Posey's Tips & Tricks
How To Disable SMB 1.0
Despite Microsoft patching many of the security vulnerabilities, including the one that led to the WannaCry attack, it's a smart move to disable the protocol to avoid future security headaches.
As early as 2016, Microsoft was cautioning customers to stop using the SMB 1.0 protocol because of its inherent security flaws. Unfortunately, this warning was largely ignored until some of the more recent ransomware attacks, including the infamous WannaCry attack, have begun exploiting the SMB protocol.
It is worth noting that Microsoft Security Bulletin MS17-010 has addressed SMB 1.0 vulnerabilities that allow remote code execution. Even so, it is best to disable SMB 1.0 unless you have a compelling reason to keep using it.
There are several different methods that you can use to disable the SMB 1.0 protocol. Any of these methods will work, but some are better suited to larger environments, while others are more appropriate for one off situations.
Disabling SMB 1.0 on an Individual PC
If you only need to disable SMB 1.0 on one (or perhaps a few) PCs, then you can easily do so manually. The exact steps that you will need to follow will vary depending on the version of Windows that you are using.
In Windows 10, you can disable SMB 1.0 by right clicking on the Start button, and choosing the Run command from the shortcut menu. Now, type Control at the Run prompt to open the Control Panel. When the Control Panel opens, click on the Programs link, and then click on the option to Turn Windows Features On or Off. This will cause Windows to display the Windows Features dialog box. Now deselect the SMB 1.0 / CIFS File Sharing Support checkbox, as shown in Figure 1, and click OK.
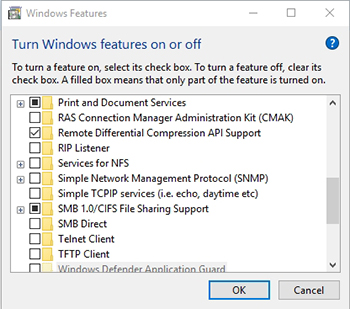 [Click on image for larger view.] Figure 1. Deselect the SMB 1.0 / CIFS File Sharing Support check box, and click OK.
[Click on image for larger view.] Figure 1. Deselect the SMB 1.0 / CIFS File Sharing Support check box, and click OK.
Using PowerShell
You can also use PowerShell to remove SMB 1.0. There is quite a bit of misinformation going around about this particular technique. Many Web sites indicate that you can check for the presence of the SMB 1.0 protocol by using theGet-WindowsFeature cmdlet. While there is an element of truth in this statement, it isn't quite right for all situations.
The Get-WindowsFeature cmdlet is designed to be used on Windows Server, not Windows 10. You can use the Get-WindowsFeature cmdlet on a Windows 10 machine by downloading and installing the Remote Server Administration Tools (RSAT). You can download these tools from here.
But here is the catch. If you want to use the Get-WindowsFeature cmdlet, you will have to import the Server Manager module, and even then you will only be able to use the Get-WindowsFeature cmdlet against a machine that is running a Windows Server operating system. You can't use the Get-WindowsFeature cmdlet to see which features are installed on a Windows 10 machine. For that you will have to use the Get-WindowsOptionalFeature cmdlet. Don't ask me why Microsoft decided to do things in this way. At any rate, you can check for the presence of the SMB 1.0 protocol on a Windows 10 machine by using this command:
Get-WindowsOptionalFeature -Online -Featurename SMB1Protocol
If the protocol is online, then you can disable it by using this command:
Disable-WindowsOptionalFeature -Online -Featurename SMB1Protocol
Upon disabling this feature, you will need to reboot the computer. You can see what the entire process looks like in Figure 2.
 [Click on image for larger view.] Figure 2. You can use PowerShell to disable the SMB 1.0 protocol.
[Click on image for larger view.] Figure 2. You can use PowerShell to disable the SMB 1.0 protocol.
Using Group Policy
When I set out to write this post, my initial goal was to talk about disabling the SMB 1.0 protocol through the use of group policy settings. That actually ended up being more difficult to do than I had anticipated. While SMB 1.0 can be disabled through group policy settings (or through the registry editor), the process is significantly different from what you might expect, and is not necessarily encouraged by Microsoft. If you are curious as to how this works, then check out this blog post.
There is actually something of a debate surrounding the disabling of the SMB 1.0 protocol. On one side, there are those who subscribe to the belief that this protocol is dangerous and outdated, and should therefore be deleted. On the other side are people who say that Microsoft has patched the security vulnerabilities associated with the protocol, so there is no reason to disable it. In my opinion, both arguments have merit. Personally, I tend to think that disabling the protocol is a good thing, because even though the protocol has been patched, disabling it reduces a machine's potential attack surface.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.