In-Depth
Microsoft's New Security Approach
Microsoft is shifting to an operational focus and creating a security graph to help address the alarming new threat landscape and the rise of cloud computing.
Ever since Microsoft founder Bill Gates delivered his famous Trustworthy Computing manifesto, security has remained a focal point with every product the company released while maintaining an important role in every major public presentation ranging from technology to policy. Nearly 14 years after the Trustworthy Computing imperative -- one of Gates' most eminent decrees -- Microsoft's current CEO Satya Nadella decided it had become so deeply entrenched in Microsoft's DNA that it was time to recast Redmond's focus on security.
While Trustworthy Computing hasn't gone away, Nadella last summer moved the autonomous organization into the new Cloud and Enterprise Group. Along with a number of key acquisitions since late 2014, the moves set the stage for Microsoft's "new approach" to security, which Nadella rolled out in the keynote address at the Government Cloud Forum in Washington, D.C., in November, the week before Thanksgiving.
Noting a threat landscape that has worsened at an alarming pace year after year since Trustworthy Computing arrived in 2002, Nadella determined it was time to reset Microsoft's security strategy. In his speech he noted despite the progress Microsoft and the IT industry has made in delivering more secure solutions, the number and sophistication of attackers continue to get worse, harder to predict and often compromises lay dormant for months undetected. That's why Microsoft has to give systems and security and systems managers better resources to detect them and protect their organizations.
Escalating Threat Landscape
Nadella pointed to a staggering 160 million data records that were compromised from just the eight worst attacks last year alone. It can take on average 229 days for IT to know its systems were breached before they can respond, and often the damage already is done before a latent intrusion is detected. "The cost of all of this in terms of lost productivity and lost growth really adds up," Nadella said. "It's estimated that it's something like $3 trillion. Now, in a global economy that is challenged for growth, this is really a huge issue for all of us collectively."
The world has changed enormously, as well, since Trustworthy Computing, Nadella has concluded. Perimeters are gone and individuals, infrastructures and organizations are connected -- from sensors and mobile devices to the rise of infrastructure and platform cloud services and the delivery of applications as mobile apps and Software-as-a-Service (SaaS) solutions.
"With this changing environment it's no longer just about our code and the threat modeling and the testing, but it is in fact about the operational security posture that we have in this constantly evolving environment, this constantly under-attack environment," Nadella said. "The operational security posture to me is where it all starts. It's like going to the gym every morning. Every hour of the day you need to be prepared. And so that means you have to exercise this operational security posture in a continuous basis."
Nadella emphasized that the tools to protect, detect and respond to threats have existed for many years. The seeds for this were planted more than a year ago as Microsoft combined Intune, Azure Rights Management and Azure Active Directory Premium into its Enterprise Mobility Suite and the company doubled down on technologies such as authentication and identity management. "What is new is that posture," Nadella said.
Microsoft's new world order when it comes to security is that it must be front and center with the core systems management process and that administrators and engineers must be able to utilize the new intelligence available to them. What Microsoft is trying to build, he said, is an "intelligent security graph" that brings together virtually all of the company's security intelligence from streams throughout Microsoft, its customers, partners and security operations centers throughout the world in real time and that of select partners tied into that graph.
Microsoft Chief Information Security Officer (CISO) Bret Arsenault elaborated on Microsoft's new security approach in a post following Nadella's speech. "While security has always been a focus for Microsoft, we recognize that the digital world in which we live requires a new approach to how we Protect, Detect and Respond to security threats," Arsenault wrote. "We must better Protect all endpoints -- from sensors and datacenters to identities and SaaS applications. We must move faster to Detect threats using the scale and intelligence of the cloud, machine learning and behavioral monitoring. We must Respond more quickly and comprehensively, and empower our customers with insights that are actionable and holistic."
Building the Security Graph
Arsenault explained the concept of the security graph. "Microsoft's unique insights into the threat landscape, informed by trillions of signals from billions of sources, create an intelligent security graph that we use to inform how we protect all endpoints, better detect attacks and accelerate our response. The intelligent security graph is powered by inputs we receive across our endpoints, consumer services, commercial services and on-premises technologies -- and uniquely positions us to better protect our customers and their data."
To enable the delivery of Microsoft's new emphasis on operational security management, the company launched the Enterprise Cybersecurity Group (ECG), charged with delivering this new approach with security solutions from the company and its partners. Microsoft also launched a new Cyber Defense Operations Center, a 24x7 facility that Arsenault said has direct access to thousands of security professionals, data analysts, engineers, developers and operations specialists throughout the company, as well as with partners, customers and government experts. The center is charged with providing rapid response and resolution to all threats, he added.
In cases where the operations center needs to respond to criminal incidents, it works closely with the Microsoft Digital Crimes Unit, the company's elaborate facility that houses its own security operations center to detect global threats, along with malware and forensics labs.Azure Security Center
The key new deliverable from Microsoft's "new approach" to security is the Azure Security Center. Announced by Nadella in his speech, the company last month released a preview of the service and is expected to roll it and other new capabilities out this year. The Azure Security Center (see Figure 1) will be accessible to any of its public cloud customers via the Azure Portal.
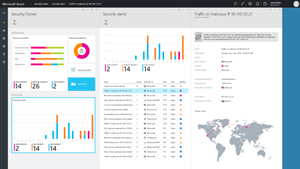 [Click on image for larger view.]
Figure 1. The Azure Security Center provides alerts and a holistic view of an organization's security picture.
[Click on image for larger view.]
Figure 1. The Azure Security Center provides alerts and a holistic view of an organization's security picture.
The Azure Security Center will provide security monitoring and policy management across all Microsoft Azure subscriptions and provide both visibility and control over security issues taking in data streams from the Cyber Crime Operations Center, Microsoft's new Advanced Threat Analytics tool released late last year, as well as letting customers tap into intelligence information from select ecosystem partners. The first such partners include Barracuda Networks Inc., Checkpoint Software Technologies Ltd., Cisco Systems Inc., CloudFlare Inc., F5 Networks Inc., Fortinet Inc., Imperva Inc. and Trend Micro Inc.
"The Azure Security Center provides a central view of your security settings across your entire Azure environment, with live monitoring of your security configuration to make sure there's ongoing good security health," explained Julia White, Microsoft's general manager for technical product management during Nadella's keynote in the first public demonstration of the new offering. "We're analyzing your security settings even as they change and bringing back policy-based recommendations, as well as guiding you through the steps to ensure your environment is secure."
 "It's no longer just about our code and the threat modeling and the testing, but it is in fact about the operational security posture that we have in this constantly evolving environment." --Microsoft CEO Satya Nadella
"It's no longer just about our code and the threat modeling and the testing, but it is in fact about the operational security posture that we have in this constantly evolving environment." --Microsoft CEO Satya Nadella
Based on an organization's application requirements and security position, an engineer may determine a Web application firewall (WAF) is necessary and is presented with choices from those partners who have offerings suited for the customer's cloud environment. In the demo, White showed how a customer can deploy a Barracuda WAF. "It significantly streamlines the process of provisioning my partner solution, as well as enables you to bring whatever your preferred security vendor is with you to the cloud in a very simple way," she said.
Automated Provisioning
Jan Poczobutt, senior director of public cloud for Barracuda, says his company's biggest hurdle now is getting its solutions running in the cloud to properly protect customers. "What Azure Security Center does for us is it helps simplify and automate that process, so the time to get an application instead of workloads up in Azure and protected is decreased significantly," Poczobutt says. "With the automation process, we're essentially taking the best practices that we have built up in the on-premises world and in the cloud and making sure they get applied on a consistent basis."
Customers can get these environments protected much quicker and with best practices already built in to the whole system, he adds. "It also offers integration of all of the information from the various security devices like ours and data feeds from Microsoft sources and putting it all together. When you talk to customers about that process, just the sheer amount of data and being able to sift through it and make sense of it can be overwhelming, so that's the great win that we see."
 "The Azure Security Center provides a central view of your security settings across your entire Azure environment, with live monitoring of your security configuration."
"The Azure Security Center provides a central view of your security settings across your entire Azure environment, with live monitoring of your security configuration."
Julia White, Microsoft's General Manager for Technical Product Management
The Azure Security Center is more than just a marketplace for third-party add-ons, several partners noted, pointing to its ability to tie together multiple solutions and make recommendations. "It takes a look at your apps and makes recommendations on what you should be adding to your application, whereas if you're going to the marketplace, it's just the marketplace, which isn't helpful if you don't know what it is you want to buy," says Alex Rublowsky, F5's VP of new business models and licensing strategy. "This uses some intelligence. That's kind of a step up for the people who own those applications that are bringing them to the cloud, not all of them are security specialists or IT departments, so this is a way of helping them protect their applications in a more effective way."
Available in the preview launched in early December are WAFs from some of the various partners, though in the future the Azure Security Center will include antimalware solutions and next-generation firewalls, as well, Microsoft said.
Trend Micro is poised to be the first antimalware provider in the Azure Security Center. "There are two really important drivers for our product -- its automation, which is how does it get installed and provisioned automatically when customers are provisioning instances of Azure -- as well as operations and management," says Partha Panda, Trend Micro's VP of global alliances. "Being able to have that single pane of window where they can look at all incidents and events and both operational and security is a big deal."
Trend Micro plans to integrate its Deep Security offering into the Azure Security Center and Panda says when security events and incidents appear on the Azure dashboard systems, network and security engineers can see both security and operational data in a common pane. "With this integration, the security context of incidents are now available alongside the operational data and that's where there is a huge value, as in they know if it's a security incident or event, they can pull in their security team and get them to work on forensics and whatever other follow-through that needs to happen," he says.
Microsoft isn't the only major IT provider recruiting third parties to deliver security as a service. IBM Corp. last month launched the IBM Security App Exchange, a new security marketplace that aims to integrate third-party tools with its QRadar security information and event management (SIEM) platform. Others, such as Intel Corp.'s Intel Security business unit had an earlier start with its Threat Intelligence Exchange (TIE) based on its McAfee Data Exchange Layer (DXL). Intel Corp. counted 16 DXL Alliance partners in October including Windows privilege management provider Avecto Ltd., Brocade Communication Systems Inc., ForeScout Technologies Inc., Mobile Iron, Titus Inc. and TrapX Security.
Assessing the New Approach
Microsoft's new approach is unique in certain ways, notes IDC Analyst Robert Westervelt. "Nadella reaffirmed the company's commitment to security and is aiming to show that Microsoft's longstanding data security and privacy principles set apart Azure and other Microsoft products and services against competitors," Westervelt says. "For example, Nadella said that Microsoft recognizes that Office 365 as a service is no longer about simply giving customers the tools, but ensuring the security of corporate data in the service itself."
Not everyone believes the new approach is an improvement. One who raised concerns is Gary McGraw, CTO of security consultancy Cigital Inc., a longtime champion of Microsoft's Trustworthy Computing initiative and its Security Development Lifecycle methodology. "It's a step backward," McGraw says. "The notion we should start with operations and go from there is absolutely wrong. It's not like what Nadella was saying anything woefully wrong or horrible, it's just in my view, the emphasis should be we should always engineer our systems to be secure and then operate them in a secure fashion."
IDC's Westervelt sees the new effort as a modernization of Microsoft's security focus. "Microsoft is attempting to showcase that its demonstrated commitment to security and privacy in Windows and Office products will also translate to its Cloud and SaaS services," he says. IDC predicts adoption of SaaS-based security will grow significantly over the next two to four years. According to the the IT market researcher, more than half of Web security market revenue will come from the cloud-based offerings over traditional on-premises gateways by 2020.
The addition of companies that Microsoft has acquired including cloud identity management provider Adollom and behavioral analysis tool Aorato, among a number of others, have helped pave the way for this transition, notes Simon Crosby, CTO of security vendor Bromium, a Microsoft partner that provides an advanced endpoint protection tool.
"Microsoft's recent security acquisitions have all been of tremendous additive value to the Microsoft cloud business," Crosby says. "Finally Microsoft is able to sell security products because it's not only protecting its own software, but customer applications in the cloud."