In-Depth
How To Say Goodbye to Passwords
Eliminating passwords by configuring settings and policies with Windows Hello or the picture-tracking option will create more secure authentication to devices and Active Directory.
While passwords are frustrating to users, they’re also the weakest links in the security chain. There are countless ways passwords are compromised. A password can be stolen by malware (especially by key loggers), users often voluntarily disclose or unwittingly do so to a tech support scammer, and some even fall victim to shoulder surfing. These methods and others reveal just how insecure passwords really are.
Yet most users still rely on passwords, even though there are alternatives, especially for those with Windows 8.1- and Windows 10-based PCs. Both versions support picture passwords, while Windows Hello emerged on the scene in July 2015 with the launch of Windows 10. With either method, the authentication process is based on something other than a password. Using a password alternative is more secure than a complex password. To use them effectively in a business or enterprise environment, there are some important but relatively simple steps you can take.
Picture Passwords
Microsoft introduced alternatives to traditional passwords with Windows 8 and picture passwords. With a touchscreen PC, you can use a finger to doodle on the Windows wallpaper and that doodle becomes your password. It’s possible to use a mouse to complete a picture password on a non-touchscreen device, but doing so is somewhat awkward.
So how do picture passwords work? Suppose a user’s wallpaper has a picture of the Luxor Hotel in Las Vegas, complete with its pyramid and sphinx. A user might trace the sides of the pyramid with a finger and then circle the head of the sphinx. Those gestures become the user’s password. To log into the computer, the user not only performs the doodle, but draws the picture-password elements in the same way they were originally performed (the same sequence, and in the same direction).
Picture passwords are similar to verifying a signature. Everyone’s signature is unique. When people sign their names, they form the letters in a certain way, holding the pen at a specific angle, while applying a certain amount of pressure on the paper. The result is something that’s personally identifiable. Picture passwords aren’t quite as unique or as sophisticated as a person’s signature, but they use some of the same characteristics.
On the surface, doodling on the screen hardly seems like a secure way of authenticating into the system. However, picture passwords are resistant to many forms of password theft, because there’s no password to steal. It’s conceivable a picture password could be stolen through shoulder surfing, but other methods such as keystroke logging or social engineering wouldn’t work.
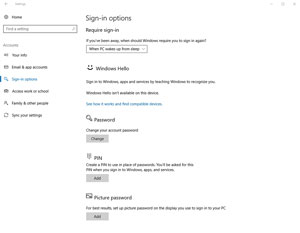
Picture passwords also work with Windows 10. Just open Settings, click on the Accounts option and then click the Add button found in the Picture Passwords section (see Figure 1). The Sign-in options screen contains a few other options.
 [Click on image for larger view.]
Figure 1. Windows 10 can be configured to use picture passwords.
[Click on image for larger view.]
Figure 1. Windows 10 can be configured to use picture passwords.
Windows Hello Settings
Microsoft’s preferred authentication for Windows 10 is via Windows Hello. Using its biometric authentication, a user can log in to Windows with facial, fingerprint or even iris recognition. This, of course, raises several questions.
First, how is it possible for a Windows device to perform biometric authentication? By going into the Windows 10 Sign-in options, as shown in Figure 1, a message states that Windows Hello isn’t available on my device. That’s because Windows Hello requires special hardware in order to work. If your laptop features a built-in fingerprint reader, then you can use that fingerprint reader with Windows Hello. Likewise, the Microsoft Surface Pro 4 and Surface Book are specifically designed to work with Windows Hello. If you don’t happen to have one of these devices or want to ensure PCs purchased for your employees support Windows Hello, Microsoft lists those that support it. As of early March, the tally was at 55 devices, and that number is expected to rise over time.
The Windows Hello signature feature is its ability to authenticate a user based on facial recognition. Even though facial recognition is new to Windows Hello in Windows 10, it has existed in consumer electronic devices for quite some time. Roughly 10 years ago, some of the higher-end digital cameras began to include face-detection software. This software would recognize faces within the frame, and then lock the auto focus onto those faces. Eventually, the facial detection software became more sophisticated. Some camera manufacturers, for instance, have designed software that can tell whether the person who’s being photographed is smiling.
As handy as these types of features can be, however, they aren’t perfect. My digital SLR will sometimes lock the camera’s auto focus on a person who is standing in the background, rather than the person I’m trying to photograph. I have also seen the camera’s face detection feature lock in on billboards or other media containing a picture of someone’s face.
This may raise the concern that it’s easy to fool Windows Hello by showing the computer a photograph of the person whose identity you’re trying to spoof. Fortunately, this is not how Windows Hello works.
If it were that easy to spoof an identity using a photo of someone’s face, the PC that doesn’t support Windows Hello might be able to invoke that feature. Microsoft requires a camera (either built-in or external) that’s specifically configured for near infrared (IR) imaging, which authenticates users to access Windows-based systems and Microsoft Passport accounts. The facial recognition authentication is based on what Microsoft has defined as the enterprise-grade identity verification mechanisms built into Windows 10, which are integrated into the Windows Biometric Framework.
As such, facial recognition will only work if the device is equipped with effectively a 3-D video camera with a near IR sensor engineered to Microsoft’s specifications, similar to the Xbox Kinect motion-sensing device. Because the camera is able to capture a user’s face in that third dimension, Windows Hello can tell the difference between a real person and a 2-D photograph. Microsoft has engineered very specific requirements for sensors in cameras to authenticate users to Windows, enterprise resources and networks and recently published an update.
The use of biometric authentication raises some serious concerns about personal privacy, but Windows takes steps to keep biometric information secure.
In the in settings in Figure 1, Windows offers the option to log in with a PIN. A PIN is just a short numeric code. It’s far shorter -- and much less complex -- than a password, so why does Microsoft provide the option to use it? Because the PIN-based authentication works at the device level. In other words, the PIN is never transmitted as part of the authentication process, and it cannot be used to log into another device. The PIN only works on the device it has enabled. Therefore, knowing someone’s PIN is not of any use, unless you also happen to be in physical possession of the device.
This same basic principle applies to biometric authentication through Windows Hello. Like a PIN, using Windows Hello is completely optional. If biometric authentication makes you uncomfortable, then you don’t have to use it. Instead, you can opt to use a regular password, a picture password or a PIN.
When setting up Windows Hello, Windows doesn’t take a photograph of your face, iris or fingerprint. Instead, Windows looks at your unique characteristics and then forms a numeric representation of those characteristics. This numeric hash is local to the device. Like a PIN, the hash is never transmitted, and cannot be used to log into other devices.
Also, the algorithms to create the numeric data used by Windows Hello are unique to Windows. If someone could extract the codes from a Windows PC, they wouldn’t be able to "reverse engineer" the codes to produce an image of someone’s face, fingerprints or iris. Also, they’d be unable to use the codes to gain access to a non-Windows biometric device because the codes are created using an algorithm that only Microsoft uses.
Although Windows Hello is designed to be something users can enable on their own, it’s possible to use Group Policy (or an MDM policy) to enforce or restrict its use. The Group Policy settings are located under both User Configuration and Computer Configuration at: Policies | Administrative Templates | Windows Components | Windows Hello for Business.
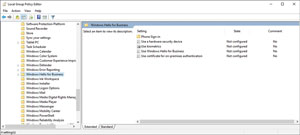
The Group Policy settings exposed for Windows Hello vary depending on whether you implement the policy settings at the user level or the computer level. When implemented at the computer level, Group Policy settings can be used to configure phone sign-in, the ability to use hardware as a security device and biometric support. There are also settings to enable Windows Hello for Business and to use certificates for on-premises authentication (see Figure 2).
 [Click on image for larger view.]
Figure 2. These are the Windows Hello for Business Group Policy settings exposed as part of the computer configuration.
[Click on image for larger view.]
Figure 2. These are the Windows Hello for Business Group Policy settings exposed as part of the computer configuration.
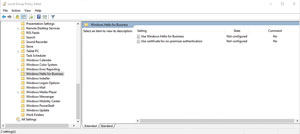
If you opt to implement Group Policy settings through User Configuration, then the Windows Hello for Business settings that are exposed are limited to enabling Windows Hello for Business, and using certificates for on-premises authentication (see Figure 3).
 [Click on image for larger view.]
Figure 3. The Windows Hello for Business Group Policy settings exposed as part of the User Configuration.
[Click on image for larger view.]
Figure 3. The Windows Hello for Business Group Policy settings exposed as part of the User Configuration.
Other Options
Microsoft’s documentation offers additional group and MDM policy settings for organizations configuring Windows Hello. Organizations can also now use Windows Hello to authenticate to the cloud using Azure Active Directory Connect (see "Synchronize Directories with Azure AD Connect"). With the release of the Windows 10 Creators Update, organizations will be able to use Windows Hello with Active Directory on-premises environments.
Another new feature, Dynamic Lock, will automatically lock a PC if a user is out of proximity of the system. It uses Bluetooth signals, and can also be enabled through policy or system settings.
Later this year, Microsoft has said Windows Hello will support Intel Corp.’s new Authenticate hardware-based solution. That will enable multi-factor authentication, which more organizations are considering for added layers of security.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.