In-Depth
Manage Mobile Devices and Policies in Active Directory
Introduced in Windows Server 2012 R2, Workplace Join lets otherwise incapable mobile devices participate in an Active Directory domain, but doesn't provide comprehensive security.
One of the major challenges facing organizations today is the proliferation of mobile devices. Mobile device use raises a number of concerns around issues such as security and privacy. Although there are a number of different solutions available from Microsoft and from third-party vendors for mobile device management, IT shops are increasingly finding that achieving the desired level of security requires them to adopt multiple solutions.
In order to understand the advantages and disadvantages of the available solutions, it's important to understand why mobile devices pose such a challenge in the first place. Mobile devices are different from desktop PCs in that they typically cannot be joined to an Active Directory domain. When a PC is joined to the Active Directory domain, a computer account is created as a means of authenticating and positively identifying that computer as it participates on the network. Furthermore, applying Group Policy settings can secure the computer's OS, and access control lists provide a mechanism for controlling access to network resources at the computer level.
Mobile devices are the complete opposite. They can't be joined to the Active Directory domain (at least not in the traditional sense) and, therefore, you can't apply Group Policy settings to a mobile device.
Previously, one of the best options for securing mobile devices that participate on a corporate network was the use of ActiveSync policies. For those who might not be familiar with ActiveSync policies, they were first introduced in Exchange Server as a mechanism for pushing mail to mobile devices. Eventually, Microsoft extended the ActiveSync protocol in an effort to allow security settings to be applied to mobile devices.
The Trouble with ActiveSync
ActiveSync has become an industry standard for providing synchronization between Exchange and mobile devices. Every major device manufacturer supports the use of ActiveSync policies as a way of locking down their devices. However, there are a couple of issues that limit ActiveSync as a comprehensive mobile device security solution.
The first issue is that mobile devices support ActiveSync in varying degrees. ActiveSync policies are made up of a collection of individual policy settings. Most of the mobile devices available today do not support every available policy setting. As such, administrators aren't assured that a policy setting will apply to every device that's in use on their network unless they restrict access to devices that do not fully support all policy settings (which includes most device types). The various ActiveSync policy settings and the devices that support them are published in a Wikipedia post.
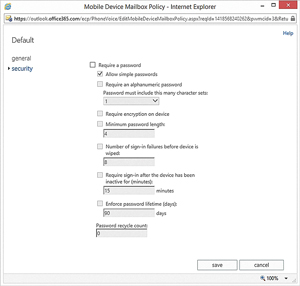
Another issue with using ActiveSync for mobile device security is that it has become increasingly difficult to fully implement. Exchange Server 2013 and Microsoft Office 365 expose ActiveSync policy settings through mobile device mailbox policies. Microsoft makes it relatively easy to create mobile device mailbox policies, but the Exchange Server 2013 Administrative Center and the Office 365 Exchange Admin Center only expose the most basic policy settings (see Figure 1). These are the policy settings that are used to require a password and to set password-related attributes, such as the minimum password length. There are dozens of other ActiveSync settings available, but using them means delving into Windows PowerShell (or reverting to Exchange Server 2010).
 [Click on image for larger view.]
Figure 1. Office 365 exposes only the most basic ActiveSync policy settings.
[Click on image for larger view.]
Figure 1. Office 365 exposes only the most basic ActiveSync policy settings.
Organizations that create comprehensive mobile device mailboxes usually find that those policies work really well for securing mobile devices. Even so, ActiveSync has its limits. For instance, ActiveSync doesn't allow for device-level access control for resources that exist outside of Exchange Server.
Pluses and Minuses for Workplace Join
One of the new features in Windows Server 2012 R2, called Workplace Join, is a way for allowing otherwise incapable mobile devices to participate in the Active Directory domain. Even though a device such as an iPad or a Windows RT tablet can't join to an Active Directory domain in the same way a Windows desktop PC can, the Workplace Join feature lets these types of devices participate in Active Directory in other ways.
The Workplace Join feature accomplishes three main things. First, it allows a device to be positively identified on the network. When a user enrolls a mobile device, a certificate is assigned to that device. This certificate is used as an identification mechanism. The device is also added to Active Directory and is listed in the Enrolled Devices container.
Second, the Workplace Join feature enables device-level access control. It's possible to base access to Web applications on whether the device has been enrolled in Active Directory. This isn't done through standard access control lists, but rather as a function of Active Directory Federation Services and a relaying-party trust. Third, Workplace Join provides single sign-on capabilities for certain network resources.
Unfortunately, Workplace Join is inadequate by itself. Although it does provide some interesting capabilities, it also lacks some key features that are required for organizations to effectively manage mobile devices. Keep in mind Workplace Join is designed to simplify resource access. As such, it's not a true mobile device security feature. For instance, Workplace Join doesn't provide a collection of Group Policy settings that can be applied to mobile devices. Similarly, it doesn't provide the types of device security controls that are available through ActiveSync policies.
Workplace Join is also inadequate as an access control mechanism. While it's true Workplace Join can be used to grant or deny access to network resources based on device enrollment, there are significant limitations. You cannot, for instance, use an access control list to block devices that aren't enrolled. Most often Workplace Join is used to control access to browser-based apps.
Moving to a Primary Solution
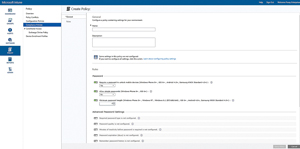
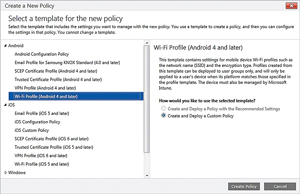
Workplace Join and ActiveSync policies both have their place, but the primary Microsoft solution for securing and managing mobile devices is Microsoft Intune (formerly known as Windows Intune). Microsoft Intune is a cloud-based service that can apply security controls to user devices. These controls are very similar to those that are available through ActiveSync (see Figure 2). Unlike raw ActiveSync, however, Intune is also able to create template-based policies that can be applied to various types of mobile devices (see Figure 3).
 [Click on image for larger view.]
Figure 2. Microsoft Intune policies are similar to ActiveSync policies.
[Click on image for larger view.]
Figure 2. Microsoft Intune policies are similar to ActiveSync policies.
 [Click on image for larger view.]
Figure 3. Microsoft Intune can create template-based policies for mobile devices.
[Click on image for larger view.]
Figure 3. Microsoft Intune can create template-based policies for mobile devices.
Microsoft Intune is also able to manage applications on mobile devices. For example, the organization's approved applications can be made available to mobile devices. Administrators also have the ability to blacklist undesirable applications.
So what should you be using to manage your network -- Microsoft Intune, Exchange Server, Workplace Join or perhaps something else? For the best overall management experience, you might want to use a combination of all three. All three technologies have both abilities and limitations. However, the three technologies complement one another rather nicely.
On the surface, there seems to be a high degree of overlap between the three solutions. Microsoft Intune, for example, provides the ability to enforce password policy settings on mobile devices, but so does ActiveSync. Similarly, the Workplace Join feature provides access control to Web-based applications, but Microsoft Intune also provides application access control capabilities.
Although there are some similar capabilities exposed through the various management platforms, the overlap helps to provide good, comprehensive security for mobile devices. The reason why overlapping features may be necessary is because mobile devices can exist in different states.
Imagine for a moment that a user wants to access e-mail and the calendar running on a mobile device. Because ActiveSync is an Exchange Server feature, a user could easily synchronize the device to Exchange Server without ever enrolling the device in Active Directory. Doing so would provide the user with access to his mail, calendar, contacts and even his task list.
In this type of situation, the ActiveSync policy settings are the only security mechanisms readily available to prevent sensitive information from the user's mailbox from being exposed should the user's device be lost or stolen. Remember, the user is able to access the full contents of his mailbox without ever performing a Workplace Join.
Although the user can access quite a bit of data without ever performing a Workplace Join, the user's abilities are also somewhat limited. Sure, the user can access the contents of his mailbox (including the calendar, contacts and task lists), but can't access any other network resources. This is where the Workplace Join feature comes into play.
Oftentimes administrators use the Workplace Join feature as an access control mechanism for users who are accessing Web applications from outside the organization. Organizations with large SharePoint deployments in place are probably the best example of this. If a user attempts to log into SharePoint from a desktop computer that exists inside the organization's firewall, the user's Active Directory credentials are normally used to authenticate the user directly into SharePoint.
In the past, connectivity to SharePoint Sites has worked similarly for a user connecting from outside the organization. The user would enter a URL for the SharePoint Site, and then be asked to enter her Active Directory credentials to gain access to the site.
The Workplace Join feature provides an extra layer of security. The network can be configured to deny access to SharePoint content for devices that aren't enrolled in Active Directory. This is a great way of preventing users who are working on unauthorized devices from accessing SharePoint resources or other Web-based resources.
So what about Microsoft Intune? Microsoft Intune is a management tool that provides a single pane of glass for managing a variety of mobile devices. Microsoft Intune offers a self-service portal where a user can access applications or perform functions such as a device wipe or the deployment of an application to his mobile device.
Redmond's recommendations for Microsoft Intune have changed considerably over the years. The company's current recommendation is that you use ActiveSync to secure any device that isn't enrolled in Active Directory via Workplace Join. Microsoft Intune is primarily designed to manage devices that have been enrolled in the Active Directory.
Remember, though, Microsoft Intune is designed to act as an organization-level management solution for mobile devices, and it would be counterproductive to use two separate solutions for mobile device management (ActiveSync for devices not enrolled and Microsoft Intune for devices that have been enrolled).
Fortunately, it's possible to manage non-enrolled devices using Microsoft Intune. The trick to doing so is to use the Microsoft Exchange Connector. This connector ties Microsoft Intune to Exchange Server so that Intune can be made aware of devices that are being used to access Exchange Server resources, but aren't enrolled in Active Directory. That way, non-enrolled devices can be managed alongside devices that have been enrolled. In case you're wondering, it is possible to block e-mail apps on non-compliant devices from accessing Exchange.
Benefits and Limitations
The fact that mobile devices aren't domain-joined in the traditional sense makes mobile device management tricky. The tools and techniques used for mobile device management will likely change as time goes on, but for the time being, Microsoft has given us several good tools for managing device security and access control to network resources.