In-Depth
Hands-On with Microsoft's Advanced Threat Analytics 1.8
Microsoft's new Advanced Threat Analytics 1.8 applies the company's latest advances in AI and machine learning to protect against ransomware and other malicious activity.
In recent years, Microsoft has stepped up its security offerings. While security has remained a key focus in the design of everything Microsoft offers over the past 15 years -- from Windows to its datacenter offerings -- more recently the company has upped the ante. Microsoft stepped up its security focus a few years ago with the introduction of Windows Defender, an endpoint anti-malware engine included with the Windows OS.
Microsoft stepped that effort up considerably with additional products and services, most notably Enterprise Mobility + Security (EMS). Given the need for threat detection in advance of looming intrusions, the continuous onslaught of ransomware infections, recent high-profile security breaches, and of course the significant investments Microsoft has made in security in Windows Server 2016 and other products, it's not surprising Microsoft is expanding its security products portfolio. Microsoft also has among the most sophisticated cybercrime detection capabilities through its Digital Crimes Unit, meaning it has considerable intellectual property along the lines of threat intelligence.
While the various security-related sessions at Microsoft's recent Ignite conference quite naturally covered a variety of topics, there was a disproportionate amount of emphasis on Microsoft's latest Advanced Threat Analytics (ATA) release.
Predicting Threats Using Machine Learning
ATA is a tool designed to detect threats to your network's security. It does all the usual things you'd expect from a threat-intelligence tool, such as looking for insecure configuration settings and spotting common attack techniques, in real time.
The thing that separates Microsoft's ATA from similar security tools is the way it uses artificial intelligence (AI). Consider someone stealing the password for a privileged account, who begins using it for nefarious purposes. Assuming the attacker takes their time, making very small incremental changes, the attack is likely to go unnoticed for quite some time. Average attacks go undetected for 200 days, according to various reports. The reason for this is simple. An attacker using a trusted account may be able to accomplish his objectives without relying on "hacking techniques." The problem for security administrators is it's very difficult for an automated tool to tell the difference between legitimate administrative activity and illegitimate activity performed using a legitimate and trusted account.
Another problem is many conventional security event detection tools are signature-based. In other words, a detection system might have a signature that tells it what a distributed denial-of-service (DDoS) attack looks like, or it might have a signature that allows the tool to identify a particular ransomware attack.
Signature-based detection has been around in one form or another since at least the 1980s. The problem with signature-based detection is that new threats emerge daily, and there will always be threats for which no signature exists.
This is where AI comes into play. Although ATA does use some conventional threat-detection methods, Microsoft is well aware of the shortcomings. As such, ATA uses machine learning to analyze the traffic patterns on your network. By doing so, ATA is able to get a sense of what a normal day looks like for your organization. For example, ATA learns which computers individual users commonly log onto, and what those users do on a daily basis.
The idea behind using machine learning is the possibility to create a normalcy baseline. Any attack, whether it's based on malware, a malicious script or even a trusted account, will inevitably have characteristics that fall well outside the scope of what's considered to be normal operations. By looking for these types of outliers, ATA can spot attacks that signature-based systems might miss.
Deploying ATA
Microsoft's ATA Center version 1.8 is designed to run on-premises, but you'll have to do a bit of planning ahead of time in order to determine how it should be deployed. The ATA software is based on the use of an ATA gateway. There are two main gateway deployment models -- ATA Gateway and ATA Lightweight Gateway.
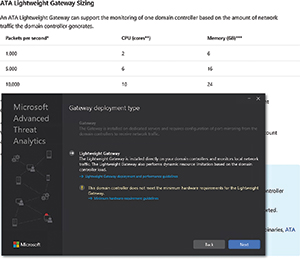
The ATA Lightweight Gateway option can be installed directly onto a domain controller (DC), and doesn't require a dedicated server, nor do you have to configure port mirroring. The disadvantage to using this deployment method is it's designed for lightweight operations such as lab deployments, branch offices or deployments for small businesses. The ATA Lightweight Gateway deployment can handle up to 10,000 Active Directory packets per second (assuming your hardware can keep pace).
Not surprisingly, the ATA Gateway option is the preferred deployment type. This option requires a dedicated gateway server, and you will have to set up port mirroring on your DCs, so DC traffic can be analyzed by the ATA Gateway. An ATA Gateway can handle up to 50,000 packets per second. It is possible to deploy multiple ATA Gateways if you need to deal with a greater volume of traffic, but the aggregate maximum load that ATA can handle is a million packets per second, although the list of new features suggests this limit no longer exists (see here). Microsoft posted its capacity planning guidelines here.
The actual ATA deployment process is relatively straightforward, especially if you're performing a Lightweight Gateway deployment. The installation is wizard-based, and the wizard's prompts are very simple and straightforward. For example, the wizard asks you questions about your preferred installation path, and whether you want to use Windows Update.
The one prompt that does warrant mentioning is the Setup wizard, which asks if you want to use a self-signed certificate. Self-signed certificates are fine for testing purposes, but I would strongly recommend using a certificate from a well-known commercial certificate authority if you're performing a production deployment, because self-signed certificates by their very nature are untrusted.
When Setup completes, you'll be able to access ATA through a Web-based console. At this point, there's still a bit of configuration work that needs to be done before you can use ATA (see Figure 1). Specifically, you're going to need to provide a set of authentication credentials, install a Gateway and connect it to your AD forest.
 [Click on image for larger view.]
Figure 1. You'll need to install the gateway and attach it to Active Directory.
[Click on image for larger view.]
Figure 1. You'll need to install the gateway and attach it to Active Directory.
I deployed a Lightweight Gateway and found the process intuitive and painless. I like the way Microsoft provides help within the wizard. The virtual machine (VM) I used didn't initially have enough memory to run the Gateway software (see Figure 2). Rather than simply generating an error message, the installer provided me with a link to the minimum hardware requirements. Clicking on the link didn't just take me to a Web page listing the various requirements, but directed me to the exact area of the page I needed. I didn't have to hunt around for the information that I required.
 [Click on image for larger view.]
Figure 2. The Gateway Deployment Wizard does a good job of giving you help when you need it.
[Click on image for larger view.]
Figure 2. The Gateway Deployment Wizard does a good job of giving you help when you need it.
Figure 3 shows the timeline view within the ATA Web interface. Although it had detected no threats, from the time it was created, you can see that threats are classified as Open, Closed or Suppressed. Open threats are further categorized as High, Medium or Low.
 [Click on image for larger view.]
Figure 3. This is the Microsoft Advanced Threat Analytics Web console.
[Click on image for larger view.]
Figure 3. This is the Microsoft Advanced Threat Analytics Web console.
New ATA Features
The latest version includes vastly improved detection capabilities. Microsoft has improved the unusual protocol detection capabilities in order to allow the software to detect WannaCry, one of the worst ransomware attacks that targeted Windows-based systems this year.
ATA 1.8 will also detect abnormal modifications to AD groups that have elevated privileges. ATA will also spot authentication failures related to brute-force attacks, and it will detect Windows Management Instrumentation-based remote code execution attempts from DCs. Microsoft has also done some work concerning detecting reconnaissance-related AD queries, and Kerberos Golden Ticket activity.
While it's always interesting to hear about new features and capabilities, Microsoft has also fixed a major shortcoming. ATA 1.8 has an improved detection engine that finally corrects what was perhaps the biggest problem plaguing previous versions: the false positive. Specifically, Microsoft has fixed the detection of false positives as they relate to privilege escalation detection (forged PAC), encryption downgrade activity (the so-called skeleton-key method), unusual protocol implementations and broken trusts.
ATA 1.8 also makes it easy to triage suspicious activity by excluding legitimate administrator activities, suppressing alerts for recurring activities, and you can even delete individual activities from the attack timeline. Microsoft has also provided some new reports in the latest ATA version. There's a summary report and a sensitive group report.
There were also two features Microsoft removed from ATA in version 1.8. These features are the option to add notes to suspicious activities, and the recommendations for mitigating suspicious activities that previously appeared on the Suspicious Activities Timeline. Microsoft published a list of changes made to version 1.8 here.
Going Beyond Active Directory
Although Microsoft ATA has traditionally been known as an AD monitoring tool used to detect security breaches, similar threat detection and prevention technology is slowly making its way into a variety of other Microsoft products through something Microsoft calls Advanced Threat Protection (ATP).
In the case of Microsoft Office 365, for example, Advanced Threat Protection exists as a tool for detecting e-mail threats. Like ATA, Office 365 ATP uses machine learning techniques to determine whether message attachments are malicious. A feature Microsoft calls Safe Attachments performs behavioral analysis on attachments within a sandboxed environment, in order to determine whether the attachment exhibits malware-like behavioral characteristics. By using machine learning in this way, the Safe Attachments feature can detect threats even if no signature exists.
Another Office 365 ATP feature is Safe Links. The Safe Links feature is essentially a proxy for links within e-mail attachments. When a user clicks on a link, the URL is passed to Office 365 for behavioral analysis. If the link is determined to be malicious, then Office 365 blocks it. A report can even be generated to inform the administrator of the user's risky behavior.
Unfortunately, Office 365 ATP is only included with Office 365 E5 subscriptions. Microsoft does, however, allow ATP to be added to most other Office 365 subscriptions at an extra cost.
Traditional Detection Is Insufficient
The proliferation of ransomware and all the recent high-profile security breaches point to the need for a more effective approach to security. Traditional threat-detection methods are completely inadequate by today's standards, so it's nice to see Microsoft using advanced machine learning as a tool for detecting and mitigating various threats.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.