In-Depth
Can AI Protect IT?
Microsoft has touted how artificial intelligence (AI) and machine learning are solving many problems. Now Redmond and IT security providers are applying AI in cyberthreat detection.
Artificial intelligence (AI) and machine learning have existed in computer science for decades, but in 2017 they were the hottest things in IT. Touted to address everything from helping diagnose and cure major diseases to translating live Skype sessions on the fly and enabling smart chatbots, applying AI and machine learning's highest calling may come in the effort to protect PCs, devices and critical infrastructure. Adding deep learning, automation and predictive analytics has become a key imperative by virtually every provider of software this year amid an exponential rise in cyberattacks.
If there's one place AI and the use of predictive analytics need to have a profound impact quickly, it's thwarting the massive wave of data breaches that increase exponentially each year, where 2017 was off the charts. Many leading threat analytics tools already have AI, aiming to predict oncoming threats in advance, discovering breaches that occur and reacting to ransomware and other malware attacks. The notion of applying intelligence to cybersecurity is also nothing new, but this year every major provider of endpoint detection and response (EDR) and endpoint protection platforms (EPP) has introduced new offerings that emphasize the ability to predict or provide automated response to threats and attacks using advanced AI and machine learning capabilities.
Among those that have unveiled new threat-detection capabilities that use AI and machine learning, Cisco Systems Inc., Carbon Black Inc., Cylance Inc., CrowdStrike, FireEye Inc., IBM Corp., Kaspersky Lab, McAfee LLC, Sophos Ltd., Symantec Corp., Palo Alto Networks Inc. and Trend Micro Inc. are a few that have introduced or added machine learning capabilities or extended them.
The focus on bringing more AI and machine learning technology into all layers of the IT security stack couldn't come at a better time. The sheer volume and scope of attacks have exceeded the capacity of any number of IT security professionals, who are already in short supply. As every year winds down, it seems the list and severity of major security breaches will be difficult to top and 2017 was no exception. Ransomware attacks alone will have cost companies an estimated $5 billion this year, up from $1 billion in 2016, according to Cybersecurity Ventures, a research firm focused on IT security.
Sophisticated ransomware and malware exploits such as WanaCry, Petya, NonPetya, Nyetya, Goldeneye and others had various consequences to victims this year. Many breaches shut down their victims for days and in some cases longer, while others had to pay a huge price to make their customers whole -- or at the very least saw their brand reputations take a huge hit. Among them were Arby's, Deloitte, DocuSign, Hyatt, FedEx, Merck, Sonic, Verizon and Whole Foods, though there were many others. Add smaller organizations to the count and rarely did a day go by where someone wasn't a victim.
If the 1 billion Yahoo customer identities breached over a period of several years and disclosed last year wasn't staggering enough, this year the company revised that to all 3 billion identities. But that was a mere footnote, overshadowed by the Equifax breach, in which financial information of up to 143 Americans was exposed and amid reports of strong evidence that the Russians tried to influence the U.S. election last year.
Fighting Fire with Fire
Preventing foreigners from attempting to influence future elections has become a high national priority and now C-level execs and their boards are coming to terms with the reality that it's necessary to fight fire with fire. Many organizations are outmatched by the fact that their attackers are using advanced techniques to attack them, often based on their own use of AI and machine learning. Consequently, IT and security operations teams don't have the capacity to discover and mitigate the onslaught of attacks, meaning they must also use AI and machine learning to defend and protect their organizations' critical information.
Arguably one of the most alarming breaches to date, the Equifax breach is the result of the credit reporting provider's failure to patch a security flaw that Cisco publicized on March 8 when the company warned of a critical security flaw in Apache Struts, the open source, Java-based framework widely used on interactive Web sites. Despite reports that the flaw was "being actively exploited," Equifax's July 29 discovery that customer records were potentially stolen traces back to the fact that the flaw wasn't patched. It's not clear why the patch wasn't fixed, and while Equifax's handling of the matter extends beyond that initial failure, the fact is many organizations avoid patching because they're concerned that doing so will cause a failure, or even a systemwide outage.
That thinking needs to change, said David Konetski, VP and a technical fellow with Dell Technologies' Office of the CTO. Speaking during a mid-October panel discussion hosted by the National Cybersecurity Association (NCSA) in New York on the topic of AI and machine learning, Konetski said organizations will find that in order to keep pace with the threat and attack vectors, they'll have no choice but to automate.
"The security exposure of not automating is now starting to outweigh the paranoia of doing something wrong, pushing a button, taking down 170,000 endpoints," Konetski said. "You'd much rather have to deal with a catastrophic issue like that than have to deal with a breach. I think over the next couple of years, you are going to see a large switch to automation, which will increase the security posture of all of the customers. It's going to be a little painful, because IT departments move slow by nature."
The decisions made -- or lack thereof -- by Equifax notwithstanding, it raises the question: If the company's security operations team had applied threat- and breach-detection systems properly using AI, would it have discovered the breach, pinpointed the Struts issue and used predictive analytics to determine what impact the patch might have on the operation of the system?
Generally speaking, the existence of an isolated Apache Struts server in a large, global organization can be difficult to find from an asset management perspective, said Richard Baich, CISO of Wells Fargo Bank, who was also on the NCSA panel discussing the role of AI applied in cybersecurity, a topic of which he's a proponent.
"Organizations need to help vendors to be able to do that, to drive that innovation," Baich said. "I think the real call to action is how do you prioritize from the probability of an occurrence to understand the threats, so that it enables you to be more proactive. We are utilizing and looking at AI and machine learning to enhance our interactions and drive innovation on the internal side of the house as it relates to defining information security and moving it honestly from a proactive to a preemptive stance. Utilizing the functionality of AI or machine-related correlations could speed things using Big Data."
Microsoft's AI Push
AI and machine learning are key emphases of the new Microsoft 365 subscription offerings, which bundle Windows, Office 365 and Microsoft's Enterprise Mobility + Security (EMS) service. Overall, AI and machine learning have become key pillars in Microsoft's focus on making users and groups more productive and on enabling digital transformation. Microsoft CEO Satya Nadella started talking it up about two years ago and it has become the focal point since then. The company's progress in bringing AI into its data platforms was at the heart of Nadella's keynote at the recent Ignite conference.
"When you create such a rich data asset, what you truly enable is AI-first workloads, because with data, your ability to reason over data becomes possible, and when you have that, you can create a completely new capability that you couldn't before," Nadella said in his keynote. "Once you have this very rich data substrate, you can go one step further. You can start building AI-first business-process applications."
AI has become the root of many of the company's initiatives and Microsoft has already released services such as Azure Machine Learning and APIs for its Bot Framework, conversational computing and Microsoft Graph. Microsoft is infusing elements of machine learning and AI into other products, too, including SQL Server, Office 365 and Windows. And when referring to Azure, the company calls the business it's "Intelligent Cloud," when reporting on it to Wall Street. Nadella outlined the core of that intelligence in Azure last year, when revealing that the company has installed field-programmable gate arrays (FPGAs) and GPUs and has deployed advances in software-defined networking and storage into Azure. Speaking in October at the Sibos financial industry conference in Toronto, Nadella said in regard to AI: "We have ambitious goals there."
Those ambitious goals include applying AI to its various security platforms, which include the company's Digital Crimes Unit, its own security operations center and its rapidly growing portfolio of security software and services. It even now plays into Microsoft's secure-by-design software development lifecycle process.
Machine Learning in Windows Defender ATP
When it comes to delivering security software, Microsoft has offered various security tools over the years, such as Forefront Security and Security Essentials, among others, none of which were considered superior to most third-party alternatives, but regarded as better than nothing. Security Essentials was a malware-scanning tool that was offered as an addon for Windows. It was replaced by Windows Defender with the release of Windows 8, but most deemed it as lightweight compared with third-party tools.
When Microsoft launched Windows 10 in July 2015, it came with an improved version of Windows Defender and offered a new behavioral analysis capability to detect malware during scans. But with last year's Windows 10 Anniversary Update release, Microsoft introduced Windows Defender Advanced Threat Protection (ATP). The new offering was designed to gather telemetry from behavioral sensors built into the Windows 10 Anniversary Update and future releases. Using Microsoft's cloud-based security analytics and threat intelligence data, anonymized data gathered from other Windows devices, more than 2.5 trillion indexed URLs and reputation lookups, Windows Defender ATP taps into Microsoft's new intelligent security graph.
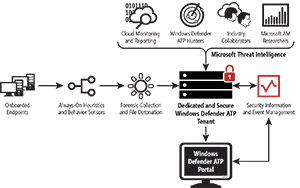 [Click on image for larger view.]
Windows Defender ATP includes agents in Windows 10 Anniversary Update and above and a security administrator's portal that gathers threat telemetry from Microsoft's cloud service.
[Click on image for larger view.]
Windows Defender ATP includes agents in Windows 10 Anniversary Update and above and a security administrator's portal that gathers threat telemetry from Microsoft's cloud service.
The service provides response recommendations based on its security operations, which include a cloud-based detonation service to run files and URLs in isolated virtual machines for deep inspection. The initial release lacked endpoint remediation tools and wasn't able to detect all attack types. In April, with Microsoft's release of the Windows 10 Creators Update, the company improved Windows Defender ATP by adding sensors to detect in-memory and kernel attacks.
Heike Ritter, a Microsoft senior product manager, speaking about Windows Defender ATP in a session at the recent Ignite conference, said that the ability to detect in-memory and kernel attacks is an important capability. "At Microsoft, we have experts in cybersecurity that are tracking nation states and attacker groups and all kind of other attackers out there in the wild in trying to understand what they are doing and especially what they are doing next," Ritter said. "A unique aspect here is, we built the operating systems, so we know each other in our team. They can just go next door and say, 'Hey, kernel team, what kind of visibility do I need to get to actually spot these kind of attacks?' And then they discuss, and they brainstorm, and then they give us the visibility that exposes them and our sensor will then look at those kind of behaviors in memory or in kernel."
Looking to bolster Windows Defender ATP, Microsoft in June acquired Hexadite, which is known for its automated incident investigation and response system. Microsoft said at the time of the announcement that it plans to add Hexadite's technology into Windows Defender ATP. With the Windows 10 Fall Creators Update in October, Microsoft further upgraded Windows Defender ATP with security analytics, support for enhanced detection capabilities in Windows 10, including Application Guard, Exploit Guard and script introspection, support for the Windows Security Graph APIs, and support for Windows Server.
The Windows 10 agents are embedded on the Pro, Education and Enterprise editions. Windows Defender ATP is licensed as a key component of the new Microsoft 365 package, which includes EMS and Office 365 subscription, and requires E5 licenses. Security administrators can centrally manage the security lifecycle of employee devices from the Windows Defender ATP console, which provides detections and the ability to investigate across devices, identity and information assets.
The October update to Windows Defender ATP is important because it integrates with Office 365 ATP and Microsoft Advanced Threat Analytics (ATA), the on-premises solution designed to protect datacenter resources from advanced, targeted attacks and insider threats. It gathers event data from various sources including logs, network telemetry and behavioral profiles it creates. It also gathers information from third-party security and event information management (SEIM) systems, Windows Event Forwarding and the Windows Event Collector to detect suspicious activity. The company recently released an updated version of Microsoft ATA (see "Advanced Detection").
970 Million Malicious Events Per Day
With the fall release, Windows Defender ATP also now includes access to the APIs, letting organizations integrate it with other systems. So where does machine learning and AI come into play with Windows Defender ATP? Nathan Burke, Hexadite's VP of marketing, who co-presented with Microsoft's Ritter during the Ignite session, noted that Windows Defender ATP now processes 970 million malicious security events per day from across the entire Microsoft enterprise and consumer ecosystem. "Now that to me is a staggering number, and really what it does is it just shows the magnitude of the threats and the attacks out there," Burke said.
The magnitude is why machine learning has become a prerequisite, he added. "Visibility just isn't enough anymore, it's only half the battle," he said. Noting public estimates that there are 1 million cybersecurity positions that are unfilled because of a shortage of those with adequate skills, "You have too many alerts and not enough people," he said. "Until recently, the only thing that organizations could do is prioritize. They would assign a score to every alert they had, and it's certainly better than nothing. But, when you think about it, if something's an 80 versus a 79, is there a material difference there in what you would do? And if so, the other piece of it is, when you really think about prioritization, it's really just a conscious decision about what you're willing to ignore, for better or for worse. And so, really, what does that leave you with? And it's pretty much this: People in organizations are constantly trying to recruit cyber analysts to spend all day long, really doing manual repetitive work."
Burke pointed to a survey conducted by consulting firm Enterprise Management Associates (EMA) that determined 92 percent of organizations receive more than 500 alerts per day from their intrusion detection systems, and 88 percent who see more than 500 daily alerts classified them as either critical or severe. Because these organizations don't have enough people, it means that fewer than 1 percent of the alerts are ever investigated, Burke said. "Put that together and you see there's a big problem and the math doesn't work."
Will AI Take Away Jobs?
And that's why Burke and others say automation using machine learning is necessary. "When you're able to use automation and move beyond human scale, you're then able to say: 'All right, based on what we've learned here, how do we apply that elsewhere on the network? How do we find things that are common and look like what I've just found, and then how do we keep going? How do we spawn additional parallel investigations until we find nothing else?' And I think that is the key to automation, that you're just not going to be able to get with people."
In every conversation about automation, Burke points to the inevitable elephant in the room that many prospects bring up: the fear that AI will take away their jobs and eliminate the need for their staffs. "One of our customers said this, which is: 'Security automation is preventing people from doing a machine's job.' I think that's exactly right. It kind of flips it on its head because automation does help to take away that manual repetitive work, and it gets rid of the things that machines will always do better than people, so that people can do things that people will always do better than machines."
Next-generation anti-virus protection requires accurate labels from expert analysis applied by human cybersecurity analysts to accurately train performant models, according to a Microsoft white paper describing Microsoft ATA. Ritter demonstrated how Windows Defender ATP could gather an alert and correlate it against other alerts and patterns, helping the analyst make a decision on how to act on it and whether further investigations are necessary. "Let the machines do what they do better, but let the analysts really focus on their work," she said. "There are so many threats happening that really need analysts to look at that can't just be automated. Also, they can invest more time in their strategic work."
Microsoft ATA protects an average of 4,500 other malicious samples using machine learning, according to Microsoft. This analysis and data from the Microsoft Security Intelligence Graph amplifies protection using machine learning, automation and behavioral analysis. Microsoft claims that an average manual investigation with Windows Defender ATP augments protection against similar threats to 12,000 customers.
Even security vendors such as Sophos, which earlier this year stepped up its efforts to apply machine learning with the acquisition of Invincea, say automation is critical but not a replacement for human expertise and decision making. "As we build better and better tools, all we are doing is getting rid of the noise, so there is more signal for the humans to defend against more persistent attackers," says Sophos Principal Research Scientist Chester Wisniewski. "The tools are only good at automating so much of it away. It requires a lot of human effort to defend an organization, as well. If you look at some of the major breaches this year, Equifax, Deloitte and others that made big headlines, all of those organizations were compromised for months if not a year or more. That's quite common, and the reason is the tools did not find those breaches. You need the humans to be part of that process."
Is Windows Defender ATP a Threat?
While critics argue that Microsoft providing security for its own software and service is the equivalent of letting the fox in the henhouse, others laud some of the recent advances the company has made. While Sophos' Wisniewski hasn't looked at Windows Defender ATP, he doesn't believe Microsoft will displace third-party malware and threat-detection and remediation offerings. "This is their fifth or sixth stab at trying to do something useful in security and they still haven't gotten there," he says. However, Wisniewski allows Microsoft has made significant progress at improving the security of its platforms, notably Windows.
"They have done really great things with Windows 10 from a mitigation standpoint," he says. "Microsoft understands the problem really, really well. The problem with Microsoft, of course, is they have literally the world's largest target painted on their back. Anything they do, the criminal considers the bare minimum they have to defeat in order to be successful at all because every Windows computer is going to potentially have the bare minimum from Microsoft. It's going to have Defender and now it has this new anti-ransomware in the Fall [Creators] Update, so if the criminal can't get past those, they are useless. Sadly, I don't think Microsoft can win that battle."
Nadella sees it as Microsoft's duty to raise the bar on security, now more than ever. "It's sort of the topic of our times," he said during his Sibos talk. "Clearly, we are the first responders, and we have tremendous responsibility in doing a lot of things right," Nadella said. "One is making sure we build secure software but more importantly the cybersecurity operational posture that we have is helpful in making sure that your endpoint, as well as your digital estate that's in our cloud, is protected and then sharing that intelligence broadly."