In-Depth
Prevent Data Leakage with Windows Information Protection
Windows Information Protection is among many new security features introduced in last year’s Windows 10 Anniversary Update release, bringing data loss prevention to the OS.
Among the numerous security improvements Microsoft added to Windows 10 last summer, administrators can now create policies in the OS aimed at reducing data leakage. Windows Information Protection (WIP) brings data loss prevention (DLP) capabilities, mobile device management (MDM) and other security tools to the OS for the first time. Microsoft added WIP, a feature known as endpoint data protection (EDP) prior to its release, with the Windows 10 Anniversary Update.
Any organization considering a Windows 10 migration should evaluate WIP, especially if your organization has done little to prevent data leakage.
It’s no secret how easy it is for an employee to copy files onto a USB drive or to a personal online cloud service such as iCloud, Google Drive, Dropbox, and OneDrive, or even social media sites including Facebook, LinkedIn, and Twitter. Despite the ease of doing so, many organizations do little to prevent it. WIP is one easy way to do so, whether you have Office 365 or an MDM tool.
WIP isn’t a replacement for BitLocker disk encryption, which protects data on behalf of the user. But BitLocker doesn’t stop an authorized user from intentionally or inadvertently decrypting and moving files. WIP lets administrators invoke copy and paste protection, segment personal from corporate data, provision policies, and selectively wipe corporate data. Data coming in from an enterprise network node is automatically protected by WIP. Once WIP is configured, business data can only be stored on approved devices or even within approved applications.
A Key WIP Requirement
There is a catch. To create policies using WIP, administrators must use System Center Configuration Manager (SCCM) or Intune, the Microsoft cloud-based management tool, available with either a standalone subscription or though the Microsoft Enterprise Mobility + Security (EMS) bundle. Microsoft claims more than 30 million EMS subscriptions, suggesting Intune is widely used, making WIP accessible to administrators rolling out the latest version of Windows 10. Using Intune, I’ll describe how to create polices using the WIP capabilities and to what extent, if any, these features are unique to those deploying Windows 10.
Configuring WIP
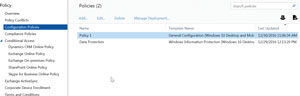
WIP is configured using policies to enable the selections that match the needs of an organization (see Figure 1).
 [Click on image for larger view.]
Figure 1. Configuration Policies.
[Click on image for larger view.]
Figure 1. Configuration Policies.
To configure a WIP policy, complete the following steps:
- Log in to manage.microsoft.com with your Windows Intune administrative account.
Note: Microsoft Edge is not supported by the Intune service as of this writing, so plan on using an alternate browser.
- In the navigation strip on the left, select Policies.
- Within the main window, select Add Policy.
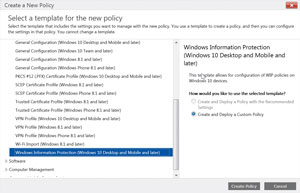
- In the Create a New Policy dialog, expand Windows and select Windows Information Protection, then choose Create and Deploy a Custom Policy (see Figure 2).
 [Click on image for larger view.]
Figure 2. Select the Windows Information Policy template.
[Click on image for larger view.]
Figure 2. Select the Windows Information Policy template.
- Click Create Policy.
- Enter a Name for the policy.
- Enter an optional description for the policy.
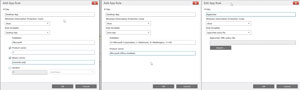
- Specify some App Rules by clicking Add under the App Rules section and completing the dialog.
- Specify a name for the rule.
- Choose the Windows Information Protection Mode.
- Allow -- enable protection.
- Exempt -- disable protection.
- Choose a rule template.
- Store App -- creates a rule for Windows Store apps.
- Desktop App -- creates a rule for a Desktop Application.
- AppLocker policy file -- creates a rule for an AppLocker configured item.
- Publisher -- specify the application publisher for the rule (that is, O=Microsoft Corporation, L=Redmond, S=Washington, C=US).
- Product Name -- specify the product name for the rule.
Windows Store apps require publisher and product name, while desktop apps require publisher, product name, binary name and version number -- the dialog box will change depending on the item type chosen for the rule.
All of these options for desktop applications support Wild card values. For AppLocker policy files, an XML file must be specified for upload.
- Choose the sharing and paste options for the policy.
- Block -- prevents copy/paste, drop and share options for attempts to move data out of the enterprise.
- Override -- prevents copy/paste, drop and share options for attempts to move data out of the enterprise while logging the operations for audit.
- Silent -- Allows copy/paste, drop and share options for attempts to move data out of the enterprise while logging the operations for audit.
- Off -- Disables Windows Information Protection.
Specify the corporate identity (used to tag and identify the data belonging to an organization -- that is, yourcompany.com).
Add corporate network or SharePoint locations to monitor for corporate data (that is, yourcompany.com | files.yourcompany.com -- using the pipe as a separator) by clicking Add.
- Specify a name for the network definition.
- Select the type of resource for the definition:
- Enterprise Cloud Resources
- Enterprise Network Location
- Enterprise Proxy Servers
- Enterprise Internal Proxy Servers
- Enterprise IPv4 Ranges
- Enterprise IPv6 Ranges
- Neutral Resources
Specify the path to the resource.
Click OK to save the location.
Upload a certificate to allow for recovery of encrypted data. Microsoft described how to create and verify an Encrypting File System (EFS) Data Recovery Agent (DRA) certificate in a recent post.
Configure any of the additional settings required by the organization:
- Show the Personal Option from the file ownership menus in the Windows File Explorer and the Windows Save As Dialogs -- allows specification of Work or Personal during Save As or from File Explorer.
- Prevent corporate data from being accessed by apps when the device is locked.
- Revoke encryption keys on unenroll.
- Allow Windows Search to search encrypted corporate data and store apps.
- Show the Windows Information Protection overlay.
Click Save Policy to store the configuration you’ve created.
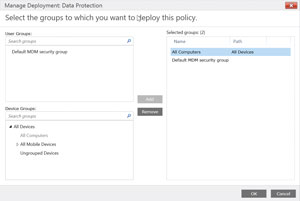
With the policy created and saved, all that’s left is the application of the policy to enrolled devices. As with all configuration items managed by EMS, groups of devices (or users) can be used to handle application of items. It lets administrators create groups for application of policies, updates and other management items (see Figure 4).
 [Click on image for larger view.]
Figure 3. App Rules configuration.
[Click on image for larger view.]
Figure 3. App Rules configuration.
 [Click on image for larger view.]
Figure 4. Policy application groups.
[Click on image for larger view.]
Figure 4. Policy application groups.
After the application of policies, items are queued until the next application refresh. Given the shift to more mobile workforces and support for BYOD, more organizations have implemented or are looking at configuration and data management tools such as EMS to ensure the security and safety of corporate data. In addition, the ability to use the devices provided by an organization for projects outside the company is helpful to employees as it enables many things without worrying that the documents or items created land on corporate servers. WIP is a good start.
File-Level Integrity
WIP not only manages information on your corporate Windows laptops to keep information secure and PC images consistent, but can also ensure file-level integrity. Take the common scenario where an employee is on vacation with her family and an important work task lands in her inbox. Because the only device available is a personal iPad, she logs in to check the e-mail.
Opening a link to a document stored on the company SharePoint server downloads the document to her device, which she opens in Word. What does WIP provide in this situation? The enrolled application -- Word, in this case -- will allow her to save her edits to the document back to company servers, but the document cannot be stored locally on the application. WIP allows personal devices to view information, but doesn’t allow documents originating from managed locations to be stored locally on a personal (non-managed) device.
While this may encourage a more accessible workforce because any device can accommodate a login to access files, keeping the data safe and disallowing local storage of the document is the overall goal.
Options and Pricing
Intune supports WIP features on its own, as part of EMS or as part of Office 365. The various options are outlined by Microsoft here. The lowest-cost option for those that don’t already use SCCM is Intune, which starts at $6 per user per month. It includes the cloud-based SCCM client, 20GB of storage for application distribution, PC endpoint protection, the ability to create and manage security policies, monitoring and alerts, software distribution, mobile device app publishing and inventory policies. Other Intune options are outlined on Microsoft’s price list.
Recommendations
Letting IT departments manage employees’ mobile and personal devices provides many benefits. By properly ensuring updates and patches for OSes and the applications required by the business, the devices become less likely to be compromised in general. Adding WIP to the equation will ensure that data is kept where it belongs, inside the business, while still allowing personal data to be stored locally as needed.
The additional abstraction of security of information from devices should bring peace of mind to business owners by ensuring that information is protected separately from the corporate (and personal) devices it may reside on -- making a device that much more of a commodity item. While it’s not a perfect solution, implementing WIP with Windows 10 is definitely a step forward in keeping data more secure.
About the Author
Derek Schauland has worked in technology for 15 years in everything from a help desk role to Windows systems administration. He has also worked as a freelance writer for the past 10 years. He can be reached at [email protected].