In-Depth
What's New in Windows Server 2016 TP5 Hyper-V
Better backups, checkpoints and security are highlights of the latest version.
The recent release of Microsoft Windows Server 2016 TP5 offers a closer look at the likely capabilities and features coming to the final release of the server OS, which, among many new features, includes an improved version of its Hyper-V virtualization technology. I say likely because TP5 is apparently feature-complete; it's also the last preview before release to manufacturing (RTM), expected sometime in the second half of this year. Among the many new features in Windows Server 2016, many IT pros are looking to see new capabilities in Hyper-V.
While Hyper-V has been around since 2008, Microsoft has taken a new approach to enhancing it with this release, according to Ben Armstrong, principal program manager of the Microsoft Hyper-V team. Armstrong discussed some of the planned new Hyper-V features in an interview late last year with Redmond sister publication Virtualization Review.
Simply put, in the past, Microsoft would develop Windows Server "in the back room" with a public beta late in the development cycle, more for fixing bugs than as a source of ideas for improvements or new features. This version of Windows, on the other hand, has been "in the open" since TP1 back in October 2014, all the way through to TP5, released April 27.
Overview of the New Hyper-V
Given the long development time, expectations are high. Fortunately, this version doesn't disappoint, with many new features, including:
- New types of checkpoints
- A new backup platform
- Rolling cluster upgrades
- Virtual machine (VM) compute resiliency
- Storage Quality of Service (QoS)
- Storage Spaces Direct
- Shielded VMs
- Windows and Hyper-V containers
- Nano Server and PowerShell Direct
There are also other improvements to existing features such as Shared VHDX, Hyper-V Replica, more online operations for VMs, a better Hyper-V manager console and more. Following is a summary of some of the key new features in TP5.
Backup and Checkpoints
Backups in Hyper-V can sometimes be a bit shaky, due to a reliance on the underlying Volume Shadow Copy Services (VSS) system. Windows Server 2016 instead makes change tracking a feature of Hyper-V itself, making it much easier for third-party backup vendors to support Hyper-V.
Snapshots and checkpoints are dangerous for production workloads. They have a convenient workflow: Take a snapshot, make some changes in the VM and, if those changes turn out badly, simply roll back to the snapshot.
The problem is that if it happens on a domain controller or database server that's replicating with other servers, it's now out of sync -- and there's no easy way to tell, nor any easy way to fix it. Microsoft made changes in 2012 for Active Directory DCs to make them safer, but this still doesn't cover any other workloads in danger from a wrongly applied snapshot.
Production checkpoints in Windows Server 2016 (the classic checkpoints can still be used) use VSS inside the VM; when you apply them, the VM will assume it's been restored from a backup and reboot, rather than be restored to a running state. This eliminates the danger while retaining the convenience of snapshots.
Rolling Cluster Upgrades
The upgrade story from Windows Server 2012 to Windows Server 2012 R2 was pretty good, enabling live migration of VMs from the old to the new. But you still had to stand up a separate Windows Server 2012 R2 cluster to start the process, which wasn't ideal.
Going from Windows Server 2012 R2 to Windows Server 2016 is a lot easier: Simply evict one cluster node, format and install Windows Server 2016, and add it back into the cluster. It now acts as a Windows Server 2012 R2 host, so VMs can be live migrated to it; that means you can take another host and clean install it. Rinse and repeat as many times as required. When all nodes are upgraded and you're sure you're not going to add any down-level nodes, you use Windows PowerShell to upgrade the cluster functional level, similar to the way you do AD upgrades.
VMs have had version numbers internally since the first version of Hyper-V. Because of the rolling-cluster upgrade scenario, they're now visible, so you need to be able to upgrade the configuration files for each VM. This is also done using PowerShell. Once upgraded, a VM can only run on Windows Server 2016 hosts. Each VM uses the new .vmcx file format for configuration and .vmrs for runtime state data; both are binary files and do not support direct editing (unlike the current XML file type).
VM Compute Resiliency
Clustering hosts together provides continuous VM availability for planned downtime; simply live migrate VMs from the host first, then perform the maintenance. For unplanned downtime, VMs on a failed host are automatically restarted on another host in the cluster, providing for high availability with a few minutes of downtime for the restart. So far, so good.
There are times, however, when host clusters can cause issues by themselves. A short network outage between the hosts can cause them to initiate a failover of many VMs, when, in fact, the network could right itself after a few seconds. Such a failover could cause more downtime, with numerous VMs restarting simultaneously.
In Windows Server 2016, if a host loses connectivity to the cluster, the VMs will keep running for four minutes (this can be changed) in "isolated mode." If it's longer, normal failover will occur. If a host has numerous disconnections over a 24-hour period, it will be quarantined and its VMs live migrated off as soon as possible.
Today, if a VM has an outage to the shared storage where the virtual disks are housed, it'll crash if the outage is longer than about a minute. In Windows Server 2016, if storage connectivity is lost, the VM will be paused, pending reconnection to its virtual disks, avoiding the likely data loss in a crash.
You can now specify priority for VMs -- high, medium and low -- when failover occurs. TP5 allows admins to create sets of VMs, define dependencies between them, and let this dictate the order in which VMs are started.
Storage QoS
In the current version of Hyper-V, you can set a min or a max (or both) value for IOPS for virtual hard disks. This works fine as long as the back-end storage can actually deliver the combined IOPS requirement for all running VMs; if it can't, there's no way for the individual hosts to manage IOPS requirements.
Windows Server 2016 brings a centralized storage IOPS "cop," sitting on the Scale Out File Server (SOFS) nodes. It's managed either through PowerShell or with Virtual Machine Manager (VMM), and provides a way to create policies that can be applied in aggregate across VMs or to individual VMs (you can read more on Storage QoS here). It also monitors the IOPS actually used by each VM, giving you a more comprehensive view of the way your applications use storage.
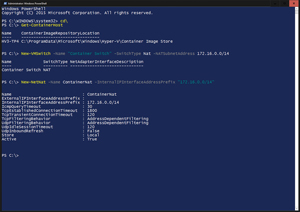 [Click on image for larger view.]
Configuration script for running Hyper-V containers in Windows Server 2016.
[Click on image for larger view.]
Configuration script for running Hyper-V containers in Windows Server 2016.
Storage Spaces Direct
Microsoft's implementation of software-defined storage (SDS) took shape in Windows Server 2012. SOFS nodes act as the front-end of a SAN (but simpler to set up and manage); SAS JBOD (just a bunch of disks) disk trays with HDDs and SSDs provide the data storage.
In Windows Server 2016, Microsoft takes the next logical step by offering Storage Spaces Direct (S2D), which provides pooling of local storage (SAS, SATA and NVMe HDDs, and SSDs) in each host, and offers it up as VM storage (you can read more about S2D here). This can either be disaggregated with storage nodes in one cluster and Hyper-V nodes in another, or hyper-converged where each host is both a storage node and VM host.
New in TP5 is the ability to have fewer than four nodes, along with support for SATA disks (previous previews required SATA disks to be connected through a SAS adapter).
Shielded VMs
One basic problem with any hypervisor is that host and/or fabric administrators have to be as trusted as the highest-level administrators in an organization. If VMs are hosted elsewhere, in a public cloud, for example, you have to have a lot of trust; a rogue fabric administrator can inspect the memory of a running VM, take an offline copy of the virtual disks, mount these and steal secrets such as passwords or perhaps mount an offline attack against an AD database.
There are a few building blocks for shielded VMs: Generation 2 VMs now come with a virtual TPM chip, which enables BitLocker for Windows VMs, and dm-crypt on Linux VMs for the virtual hard disks. Generation 2 VMs also provide Secure Boot for both Windows and Linux VMs, as they start from a virtual UEFI.
On separate physical servers that are part of an isolated administrative forest, there's a Host Guardian Service that attests to the health of Hyper-V hosts. There are two models for this: Administrator Attestation and Hardware Trusted Attestation. The first relies on trusted hosts being in a particular AD group; the second one uses new TPM version 2 chips in each host to protect the hypervisor from tampering.
In TP5, a new mode called Encryption Supported supports vTPM, disk encryption and Live Migration encryption, but it still provides less assurance than a true shielded VM. In TP5, you can also convert normal generation 2 VMs to shielded VMs, while a new recovery environment allows for troubleshooting of a shielded VM.
The end result of a shielded VM is that the fabric administrators have no access to the VM. They can turn it off, but they can't access its memory or connect to it with VM Connect; if they copy the virtual hard disks, they can't access them because they're encrypted.
Windows and Hyper-V Containers
Containers are all the rage in the IT press, and although I think it's going to take a lot longer than the pundits believe before we're all "containerized," Microsoft is now in the running with two flavors of containers (see Brien M. Posey's "A Tale of 2 Container Deployments," in Redmond March 2016). Each container can either run Nano Server or Server Core (not the GUI version); for developers, the flavors are identical. The difference comes in the deployment phase: In your own datacenter where you (probably) trust the code running in each container, you can rely on the weaker isolation of a Windows Container, but if you're deploying your code in a public cloud or at a hosting provider, the Hyper-V container gives you the same isolation the hypervisor provides.
Nano Server
The biggest change in Windows Server since NT was conceived is undoubtedly Nano Server. It's a minimal disk footprint, low resource, GUI-less, no local logon server where you add only the functionality needed. The only roles supported today are Hyper-V host server, SOFS server and as an application platform for modern applications. The benefits here are a very small attack surface, low overhead and less frequent reboots due to fewer patches.
PowerShell Direct
PowerShell Direct is a very useful feature in Windows 10 and Windows Server 2016. If you have the credentials, you can run cmdlets inside one or more VMs from the host without having to set up PowerShell remoting first.
New in TP5 is the ability to run PowerShell directly on a Nano Server, along with cmdlets for working with local users and groups.
Other Improvements
There are quite a few new features in TP5 coming to both Windows 10 and Windows Server 2016. Even with the Hyper-V role installed, you can now use Connected Standby power state.
The ability to connect a VM directly to a PCIe hardware device is interesting. It doesn't work for every device; more information is available here. If you want to try it out, read the instructions. At this stage, the main aim is connecting VMs directly to NVMe superfast storage, but GPU support is also coming.
Host resource protection is a feature that was added in response to Microsoft Azure vulnerabilities. In these cases, VMs with hostile code would try various attack methods to starve the host of resources. Host resource protection detects this and limits resources available to the VM.
Hyper-V Manager now lets you enter alternate credentials when connecting to remote Hyper-V hosts, and also save these credentials. The manager can manage both Windows 10 and Windows Server 2016, as well as Windows 8 and 8.1, and Windows Server 2012 and Windows Server 2012 R2 hosts. The console is operating using the WS-MAN protocol over port 80. WS-MAN also makes it easier to enable a host for remote management.
Hyper-V Replica now supports shielded VMs, provided the destination replica server is authorized to run the replicated VMs. To support containers, Hyper-V now supports nested virtualization, with a VM being a Hyper-V host with other VMs running inside it; several levels of this nesting is possible.
The new version of Hyper-V brings many unique features, as well as important improvements to existing ones.