Product Reviews
Review: Cyber-Ark Privileged ID Management Suite
The suite manages to win over our reviewer despite his cynical view of network-management tools.
As an organization grows in size, managing passwords within the organization becomes increasingly more difficult. I'm not talking about the challenge of managing user passwords. After all, the passwords for end users are managed in roughly the same way in both large and small organizations.
But this is not the case for privileged accounts. In larger organizations, it can be extremely difficult to ensure that the passwords for privileged accounts are changed according to the corporate security policy. This can be especially true for the local administrative account on users' workstations. This account is frequently neglected, which can lead to a major security threat.
Another major challenge associated with managing privileged accounts is monitoring the ways in which they're used. If an organization is serious about security, then its IT professionals need to know who uses a privileged account and why.
These are just some of the challenges that Cyber-Ark Software Ltd. has set out to solve with its Privileged Identity Management (PIM) Suite. I decided to take the software suite for a test drive and see whether or not I thought it would be beneficial to network administrators in an enterprise environment. For the purpose of this review, I used version 6.0 of the PIM Suite.
Deploy and Configure
Normally when I write a software review, I like to work through the initial deployment and configuration process. That way, I can get a feel for how well the software integrates into my existing lab environment. In this particular case, however, I didn't have the opportunity to deploy the software from scratch -- instead, a representative from Cyber-Ark provided me with access to several pre-configured servers running in a cloud environment.
The Password Vault
Here's a bit of background information about how the Cyber-Ark password vault works. Essentially every managed account is assigned a policy and a safe. A policy is a set of rules that facilitates password management. The policy controls how often the password should be changed, who has access to the account and so on.
A safe is a logical container for storing passwords. Safes are typically created based on who will need access to the privileged accounts whose passwords will be stored within the safe. For instance, you might create a safe for a business unit or for a group of administrators. The safes are collectively referred to as the vault.
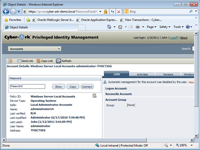
[Click on image for larger view.] |
| Figure 1. The requested password was retrieved from the vault. |
Accessing a Password
The first thing I wanted to try was to gain access to a password that had been stored in the password vault. This is important because the passwords for privileged accounts need to be changed frequently, and it's entirely possible that several password changes may have occurred since the last time an administrator needed to use a privileged account. Therefore, when an administrator needs to use a privileged account, he needs a way of finding out what the current password for that account is.
For this test, I logged on as a regular user (who had been given permission to access the administrative account) and opened the Web-based PIM Suite Console. The user account was automatically authenticated into the vault, and the console displayed the objects that the user had accessed most frequently. With that, I clicked on the local administrator account for one of the PCs on the network and then clicked the Show button. Upon doing so, the requested password was retrieved from the vault and displayed for 10 seconds. The Activities tab showed who had retrieved the password and when.
Although it's possible for a user to look up a password, it's also true that you may not want to disclose the password to all administrators. In a large organization, there are often different levels of administrative responsibilities. For example, one admin might be in charge of installing and maintaining software, while another administrator might be in charge of Active Directory management. If an administrator has a limited set of job responsibilities, then it doesn't make sense to provide him with the credentials to an account that has virtually unlimited capabilities.
But there may be times when administrators need to use a privileged account to perform a specific task that's within the realm of their job responsibilities. Thankfully, the Cyber-Ark software allows a user to temporarily use a privileged account without ever knowing the account password.
When I first attempted to connect using this account, I wondered why Cyber-Ark would design a policy that would prevent me from exposing a password, but that would still allow me to use the account. After all, if I can readily use the account, then I really don't need to know its password.
As it turns out, clicking on the Connect button doesn't automatically grant you access to the privileged account. Instead, clicking the Connect button brings up another screen, which lets you request temporary access to the account.
There's a drop-down at the top of the screen that allows you to provide a reason for using the account. This list can be pre-populated so that different administrators can use the account for different reasons. For example, you might allow an administrator to use an account only for installing applications, installing patches or making configuration changes.
This screen also allows an administrator to state for how long he'll need access to the account. This keeps the administrator from receiving indefinite access. At the bottom of the screen is a place where you can enter a reference number. Such a number might correspond to a help desk ticket number. There's also a check box that can be selected if the administrator is performing an emergency operation.
In my opinion, this screen was extremely well thought out. I like that it requires the person who's requesting use of the account to explain exactly why the account is being used and specify for how long he will need access to the account. Such information makes it easy to determine who performed an action using a privileged account and why. Requiring administrators to provide such information before accessing privileged accounts may also help to deter rogue administrators who might have planned to use the account for unscrupulous purposes.
It's worth noting that, when the administrator fills out this screen, he isn't instantly given access to the account (unless the policy provides for immediate access). Instead, the
Cyber-Ark software sends an e-mail message to a designated person who makes a decision as to whether or not to grant the request based on the information that has been provided.
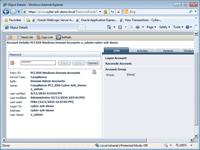
[Click on image for larger view.] |
| Figure 2. You can allow a user to use a password without actually exposing the password. |
Bulk Password Changes
Often, one of the most significant problems organizations face is when an administrator leaves, exposing the organization to numerous security threats. The administrator has an intimate knowledge of the organization's network infrastructure and security procedures. Even if you delete or disable the employee's account when he leaves, there's a good chance that he knows other passwords. He may know the domain administrator password, and he probably knows some service account passwords (which can be almost as powerful as administrator passwords).
One of the Cyber-Ark PIM Suite features that can help with situations like this is the ability to change passwords in bulk. Cyber-Ark makes it possible to change all of the passwords that the user knows -- and change them all at the same time.
I decided to try this feature out by seeing if I could locate all of the administrator accounts across the entire organization, and change the passwords for those accounts in bulk.
I was especially interested to see if I could change both domain admin account passwords as well as the passwords for the local administrator accounts on the individual workstations. Local administrator account passwords are seldom changed in the real world and represent a significant security threat.
Accomplishing the bulk password change proved to be easier than I thought it would be. All I had to do was open the PIM Suite Console and enter the word "administrator" into the search box. When I did, the console displayed 40 different accounts that fit my search criteria. From that point, resetting the passwords was just a matter of clicking the Select All link, followed by the Change button.
| REDMOND
RATING |
Installation:
20% |
NA |
Features:
20% |
10.0 |
Ease of Use:
20% |
8.0 |
Administration:
20% |
10.0 |
Documentation:
20% |
9.0 |
Overall
Rating: |
9.25 |
Key: 1: Virtually inoperable or nonexistent 5: Average, performs adequately 10: Exceptional
|
|
|
Overall Assessment
I've been a network administrator for more than two decades, and during that time I've seen many different third-party applications that are designed to provide easier or more comprehensive network management. Although there are some good network-management products out there, I've developed something of a cynical attitude toward network-management products in general. That's because I've seen so many different management products that come with a big price tag, but don't seem to offer any real benefit. Often the management products that are beneficial end up being so complicated that they ultimately prove to be counterproductive.
I didn't know what to expect when I set out to review the Cyber-Ark PIM Suite. But the software goes a long way toward helping organizations deal with some serious security vulnerabilities that exist on most networks (such as local administrator passwords that are never changed). The software's auditing and reporting capabilities will be useful to anyone who needs to maintain an administrative paper trail for compliance purposes.
Privileged Identity Management Suite
Pricing starts at $15,000
Cyber-Ark Software Ltd.
888-808-9005
cyber-ark.com