In-Depth
How To Sync Azure Active Directory with SaaS
The new Microsoft Azure Active Directory puts more on-premises features into the cloud version and links to more than 1,200 Software as a Service (SaaS) apps.
Last year's release of Microsoft Azure Active Directory introduced a new way of providing its identity and access management controls in the cloud. Azure Active Directory was designed to be a cloud-based directory service that could integrate with your on-premises Active Directory in order to help bridge the gap between local and cloud resources.
Even though Azure Active Directory introduced a number of very welcome capabilities (such as cloud single sign-on), there were those who were disappointed by it, citing that Azure Active Directory did not live up to its full potential.
Microsoft has decided to augment the capabilities of Azure Active Directory by offering a premium version of Azure Active Directory Services called Azure Active Directory Premium. The premium version has all of the same features and capabilities as the previous version (which is now being referred to on some Microsoft Web pages as Azure Active Directory Free), as well as a number of new features and capabilities Microsoft has introduced. In addition, Azure Active Directory Premium comes with an enterprise SLA that guarantees 99.9 percent availability.
Premium Features
The new feature that has probably received the most attention is support for Forefront Identity Manager, the Microsoft solution designed to establish user identities across multiple, heterogeneous platforms. Azure Active Directory Premium includes the ability to work with a Forefront Identity Manager Server in your on-premises network. This capability will be the most useful for organizations that have multiple on-premises directories (such as directories on multiple platforms) they want to synchronize with Microsoft Azure.
Given the increased number of high-profile breaches, many organizations are looking more closely at multifactor authentication. While multifactor authentication with Microsoft Azure would be nice, there's a lot more to it than that. Microsoft has designed Azure Active Directory Premium to support multifactor authentication for a variety of services and applications -- both Microsoft and third-party. Furthermore, organizations can use multifactor authentication to secure resources regardless of whether they exist on-premises or in the cloud.
The list of applications and services that can be secured through multifactor authentication is impressive. Obviously, multifactor authentication can be used with Azure, and it shouldn't come as any surprise that Microsoft also provides multifactor authentication support for Office 365 and Dynamics CRM Online. In addition, Microsoft has provided pre-integration with more than 1,200 non-Microsoft cloud services.
Another welcome capability found in Azure Active Directory Premium is the ability to compile various access and usage reports. Microsoft provides a variety of reports that allow you to see how your Azure resources are used. You can also use these reports to detect and mitigate potential security risks.
There are four main categories of reports used by Azure Active Directory Premium:
- User-Specific Reports: Display information about who logged in and when, and from what device.
- Error Reports: As you would expect, these reports are primarily focused on provisioning errors.
- Anomaly Reports: Similar to user-specific reports, except they only contain login events that are deemed to be somewhat suspicious.
- Integrated Application Reports: These cover the 1,200 third-party SaaS offerings Microsoft supports and provide details about the way various cloud applications are interacting with Azure.
Keep in mind these reports are not multifactor authentication-specific. Rather, they're more generalized reports covering integration of Azure Active Directory to the third-party SaaS apps.
Create and Manage Groups
Azure Active Directory Premium lets you create groups to control access to external SaaS applications. As of right now, there are approximately 1,800 different applications that can be accessed and managed through groups.
Azure Active Directory Premium also introduces some new self-service capabilities. Some revolve around group management. Authorized users are able to create groups themselves, rather than having to request an administrator to create the necessary group. When a user does create a group, he can not only manage the group's membership, he can also delegate group ownership so that other authorized users can help out with membership requests. Incidentally, membership requests are another new capability: Users have the ability to request access to groups.
Another self-service capability in Azure Active Directory Premium is self-service password resets: End users can reset their own passwords. Microsoft has a few other features in the works that haven't been released for production use yet. These features include password reset with write back to on-premises directories, Azure Active Directory Sync bi-directional synchronization, and Azure Active Directory application proxy.
Licensing Requirements
Because Azure Active Directory Premium offers added features, it's licensed separately from your Azure subscription. Microsoft offers a 90-day free trial of Azure Active Directory Premium, but if you want to use the premium directory on an ongoing basis you'll need to purchase the necessary licenses. The licenses are available through the Microsoft Volume Licensing Web site.
When you purchase licenses for Azure Active Directory Premium, you'll need to activate those licenses before you can use them. The activation process is beyond the scope of this article, but you can find instructions for the activation process here.
Set Up
You probably don't want to convert your production Azure Active Directory to the premium version until you've had a chance to at least try Azure Active Directory. That being the case, you should build a brand new directory used just for testing purposes. This new directory will initially exist as a standard Azure Active Directory, but once it's up and running you can convert it into a premium directory.
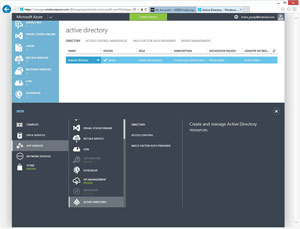
To get started, log into Azure and select the Active Directory tab. Now, click New to create a new directory (see Figure 1). Now, click on App Services | Active Directory | Directory.
 [Click on image for larger view.]
Figure 1. Creating an Azure Active Directory Premium is initially similar to that of creating a free directory.
[Click on image for larger view.]
Figure 1. Creating an Azure Active Directory Premium is initially similar to that of creating a free directory.
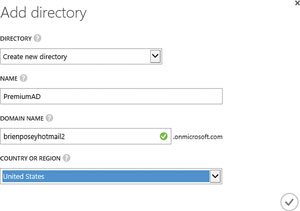
Click Custom Create and you will be taken to the Add Directory dialog box. This dialog box requires you to select the Create New Directory option and then enter a name for the directory you're creating, followed by a domain name and your country or region (see Figure 2). Click the checkmark icon to create the directory.
 [Click on image for larger view.]
Figure 2. You must populate the Add directory dialog box.
[Click on image for larger view.]
Figure 2. You must populate the Add directory dialog box.
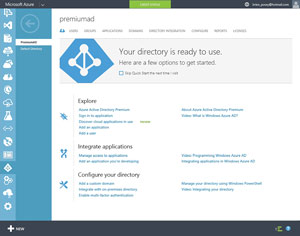
Next, go back to the main Azure screen and click on the Active Directory tab, followed by the directory you just created. When you do, you should see a screen indicating your directory is ready to use. You'll notice the Explore section contains an Azure Active Directory Premium link (see Figure 3,). Go ahead and click on this link, followed by the Try Azure Active Directory Premium link.
 [Click on image for larger view.]
Figure 3. Click on the Azure Active Directory Premium link.
[Click on image for larger view.]
Figure 3. Click on the Azure Active Directory Premium link.
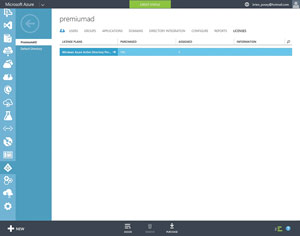
You should now see a message telling you that you're about to start a 90-day trial of Azure Active Directory Premium, and that it's licensed separately from the other Azure services. Click on the checkmark icon to acknowledge the message. You should briefly see a message indicating you successfully created the new directory. When I set up Azure Active Directory Premium, my screen got stuck and I had to refresh it to be able to access my premium Active Directory. You can confirm the conversion from a standard (free) directory into Azure Active Directory Premium was successful by looking at the License Plans field. It should indicate a Microsoft Azure Active Directory Premium license is in use (see Figure 4). You'll also notice in the figure that the trial version includes a hundred directory licenses.
 [Click on image for larger view.]
Figure 4. Azure Active Directory Premium has been created.
[Click on image for larger view.]
Figure 4. Azure Active Directory Premium has been created.
Because Azure Active Directory Premium is licensed separately from the other Azure services, you'll need to assign licenses to your users before they'll be able to use the premium features.
To assign licenses to users, click on the license plan (shown in the License Plan column in Figure 3). Click on the Assign icon, found at the bottom of the screen. You should see a list of the users to whom you can assign premium Active Directory licenses. As you select each user, the user's name should be added to the Assign column (see Figure 5). Now, just click the checkmark icon to assign a license to the user. When the process completes, you'll be returned to the Licenses screen. The Assigned column should indicate the number of licenses you've assigned.
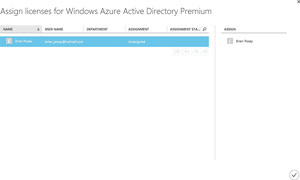 [Click on image for larger view.]
Figure 5. You'll need to assign a license to individual users.
[Click on image for larger view.]
Figure 5. You'll need to assign a license to individual users.
If you have trouble licensing a user, I recommend checking to see in which region the user is located. When you created the new directory you had to specify a region. If the user's region doesn't match the directory's region, there's a chance you might not be able to license the user. Certain Azure features and services are restricted by region for legal reasons. For example, currently Azure Active Directory Premium isn't supported in China.
Indeed, Azure Active Directory Premium introduces some exciting new features and capabilities. Of course, these capabilities are targeted toward large enterprise class organizations. Smaller organizations can still achieve basic functionality by using the free version of Azure Active Directory.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.