Active Directory How-To
Keeping an Eye on Your Network with Active Directory Auditing
Here's how to find and limit the information displayed in Auditing to just what you need.
- By Troy Thompson
- 06/11/2015
As an administrator, you have a great many tools at your fingertips. One of the tools you do not want to ignore is Active Directory Auditing. By auditing certain events, you can record which user is logging on and to which computer. You can also see who is accessing resources on your servers. Auditing uses server resources, so you should be selective with the events you audit. Depending on the nature of your company, you may want to track resources extensively. Below we will discuss the different auditing options you have at your disposal.
The list of auditing options can be seen in Figure 1.
 [Click on image for larger view.] Figure 1. Auditing options available in Active Directory.
[Click on image for larger view.] Figure 1. Auditing options available in Active Directory.
There are nine auditing settings that can be configured on a Windows computer. Each of the auditing options provides two configuration settings: Success and/or Failure. You may want to monitor all unsuccessful login attempts, but do not want to monitor the successful attempts. It really depends on what you want to track. You should ease into auditing if you are new to it. Don't audit the success and failure of every event.
Audit account logon events: Account logon events are generated whenever a computer validates the credentials of an account for which it is authoritative. In a domain environment, a user account is authenticated on a domain controller. Account logoff events are not generated. It is a good practice to have all domain controllers and servers audit these events.
Audit account management: This security setting determines whether to audit each event of account management on a computer. Some examples of account management events include:
- A user account or group is created, changed, or deleted.
- A user account is renamed, disabled, or enabled.
- A password is set or changed.
Audit directory service access: This security setting determines whether the operating system will audit user attempts to access Active Directory objects. An audit event is only generated for objects that have system access control lists (SACL) specified, and only if the type of access requested (such as Write, Read, or Modify) and the account making the request match the settings in the SACL.
- Default values on Client editions:
- Directory Service Access: No Auditing
- Directory Service Changes: No Auditing
- Directory Service Replication: No Auditing
- Detailed Directory Service Replication: No Auditing
- Default values on Server editions:
- Directory Service Access: Success
- Directory Service Changes: No Auditing Directory
- Service Replication: No Auditing
- Detailed Directory Service Replication: No Auditing
Audit logon events: This will audit each event that is related to a user logging on/off or one who makes a network connection to the computer configured to audit logon events.
- Default values on Client editions:
- Logon: Success
- Logoff: Success
- Account Lockout: Success
- IPsec Main Mode: No Auditing
- IPsec Quick Mode: No Auditing
- IPsec Extended Mode: No Auditing
- Special Logon: Success
- Other Logon/Logoff Events: No Auditing
- Network Policy Server: Success, Failure
Audit object access: This security setting determines whether the operating system audits user attempts to access non-Active Directory objects. The types of objects included in this include files, folders, printers, registry keys and Active Directory objects. Basically, if an object has an SACL, it will be included in this type of auditing.
Audit policy change: This security setting determines whether the operating system will audit each instance of attempts to change user rights assignment policy, audit policy, account policy, or trust policy. The policy areas included are:
- User Rights Assignment
- Audit Policies
- Trust relationships
Audit privilege use: This security setting determines whether to audit each instance of a user exercising a user right. There are quite a few user rights that can be audit. Figure 2 below shows a partial listing of user rights.
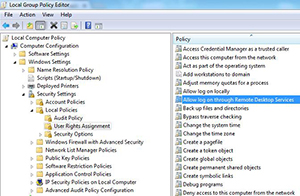 [Click on image for larger view.] Figure 2. A limited list of user rights.
[Click on image for larger view.] Figure 2. A limited list of user rights.
Audit process tracking: This security setting determines whether the operating system audits process-related events such as process creation, process exit, process termination, handle duplication, and indirect object access. Enabling this type of audit produces a large number of events and is usually enabled when troubleshooting.
Audit system events: This security setting determines whether the operating system audits any of the following events:
- Attempted system time change
- Attempted security system startup or shutdown
- Attempt to load extensible authentication components
- Loss of audited events due to auditing system failure
- Security log size exceeding a configurable warning threshold level.
Monitoring every time someone attempts to change the system time might not be too important, but auditing attempted system startup or shutdown is probably important.
Windows provides you with a lot of auditing capability. Turning auditing on for all events would provide too much information and cripple your computer's resources. Some events can and should be monitored all of the time while others should only be monitored during troubleshooting. You should be familiar with the default settings and know when to alter them. You want to stay on top of potential problems and threats in your network.
About the Author
Troy Thompson has worked in network administration for over 25 years, serving as a network engineer and Microsoft Exchange administration in Department of Defense, writing technology articles, tutorials, and white papers and technical edits. Troy is a Cisco Certified Academy Instructor (CCAI), and has numerous other certifications including CCNA, MSCE+I, Network+, A+ and Security+. Troy has also traveled the world playing music as the guitarist for the band Bride. Contact information is [email protected].