigates the delivery of spam/phishing messages. Accordingly, you should implement the Office 365 services listed in Table 1.
| Office 365 Service |
Feature Descriptions & Recommendations |
| Exchange Online protection |
DKIM/SPF/DMARC: Domain-based Message Authentication, Reporting and Conformance (DMARC) works with Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) to authenticate mail senders and ensure that destination e-mail systems trust messages sent from your domain. You should manually configure and implement all three services for your default Office 365 domain. A Microsoft TechNet article describes how to use DMARC to validate e-mail in Office 365.
Enable Common Attachment Types Filter and Notifications: Office 365 does not block the delivery of potentially malicious file types (.exe, .vbs, reg, etc.) by default. You must manually enable the Common Attachment Types Filter under Exchange Admin | Protection | Malware Filter. Also, enable Notifications to be sent to the administrator when a message is marked as spam and determined to be undeliverable.
Verify list of allowed/blocked IPs: If an attacker infiltrates your Office 365 environment, he might add IP addresses to the allowed IPs list or remove IP addresses from the blocked IP list. Check these lists under Exchange Admin | Protection | Connection Filter periodically to ensure that the allowed/blocked IP lists have not been molested.
Verify block/allow list in Spam Filter: Check the block/allow lists under Exchange Admin | Protection | Spam Filter. |
| Advanced Threat Protection (ATP) |
Use the new Advanced Threat Protection (ATP) to help protect inbound and outbound messages from malicious software and spam. You also use threat management to protect your domain's reputation and to determine whether senders are maliciously spoofing accounts from your domain.
Safe attachments: When enabled, e-mail attachments are opened in a special, isolated environment that's separate from Office 365 before they're sent to recipient inboxes. Safe attachments are designed to help detect malicious attachments even before anti-virus signatures are available. To learn more, see how the Safe attachments feature works in Office 365.
Safe links: Safe links helps prevent users from following links in e-mail or in Office documents that link to Web sites recognized as malicious. Microsoft outlines how to use Safe links in Office 365 on the Office Support site. |
Table 1. Recommended Office 365 services that should be implemented for a defense-in-breadth strategy.
|
User-Awareness Training
One of the most effective but underutilized strategies for defending your network against malware such as Osiris/Locky is user-awareness training. Because it's impossible to catch all malware, your users are the last line of defense for your network, and they should be trained as such. Accordingly, you should implement the following user-awareness training strategies:
- Threat awareness: Have your users take refresher courses on how to identify a phishing attempt and the importance of their participation in the fight to defend resources against malware once every quarter. Specifically, they must learn not to engage with any suspicious e-mail, report suspicious e-mail, and ensure that their endpoints are protected with anti-malware software and effective backups. It might sound simple, but many users still aren't aware of this.
- Phishing Simulators: A very effective method of user training is the implementation of a phishing simulator. There are several free phishing simulator options available that allow you to create a simulated phishing campaign that you can send to your users. Those who fall victim to the simulation will be impacted far greater than any passive training course could ever achieve. Of course, you must obtain the proper permission from all authoritative stakeholders before pursuing this type of training.
Continuous Monitoring
Finally, you must continuously monitor your Office 365 environment. Sadly, your environment or one of your users will fall victim to malware at some point, and continuous monitoring enables you to shorten the attack time and hopefully mitigate the impact of the attack. You should monitor your Office 365 environment in the following manner:
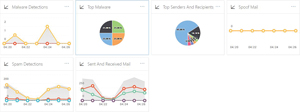
- Check Security & Compliance reports weekly: The Reports Dashboard in the Security & Compliance Center (see Figure 3) has a host of reports that you should check on weekly.
- Check Secure Score reports weekly: Reports that should be reviewed weekly include the following:
- Sign-ins after multiple failures report
- Sign-ins from unknown sources report
- Sign-ins from multiple geographies report
- Mailbox access by non-owners report
- Malware detections report
- Sign-in devices report
- Account provisioning activity report
- Non-global administrators report
 [Click on image for larger view.]
Figure 3. The Reports Dashboard tracks issues such as malware, mail spoofing and spam detections.
[Click on image for larger view.]
Figure 3. The Reports Dashboard tracks issues such as malware, mail spoofing and spam detections.
- Subscribe to Threat Intelligence: Microsoft's new Office 365 Threat Intelligence became generally available in April (see "Microsoft Adds Protection to Office 365"). This is a fantastic continuous-monitoring service that provides:
- Interactive tools to analyze prevalence and severity of threats in near-real time
- Real-time and customizable threat alert notifications
- Remediation capabilities for suspicious content
- Expansion of Management API to include threat details -- enabling integration with SIEM solutions
Implementing these strategies will reduce the risk of Office 365 being the source of a ransomware attack. But even if you apply all these steps, it's not a guarantee that individuals in your environment will fall victim to Osiris/Locky, or other ransomware variants or malicious attacks. But it should markedly reduce the risk.