Windows Server How-To
How To Work with Hyper-V Checkpoints
Here's a quick breakdown on how to roll back to an earlier Windows Server 2012 R2 Hyper-V checkpoint.
Occasionally you may need to perform administrative actions that are potentially dangerous (such as a registry modification or an Active Directory schema extension). In these types of situations, you can give yourself a bit of a safety net by using Hyper-V checkpoints. Checkpoints are a feature of Windows Server 2012 R2 Hyper-V that allow you to roll a virtual machine back to a previous state.
Creating a checkpoint is a very simple process. Before you perform the potentially dangerous administrative action, right click on the virtual machine and choose the Checkpoint command from the shortcut menu, as shown in Figure 1.
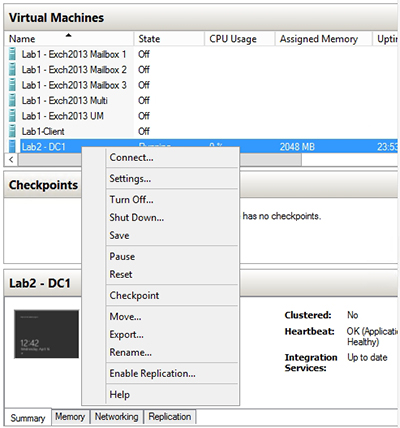 [Click on image for larger view.] Figure 1. Right click on the virtual machine and choose the Checkpoint command from the shortcut menu.
[Click on image for larger view.] Figure 1. Right click on the virtual machine and choose the Checkpoint command from the shortcut menu.
When Hyper-V finishes creating the checkpoint the checkpoint will appear in the list of checkpoints beneath the virtual machine, as shown in Figure 2.
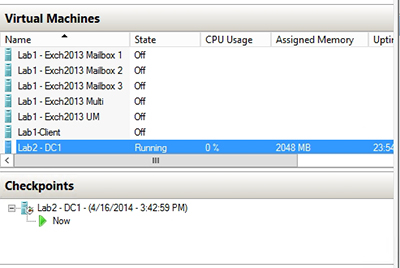 [Click on image for larger view.] Figure 2. The checkpoint has been created.
[Click on image for larger view.] Figure 2. The checkpoint has been created.
Once the checkpoint has been created, you can perform whatever administrative action you needed to do. If the administrative action is successful, you should delete the checkpoint upon completion. Checkpoints degrade read performance for the virtual machine, so you don't want to leave unnecessary checkpoints in place. You can get rid of an unwanted checkpoint by right clicking on the checkpoint and choosing the Delete Checkpoint command from the shortcut menu, as shown in Figure 3. If you have an entire series of checkpoints that you need to remove, you can save time by using the Delete Checkpoint Subtree command instead.
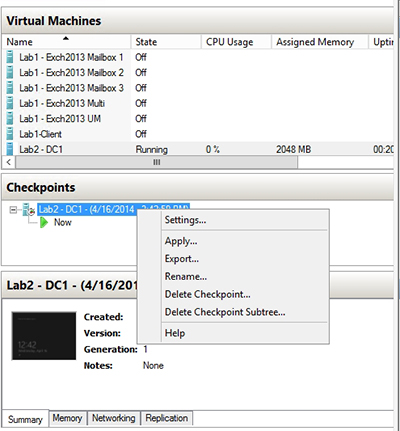 [Click on image for larger view.] Figure 3. Right click on the Checkpoint and choose the Delete Checkpoint command from the shortcut menu.
[Click on image for larger view.] Figure 3. Right click on the Checkpoint and choose the Delete Checkpoint command from the shortcut menu.
If on the other hand, something goes horribly wrong and you need to revert the virtual machine to a previous state then you can right click on the checkpoint and choose the Apply command from the shortcut menu. When you do, Windows will offer you the opportunity to create another checkpoint before applying the checkpoint. That way you can "undo" the application of the checkpoint if necessary. I recommend shutting down the virtual machine prior to applying a checkpoint.
As you can see, it is very easy to create and use Hyper-V checkpoints. Even so, checkpoints are not appropriate for every situation and it is important to understand the implications of using a checkpoint before doing so.
The first thing that you need to understand is that a checkpoint is different from a backup. When you create a checkpoint, what you are really doing is creating a differencing disk and flagging the virtual machine's original virtual hard disk as read only. This means that you are not creating a copy of the virtual hard disk, and checkpoints therefore do not protect you against hard disk failures or storage corruption.
Another thing that you need to understand is that checkpoints are sometimes affected by other servers on your network. Suppose for a moment that you created a checkpoint of a virtualized domain controller before applying a schema extension. Now, imagine that the schema extension was done incorrectly and you need to revert the Active Directory to its previous state.
You could apply the checkpoint, but doing so will only give you the desired results if the checkpoint resides on the only domain controller in the entire domain. If there are other domain controllers in the domain then the Active Directory Replication Service will become an issue. After you apply the checkpoint, the other domain controllers will see the recently reverted domain controller as being outdated. The Active Directory Replication Service will seek to bring that domain controller up to date by replicating all of the Active Directory modifications that have occurred since the time that the checkpoint was created. This includes the unwanted schema extensions. That being the case, you are better off using a traditional backup for your domain controllers (rather than relying on checkpoints) and using an authoritative restoration if necessary.
Similarly, you must not use checkpoints for virtual machines that are running applications that maintain state data in memory (such as Exchange Server). Checkpoints do not capture memory contents and applying a checkpoint of such a virtual machine will typically result in data loss or application corruption. If you need to create checkpoints of these types of virtual machines, the only way to do so safely is to create the checkpoint while the virtual machine is shut down.
As you can see, checkpoints can be a handy feature, but they can also cause problems unless you fully understand the implications of using them.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.