News
Microsoft Aligning Azure Active Directory for Windows 10 Mobile Device Management Scenarios
Microsoft is bringing a little more clarity to how Windows 10 will be used with traditional premises-based Active Directory, as well as with its Azure Active Directory service.
While Active Directory has been around for about 15 years, mobile device use and the bring-your-own-device phenomenon has complicated matters for organizations used to traditional controls, according to Jairo Cadena of Microsoft's Azure Active Directory team, in an Ignite session held earlier this month. End users are accessing various software-as-a-service (SaaS) apps, making management more difficult. With Azure Active Directory, identity will remain as the "foundation of control" for organizations, but Azure Active Directory will let them connect their premises-based resources with their cloud-based ones, he explained.
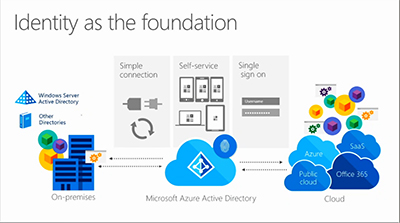
Azure Active Directory simplifies user connections to resources. It enables users to self-provision their devices. It also permits single sign-on access to an organization's resources as well as SaaS apps, according to Microsoft (see slide).
 [Click on image for larger view.]
Figure 1. Microsoft's Azure Active Directory vision as a bridge to accessing cloud resources. Source: Ignite 2015 session.
[Click on image for larger view.]
Figure 1. Microsoft's Azure Active Directory vision as a bridge to accessing cloud resources. Source: Ignite 2015 session.
Microsoft now has two models to control user identities associated with devices. There's the traditional Active Directory domain-join approach and a new Azure Active Directory "Join" feature. The Azure Active Directory Join feature lets end users set up their own devices to access organizational resources even while organizations retain management controls over those devices, Cadena explained.
Microsoft specifically improved the domain-join capability when it built Windows 10, according to Cadena. For instance, a Windows 10 domain join automatically registers with Azure Active Directory, Cadena said, adding that it's "great for organizations that already have processes in place for domain-joined devices." Organizations can continue to use their existing management solutions with Azure Active Directory, he said.
Azure Active Directory Scenarios
Microsoft conceives of the Azure Active Directory Join feature as primarily for organizations with users who access Office 365 and SaaS apps. It facilitates enterprise mobile device management capabilities, too, Cadena said.
In a blog post this week, Microsoft outlined three basic scenarios for using Azure Active Directory Join:
- Organizations have end users that mostly access SaaS apps
- Organizations have a mix of long-term and temporary users (such as school faculty users and student users)
- Organizations have end users that bring their own devices to work
The blog post also noted that "Azure AD Join is also great if you want to manage devices from the cloud with a MDM [mobile device management solution] instead of with Group Policy and SCCM [System Center Configuration Manager]."
Cadena offered an explanation along those lines:
"For admins, we have the ability to have that same concept of Group Policy, but now we're moving into this concept of mobile device management," he said. "The admin can set up Azure AD Join in such a way that every device that registers with Azure AD gets enrolled into the MDM -- by Intune or some third-party MDM."
He explained that Microsoft has built a layer in Windows 10 that will translate management settings into the device. That layer also was present in Windows 8.1, but the management experience "was a little bit limited and it was not consistent across devices," Cadena explained.
"Now in Windows 10 … we have extended that range of settings, which is not a full GPO [Group Policy Object] set of settings, because the world is different, but it's good enough for you to manage and control these devices."
He added that management controls will be consistent across multiple form factors, such as phones, tablets and PCs. It will enable IT pros to create rules for devices that are compliant with organizational policies and those that are not compliant. "This is kind of like the replacement for Network Access Protection (NAP)," he explained.
Cadena demonstrated the self-provisioning experience that end users undergo when they join their Windows 10 devices using the Azure Active Directory service. Microsoft calls that the "first-run experience." It's a Web-based enrollment experience and Windows 10 has APIs that make this first-run experience possible, he explained. It's somewhat dependent on the different Windows 10 editions -- Home, Professional and Enterprise -- as the Home SKU assumes that device is a home device, he explained.
How Authentication Works
Cadena also explained a bit about how the authentication process works after setup by the end user. On an Azure Active Directory domain-joined device located on premises, the user enters a password that is sent to Azure Active Directory, which returns a token to Windows. This is a special token called a "primary refresh token" (PRT) that has access to multiple resources.
"At the same time, in that Azure AD-joined device that works on premises and has line-of-sight to a domain controller, we send those credentials to the KDC. And then the KDC will authenticate that user and provide a very similar token ticket," Cadena said.
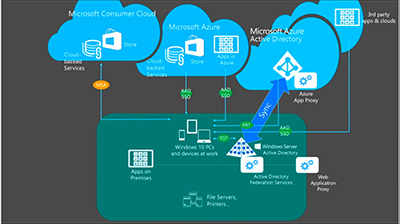
The gist of this process is that with the PRT generated, a device "can go to any AAD [Azure AD] resource and then it will have automatic true SSO [single sign-on]," he explained. That access includes single sign-on with various Azure services as well as with the services of third-party cloud providers (see chart).
 [Click on image for larger view.]
Figure 2. Azure Active Directory (AAD) enables single sign-on (SSO) access across cloud services via a primary refresh token (PRT), with consumer cloud access enabled by a Microsoft account (MSA). Source: Ignite 2015 session.
[Click on image for larger view.]
Figure 2. Azure Active Directory (AAD) enables single sign-on (SSO) access across cloud services via a primary refresh token (PRT), with consumer cloud access enabled by a Microsoft account (MSA). Source: Ignite 2015 session.
Consumer applications can be accessed from Microsoft's "consumer cloud" via a Microsoft account (MSA), he added.
Users that have Azure Active Directory domain-joined devices located outside the on-premises network also get the single-sign-on experience when accessing SaaS apps, Cadena explained.
"If you are outside the network, with that primary refresh token, you can have true SSO to those applications in the cloud. Of course, you won't have access to your on-premises applications because you don't have line-of-sight to those resources, unless you have been published through the Web access proxy or the Azure AD application process."
Availability in Windows 10
Microsoft is planning to release Windows 10 this summer, followed by another release in the fall of this year. Some of these Azure Active Directory features won't be available until the fall Windows 10 release, a Microsoft blog post explained earlier this month. However, the following Azure Active Directory features are planned at some point with future Windows 10 releases, according to that post:
- User self-provisioning of devices
- Ability to use existing Azure Active Directory accounts to log into Windows (such as an Office 365 account)
- Single sign-on to business apps in the cloud
- Single sign-on to on-premises resources via the Azure Active Directory Application Proxy service
- Windows Store access to enterprise apps
- Roaming of settings and desktops, as well as synchronized Wi-Fi passwords
- Use of the Azure Active Directory Join feature for devices that aren't using a traditional domain join
Cadena noted that a lot of organizations already may be using Azure Active Directory, especially if they are using Office 365 services. "By the fact that you have Office 365, you already have Azure AD," he said.
About the Author
Kurt Mackie is senior news producer for 1105 Media's Converge360 group.