In-Depth
Microsoft Makes the Case for Windows Server 2016
The company showcased the latest Windows Server improvements in security, cost savings and cloud-based app management.
Microsoft largely skipped outlining Windows Server 2016 during its September Ignite keynote talk, but it did offer a broad outline this month.
The details were spelled out in a talk by Jeffrey Snover, a Microsoft technical fellow and chief architect, Jeff Woolsey, a principal program manager for Windows Server, and Erin Chapple, a partner director of program management. Chapple offered high-level views of Windows Server 2016, while Woolsey offered technical details. Snover added overall perspective, including some possible "Snoverisms."
The full hour-long talk can be found in a Microsoft-produced "Introducing Windows Server 2016" webinar, originally aired on Oct. 13. It's available on demand here.
Snover said that Microsoft's Windows Server customers were primarily seeking help in three areas: addressing security threats, datacenter costs and application innovation. Microsoft's Windows Server 2016 developments were influenced by technologies used to run Microsoft Azure, the company's worldwide datacenter services operations, he added.
Security Perks
The starting point of the presentation was the security benefits of Windows Server 2016. Chapple said Microsoft added "layers of security" in Windows Server 2016. The idea is to shorten the time between attacks and detecting security breaches.
"From the time between the first host is compromised, it really is only between 24 and 48 hours between that and when the main admin is compromised," Chapple said. Breaches typically go undetected for an average of 200 days, she added. Microsoft sees protecting identity as key, along with protecting the operating system and assuring that it's running what you want it to run.
Woolsey warned IT pros to be on guard against phishing attacks. Attackers use org charts to try to divert end users toward malicious Web sites to gain access to corporate sites. Next, given a foothold, an attacker might conduct pass-the-hash exploit attempts to escalate privileges on a network. Woolsey asserted that administrative credentials are provided far more than necessary on networks. IT pros should enforce login policies that keep users with standard user access privileges 99 percent of the time, he added.
Microsoft added technologies in Windows Server 2016 to provide such protections. For instance, Credential Guard is designed prevents pass-the-hash and pass-the-ticket attacks. There's also Remote Credential Guard, which mitigates those threats when logging in remotely. There also are some constraints on administrator access privileges using PowerShell with Just Enough Administration and Just-in-Time Administration. A temporary account is provided with access to just the privileges needed to complete the task. These measures can be used to "guard-rail new administrators," Woolsey added. And it's audited, so it's possible to see who made network changes and when.
"Admins are an attack surface," Snover commented, regarding those security measures. Chapple explained that Microsoft was adding best practices on the back end with those security additions.
Here's Microsoft's slide on the credential protections enabled in Windows Server 2016:
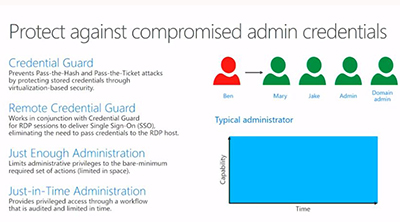 [Click on image for larger view.]
Figure 1. Admin credential protections in Windows Server 2016. Source: Microsoft.
[Click on image for larger view.]
Figure 1. Admin credential protections in Windows Server 2016. Source: Microsoft.
Another security feature is the ability to set code integrity policy with Device Guard. It assures that the only thing that can run on Windows Server 2016 is what has been white listed. Only the permitted binaries can run at bootup.
"Most importantly, it [Device Guard] protects an admin from another admin installing something later that they shouldn't be running," Woolsey said.
Windows Server 2016 also includes Windows Defender. As with the client operating system, Windows Defender in Windows Server 2016 protects against known malware. However, it's also possible to use third-party antimalware solutions as well with Windows Defender on Windows Server 2016.
Windows Server 2016 also has Control Flow Guard. It's a security feature designed to deter unknown exploits that was introduced in Windows 8.1 and Windows Server 2012. Control Flow Guard protects against classes of memory corruption attacks.
Microsoft also added Shielded Virtual Machines to Windows Server 2016. It guards against security breaches that can happen internally when a virtual machine (VM) gets copied. Woolsey explained that once an infiltrator gets into a host, essentially the whole virtualization fabric has been compromised. An attacker can own your entire VM infrastructure by simply copying the VM.
"That's another thing about virtualization -- we made it really easy to steal workloads," Woolsey said.
A VM is literally a couple of files, he added. With Microsoft's Shielded Virtual Machines feature, a stolen VM can't be run it because it's an encrypted Blob.
Shielded Virtual Machines represents a "whole new world of protection for virtualization that doesn't exist on any platform in the world, quite simply," Woolsey claimed.
"Yeah, this is a game changer," Snover agreed.
Chapple stated that Shielded Virtual Machines also provides defense in depth within an enterprise because it can protect an organization's Active Directory.
"If you have a mission-critical workload -- your domain controller, your PKI server, your search servers, all of these things -- there is absolutely no better way to run it than to virtualize it using shielded Virtual Machines," Woolsey added.
The Host Guardian Service role in Windows Server 2016 is part of the Shielded Virtual Machines protection scheme, Woolsey said. It's used as an attestation service for the host. It only runs healthy workloads.
"The Guardian Service is actually running in a separate domain of the infrastructure," Woolsey said. "It actually attests to the fabric. So it makes sure that when a Hyper-V Server booted up, it actually went though the boot process; it actually tested and attested and measured the boot process. When it actually booted, it then checked the code integrity policy. Are you running only things that are allowed via the code integrity? Does code integrity pass? And then finally we can also check for things like debuggers. If we see a debugger on one of these, we know that perhaps someone is trying to do something they shouldn't be doing, like trying to inspect memory or something like that. If it doesn't pass the test, then the Shielded VM cannot start on that server."
Shielded Virtual Machines each have an encrypted virtual TPM, which protects the key for each virtual disk. They're a black box for fabric admins and are controlled by the admin of the guest OS, Woolsey said.
Microsoft illustrated the Shielded Virtual Machines and Host Guardian Service features in this slide.
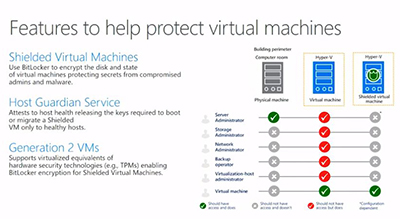 [Click on image for larger view.]
Figure 2. Shielded Virtual Machines in Windows Server 2016. Source: Microsoft.
[Click on image for larger view.]
Figure 2. Shielded Virtual Machines in Windows Server 2016. Source: Microsoft.
Networking Benefits
Next, the Webinar focused on Windows Server 2016's networking benefits.
Chapple said that Windows Server 2016 includes datacenter efficiency technologies. It has enterprise-class virtualization, software-defined storage and software-defined networking capabilities.
Woolsey noted that Microsoft took learnings from running its Azure datacenters and added it to Windows Server 2016. The Windows Server Hyper-V hypervisor is an example, as it's used for Azure virtualization, too.
Microsoft, in devising Windows Server 2016, found that its customers were looking at running large-scale workloads. In Windows Server 2016, Microsoft added up to 24TB of RAM per physical server and 512 Logical Processors. The VM memory was boosted to 12TB in a VM. Windows Server 2016 supports up to 240 virtual processors in a VM, and that's true for both the Standard and Datacenter editions, Woolsey said.
Microsoft showed the following slide, comparing the Hyper-V scalability stats between Windows Server 2016 and its predecessor:
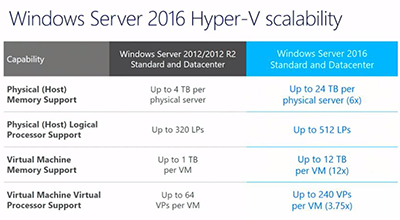 [Click on image for larger view.]
Figure 3. Hyper-V stats for Windows Server 2016 vs. Windows Server 2012. Source: Microsoft.
[Click on image for larger view.]
Figure 3. Hyper-V stats for Windows Server 2016 vs. Windows Server 2012. Source: Microsoft.
Microsoft also did some work in clustering and resiliency in Windows Server 2016. The new server has a cluster OS rolling upgrade feature without downtime. It also supports interoperability with Windows Server 2012 R2 cluster nodes. For cloud environments, Microsoft is promising VM resiliency during network or storage disruptions. Windows Server 2016 also has "fault domain-aware clusters," per Microsoft's slide:
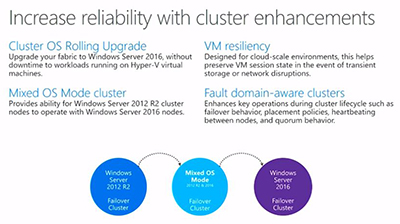 [Click on image for larger view.]
Figure 4. Cluster enhancements in Windows Server 2016. Source: Microsoft.
[Click on image for larger view.]
Figure 4. Cluster enhancements in Windows Server 2016. Source: Microsoft.
Also, load balancing is built into Windows Server 2016 now. In the past, it was a feature of System Center. Now it's in there and it's on by default in Windows Server 2016, Woolsey said.
"We are designing the drama out of your server," Snover commented.
Storage Improvements
Windows Server 2016 has a Storage Replica feature that "allows us to create stretched clusters," Woolsey said. It creates "affordable business continuity and disaster recovery in the box for the first time," Woolsey said.
For datacenters with tenants sharing resources, there's a Storage Quality of Service feature to protect high-priority workloads. It provides "service level agreements and drives policy for virtual machines so an important VM never gets starved for resources," Woolsey said.
One "key lynch pin" of Windows Server 2016 storage is its Storage Spaces Direct feature. It provides "a super high-speed infrastructure way to replicate all of my storage and make it simple and easy to deploy," Woolsey said. Storage Spaces Direct uses common hardware to create software-defined storage resources that can scale. It took its learnings from Azure, he added.
"This is a great example of where we took lessons from Azure and we bring them on premise," Snover commented. "Here we are decreasing the cost because we're using more commodity products; using more standardized components -- Ethernet vs. storage fabric; and we're increasing the availability and reliability because of it. That is using the magic of software to give you gold-plated SLAs on pretty common stuff."
Cosmos Darwin, a program manager on Microsoft's high availability and storage team demonstrated Storage Spaces Direct. He said it takes "15 minutes to deploy."
There was some talk of Windows Server 2016's software-defined networking capabilities. They are listed in the following slide:
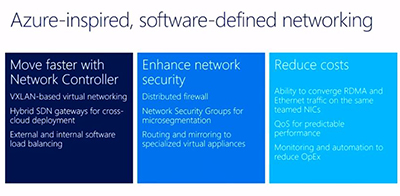 [Click on image for larger view.]
Figure 5. Software-defined networking in Windows Server 2016. Source: Microsoft.
[Click on image for larger view.]
Figure 5. Software-defined networking in Windows Server 2016. Source: Microsoft.
On the hardware side, organizations can use Ethernet, a fiber channel SAN or NAS storage with Windows Server 2016. Snover noted that organizations should just be sure that the system's NICs support RDMA when they buy server hardware. "RMDA is the thing that makes SMB 3 just rock," he said.
Woolsey explained that in a hyperconverged solution, when VMs are working, the CPUs have to replicate storage across the servers. If the VMs get really busy and there is a lot of storage, it can affect the CPUs and the density of the VMs that can be run. With RDMA, it's possible to deliver spectacular performance with little to no CPU overhead so that it doesn't affect overall density.
Microsoft also explained a bit about its software-defined networking efforts. With Windows Server 2016, Microsoft has been bringing the Azure data plane on premises, Woolsey said. Microsoft is supporting VXLAN based virtual networking as well as NGVRE.
Microservices and Containers
Chapple said that an application transition is happening from legacy apps to cloud-native apps and microservices. And a new infrastructure is needed to support that transition. Support is needed to help automate Dev-Ops workflows as well, she added.
"Microservices are the rage," Snover said. "And the question is why, and you hear lots of answers, but from an architect's point of view the heart of it is environmental decoupling."
Snover explained that components typically have been integrated from different places using DLL calls or local RPC calls all on the same machine. They either shared the same environment in terms of the same process or the same environment in terms of the same OS. As one component needed a change, it would affect the other components or break them. But environmental decoupling became enabled by great networking. With fast networks that have low latency, protocols can be used for integration instead of local DLL calls. These protocols can run in their own environment.
"Once you deal with things through the protocol level instead of the DLL level, it gives everyone the capability of being awesome in and of themselves to meet their potential and to not necessarily be dated by the other person," Snover explained. It permits different software release cycles to run, he added.
Woolsey said that containers are a large investment with this Windows Server 2016 release. While some people are saying that containers are a great thing, others say it's going to kill virtual machines. However, Woolsey said that they are "two different things." Traditional VMs have hardware virtualization emulating motherboard, storage and the like, but containers are a different thing.
"Essentially containers are what we call operating system virtualization," Woolsey said. "The applications are running and they're all talking to a shared kernel. And you're getting extra sandboxing protection around them, so when an app is talking to a kernel, it thinks it's the only thing running on the system."
Those capabilities allow IT to spin up containers quickly. It's like a replacement for installers. And it helps developers with agility, Woolsey added.
Containers share a kernel, and that's fine if it's running in your own infrastructure and you know the actors, Woolsey said. But regulatory officials may not like the idea of shared kernels. Consequently, Microsoft came up with two types of containers: Windows Server Containers (traditional shared model) and Hyper-V Containers (which doesn't share the kernel), which are integrated with Docker technology (see slide):
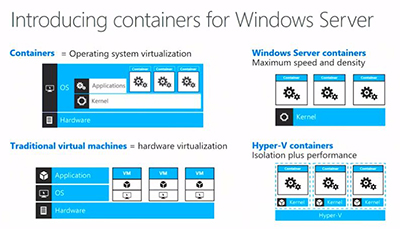 [Click on image for larger view.]
Figure 6. Containers in Windows Server 2016. Source: Microsoft.
[Click on image for larger view.]
Figure 6. Containers in Windows Server 2016. Source: Microsoft.
"If you're deploying in a public cloud, you going to want to use Hyper-V containers," Woolsey said. "If you're deploying on premises, depending on what the workload is, if it's test dev or if it's production but if it's not under compliance or regulatory, maybe Windows Server Containers are great. Go use them. If you need that extra level of protection in your enterprise because you've got compliance regulatory concerns, great, just use Hyper-V Containers and it gives you that max layer of isolation."
There was also talk about Nano Server, Microsoft's newest minimal-footprint install option on Windows Server 2016. It's an option for organizations that use containers or that develop modern applications (see slide):
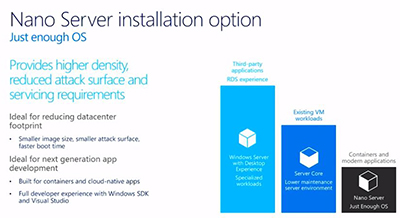 [Click on image for larger view.]
Figure 7. Nano Server and other Windows Server 2016 install options. Source: Microsoft.
[Click on image for larger view.]
Figure 7. Nano Server and other Windows Server 2016 install options. Source: Microsoft.
Nano Server is about 480MB fully installed in a VM, compared with 5GB on disk for the Server Core option, Woolsey said. Nano Server can be deployed in a container or a VM. You can also deploy Nano Server on the metal itself, which is the most optimal option. Nano Server also can be used as a scale-out file server.
One of Microsoft's customers, Tyco Security, is using Windows Server Containers, which allows its applications to work without conflicts. It has deployed 1,000 containers, which helps it scale its mission-critical systems. These details were described in a video during the presentation.
Snover added a last note to the talk.
"Windows Server 2016 is great for the cloud, but it's also great for those other areas," Snover said. "It's a great enterprise server. It's a great datacenter server. And it's a great server for the masses."